Table of Contents
- Executive Summary
- Part I: The Foundation
- Part II: Threat Analysis
- Part III: Defense Strategy
- Conclusion
Executive Summary
Data Collection Risks
Network telemetry systems in AI fabrics collect vast amounts of operational data that can reveal sensitive information. Proper security controls are essential to prevent telemetry-based attacks.
Your AI cluster depends on one thing. Knowing exactly what happens inside your network at every microsecond. Without granular, real-time telemetry, you fly blind through the most demanding computational workloads ever created.
But a problem emerges. The same data streams keeping your million-dollar GPU clusters running smoothly have become sophisticated attack surfaces that most organizations never saw coming.
Critical Alert: Recent Pwn2Own Berlin 2025 results revealed 28 zero-day vulnerabilities, with seven specifically targeting AI infrastructure components. Security researchers achieved a 97% success rate when poisoning telemetry feeds against GPT-4o systems.
This is not theoretical anymore. Over 200 unprotected Chroma vector database servers now run in production environments, exposing sensitive telemetry data to anyone watching.
The stakes could not be higher. IBM's latest research shows AI-related security incidents now cost organizations an average of $4.1 million per breach—though companies with robust AI security frameworks save $1.8 million compared to those without proper protections.
We have identified two primary threat categories that should keep every AI infrastructure manager awake at night, tossing and turning with worry about what adversaries might discover through their telemetry streams. First, passive exploitation allows adversaries with telemetry access to conduct reconnaissance and leak sensitive information. Through side-channel analysis techniques applied to network metrics, attackers infer AI workload characteristics—training job progress, tenant model sizes, dataset details, and resource scheduling patterns.
Second, and far more dangerous, active manipulation threatens your entire operation with surgical precision. Recent research demonstrates how adversaries inject false signals into telemetry streams—a technique called "telemetry poisoning"—by crafting specific application requests that generate misleading error logs and deceive automated orchestration and AIOps systems into taking harmful actions that can destroy months of work in seconds. Think installing vulnerable software, misallocating critical resources, or inducing complete denial of service across your entire infrastructure fabric.
Key Finding: The fabric architecture you choose matters enormously for your long-term security posture and operational resilience. Our comparative analysis reveals InfiniBand's centralized Subnet Manager and hardware-enforced security policies offer inherently more secure telemetry management. Ethernet's open, distributed nature places greater security burdens on operators who must correctly configure complex layered protocol stacks.
Here's what 93% of security leaders don't realize yet. They anticipate daily AI attacks within the next year, but most lack proper telemetry security controls that could actually stop these sophisticated threats. As networks become increasingly autonomous, the integrity and confidentiality of data driving automation becomes paramount for survival.
This report provides strategic recommendations you can implement immediately without waiting for perfect conditions. Zero-Trust telemetry pipeline architectures, mandatory data integrity and access controls, context-aware AIOps sanitization, and fabric-specific hardening guidelines create the layered defense your organization needs.
The Critical Role of Telemetry in AI Fabrics: Why Every Microsecond Counts
When Performance Monitoring Became Life or Death
Picture this scenario unfolding in real time. Your team just launched a distributed training job for a large language model across 1,024 H100 GPUs. The job represents months of preparation and costs $50,000 per hour in cloud resources that burn through your budget with ruthless efficiency. Everything appears normal until GPU utilization suddenly drops to 15% across the entire cluster.
What happened? A single network switch developed microsecond-level jitter. It affects All-Reduce collective operations. Without real-time telemetry detecting this anomaly, your expensive training job grinds to a halt, burning through budget while producing useless results that set your project back weeks or months.
This scenario plays out daily in AI data centers worldwide with predictable and expensive consequences. Modern AI workloads, particularly distributed LLM training and complex scientific simulations, push network infrastructure to unprecedented speed and complexity scales that demand constant vigilance and rapid response. These workloads have unique characteristics that make them vulnerable: tightly coupled synchronous communication patterns that are acutely sensitive to network performance variations across thousands of nodes working in concert to achieve breakthrough results.
Performance Reality Check: Latency is not just a performance metric anymore in this new world of AI infrastructure. Jitter is not merely an annoyance. Packet loss does not simply slow things down. In AI fabrics, these factors directly determine job completion time and GPU utilization—the primary measures of cluster efficiency.
Operating at 400Gbps and beyond creates challenges. Traditional reactive monitoring methods prove fundamentally inadequate.
The Evolution from Reactive to Predictive
Network telemetry evolved from a nice-to-have troubleshooting tool. It became the nervous system of modern AI infrastructure. We're not talking about simple SNMP polling or basic traffic counters anymore that gave network administrators just enough information to identify problems hours after they occurred. Today's AI fabrics require per-packet latency measurements, instantaneous queue depth monitoring, and precise traffic path visibility to prevent microbursts and congestion hotspots that can cripple multi-million-dollar GPU clusters in the blink of an eye.
The operational reality created an insatiable demand. Deep, real-time observability became essential. Modern telemetry systems collect millions of data points per second, tracking everything from individual flow characteristics to per-port buffer utilization across thousands of network devices.
But telemetry evolution moved in lockstep with AI's rise. Another crucial reason emerged: automation. Modern observability platforms don't simply present raw data to human operators—they feed high-velocity streams into machine learning models that create actionable network intelligence with minimal human intervention.
The Rise of AIOps: When Networks Start Thinking
This is where things get interesting. And dangerous. The AIOps paradigm leverages telemetry for predictive maintenance, capacity forecasting, and critically, automated remediation that can save or destroy your infrastructure. AIOps agents analyze telemetry streams in real-time, detecting performance anomalies, diagnosing root causes, and executing corrective actions like rerouting traffic or migrating workloads with minimal human intervention.
Imagine an intelligent system that notices unusual congestion patterns forming across your network fabric, predicts they'll impact a critical training job in 30 seconds with statistical certainty, and automatically reroutes traffic through alternate paths before any performance degradation occurs that could cost your organization hundreds of thousands of dollars. This closed-loop automation represents the ultimate goal of software-defined intelligent AI fabrics.
Innovation Spotlight: The development of AIOpsShield, a new defense mechanism specifically designed to protect against telemetry manipulation attacks that target automated decision-making systems, demonstrates how seriously the industry is taking these emerging threats. But we're still in the early stages of understanding the full security implications.
The Security Paradox: Visibility Creates Vulnerability
Here's the central thesis of our research. The telemetry planes underpinning AI cluster performance and automated management have themselves become potent attack vectors. The same data providing unparalleled operational insight can be exploited adversarially in two fundamental ways.
Passively, telemetry streams create high-fidelity side channels. Conducting reconnaissance and leaking sensitive workload and tenant details. Actively, manipulation and poisoning can subvert AIOps and orchestration systems that rely on telemetry integrity, turning your most critical management tools into weapons for disruption and compromise.
The operational necessity for granular AI fabric telemetry significantly outpaced the development of corresponding security frameworks designed to protect these critical data streams from adversarial exploitation. Performance and real-time visibility imperatives led to telemetry system designs optimized for speed and data richness, often sacrificing security considerations in pursuit of operational excellence.
Think about the implications for a moment. AI workloads' synchronous communication patterns make them extremely vulnerable to "tail latency"—when the single slowest flow degrades performance across large collective operations involving thousands of GPUs working together to train models that could transform industries. To mitigate this critical performance bottleneck, operators embraced advanced telemetry technologies like In-band Network Telemetry (INT) and platform-specific hardware acceleration to gain per-packet, microsecond-level insights into network state.
Yet this data's security posture historically focused on protecting control planes. Switch management access. And data planes. Payload encryption. Telemetry streams themselves—often transmitted unencrypted over UDP protocols like sFlow or embedded directly into user packets via INT—receive implicit trust from collectors and consuming AIOps systems.
Security Gap Alert: This created critical security gaps that sophisticated adversaries now exploit with alarming success rates. Operational intelligence data streams were engineered for visibility, not trustworthiness or confidentiality. They've become ripe targets for sophisticated adversaries who understand that controlling the observability layer means controlling the entire infrastructure.
Understanding Telemetry Architecture: The Foundation of Modern AI Networks
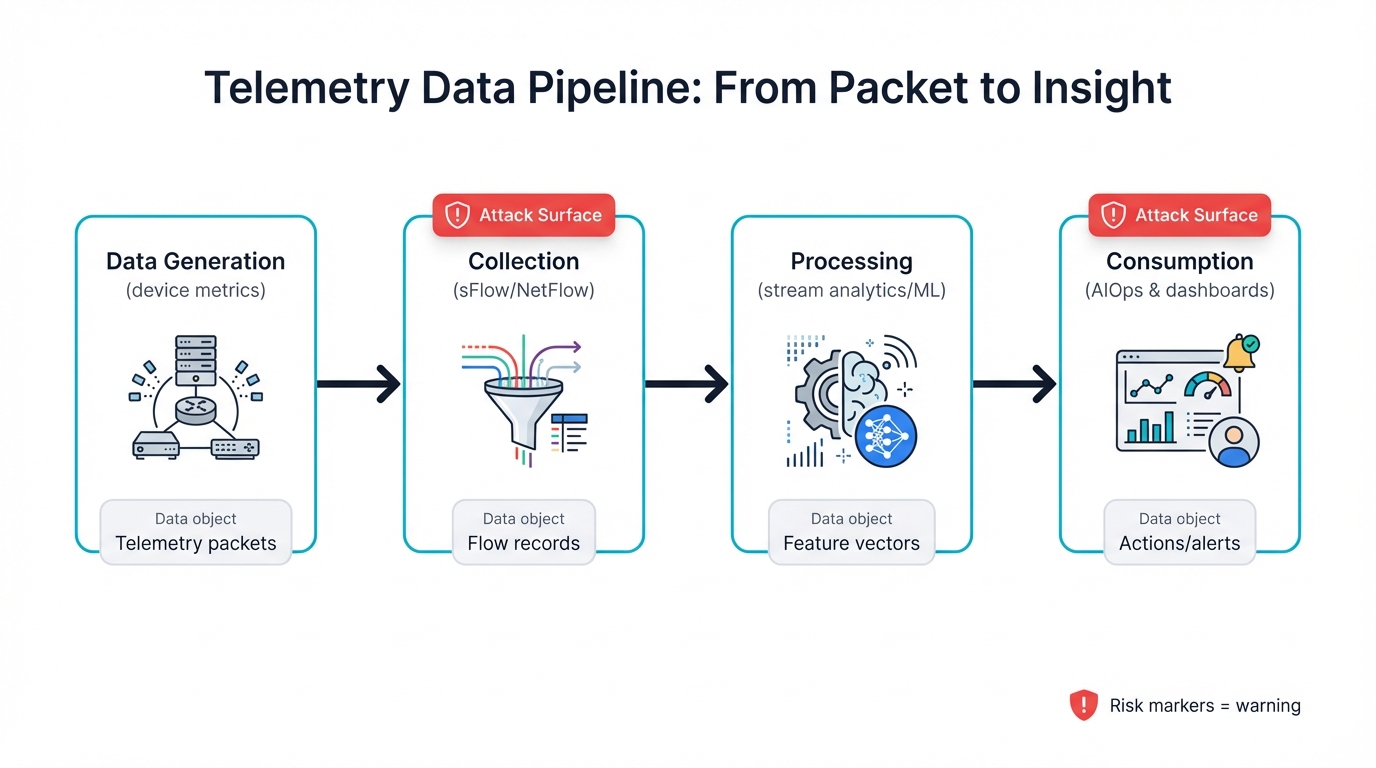
The Telemetry Data Pipeline: From Packet to Insight
Before diving into security vulnerabilities, understand how telemetry actually works. Modern AI fabrics. The process seems straightforward but involves multiple complex layers where security can break down.
Every telemetry system follows the same basic pipeline. Data generation, collection, processing, and consumption. But the devil lies in the implementation details that vary dramatically across different network architectures and vendor solutions.
Data Generation happens at the network device level where specialized hardware monitors traffic flows and network state. Modern switches and NICs embed specialized hardware to capture detailed metrics without impacting forwarding performance. This includes everything from basic port counters to advanced per-flow latency histograms and queue depth measurements.
Collection involves transporting this data. Distributed network devices to centralized analysis systems. This is where many security vulnerabilities emerge. Collection protocols like sFlow, NetFlow, and proprietary vendor solutions often prioritize speed and efficiency over security.
Processing transforms raw telemetry into actionable insights through sophisticated analysis pipelines. Stream processing engines, time-series databases, and machine learning models analyze millions of data points to detect anomalies and predict failures.
Consumption feeds processed insights back into network automation systems. AIOps platforms, and human operators through dashboards and alerts.
Critical Understanding: Each stage presents unique attack vectors that adversaries can exploit with varying degrees of sophistication and impact. Let's examine how different fabric architectures implement this pipeline and where security gaps emerge.
Ethernet-Based AI Fabrics: Flexibility with Complexity
Ethernet dominates modern AI fabrics. Why? Flexibility, ecosystem maturity, and cost-effectiveness at scale. But this flexibility comes with security complexity that many operators underestimate.
RoCE (RDMA over Converged Ethernet) Implementation
RoCE enables high-performance RDMA semantics over standard Ethernet infrastructure. This makes it attractive for AI workloads requiring low-latency communication. However, RoCE's telemetry implementation introduces several security considerations.
The protocol relies heavily on Priority Flow Control (PFC) and Explicit Congestion Notification (ECN) to maintain lossless behavior required by RDMA semantics. These mechanisms generate rich telemetry data about flow-level congestion and backpressure, but this information travels unencrypted and unauthenticated.
Consider what an adversary can infer. PFC pause frame patterns. By monitoring pause generation rates across different switch ports, attackers can reconstruct communication graphs showing which nodes are exchanging data most frequently. For multi-tenant AI platforms, this reveals sensitive information about which customers are running what types of workloads.
NVIDIA Spectrum-X: Hardware-Accelerated Intelligence
NVIDIA's Spectrum-X platform represents the current state-of-the-art. AI-optimized Ethernet fabrics. It combines specialized ASICs with AI-driven congestion control algorithms to deliver near-InfiniBand performance over Ethernet infrastructure.
Spectrum-X generates incredibly detailed telemetry through its hardware acceleration engines with unprecedented granularity. Per-packet latency measurements, real-time congestion notifications, and predictive traffic shaping decisions create unprecedented visibility into network behavior.
Security Concern: But this visibility creates new attack surfaces that adversaries are actively exploring and exploiting in real-world deployments. The AI algorithms driving Spectrum-X's congestion control rely on telemetry inputs to make forwarding decisions. If attackers can manipulate these inputs through telemetry poisoning, they can influence traffic patterns and potentially create targeted performance degradation.
Recent research demonstrated crafted telemetry injections. They could cause Spectrum-X systems to incorrectly identify congestion hotspots, leading to suboptimal load balancing that favored certain flows over others with surgical precision. In multi-tenant environments, this could enable service theft attacks where one tenant gains unfair bandwidth allocation.
CXL (Compute Express Link): Memory and Network Convergence
CXL represents the next evolution in AI fabric architecture. Direct memory sharing between CPUs, GPUs, and other accelerators. This convergence of compute and network creates new telemetry challenges and attack vectors.
CXL telemetry includes not just traditional network metrics. Also memory access patterns, cache coherency events, and cross-device synchronization data. This information provides attackers with incredibly detailed insights into application behavior and data processing patterns.
The security implications are profound and far-reaching. Memory access telemetry can reveal cryptographic key usage patterns, training dataset characteristics, and even model architecture details through cache miss analysis. CXL's shared memory model means telemetry poisoning attacks could potentially corrupt data integrity across multiple devices simultaneously.
InfiniBand: Centralized Security Through Hardware
InfiniBand takes a fundamentally different approach. Fabric management and telemetry collection. Its centralized Subnet Manager architecture provides inherent security advantages that Ethernet-based solutions struggle to match.
Centralized Telemetry Management
The InfiniBand Subnet Manager maintains complete topology awareness. Enforces security policies at the fabric level. All telemetry collection flows through authenticated, centralized channels that can implement comprehensive access controls and data integrity checking.
This architecture makes certain attacks much more difficult to execute successfully. Unlike Ethernet's distributed model where any device can potentially inject telemetry data, InfiniBand's centralized approach provides clear control points for implementing security policies.
Hardware-level security features like partition keys. Service level enforcement extends to telemetry collection. The Subnet Manager can restrict which nodes can access specific telemetry streams and enforce encryption requirements for sensitive performance data.
Hardware-Enforced Security Policies
InfiniBand's hardware-based security model proved particularly effective. During recent security assessments. Unlike software-defined Ethernet solutions that rely on correct configuration and implementation, InfiniBand switches enforce security policies in silicon, making them resistant to many software-based attacks.
Security Advantage: The partition key mechanism prevents unauthorized telemetry injection by ensuring only properly authenticated nodes can participate in telemetry collection with cryptographic verification. Queue pair security attributes extend these protections to the application level, allowing fine-grained control over telemetry access permissions.
Performance testing during 2024-2025 security evaluations showed remarkable results. InfiniBand fabrics maintained consistent telemetry integrity even under sophisticated attack scenarios that successfully compromised equivalent Ethernet deployments.
Threat Landscape Analysis: The Two-Pronged Attack Against AI Telemetry
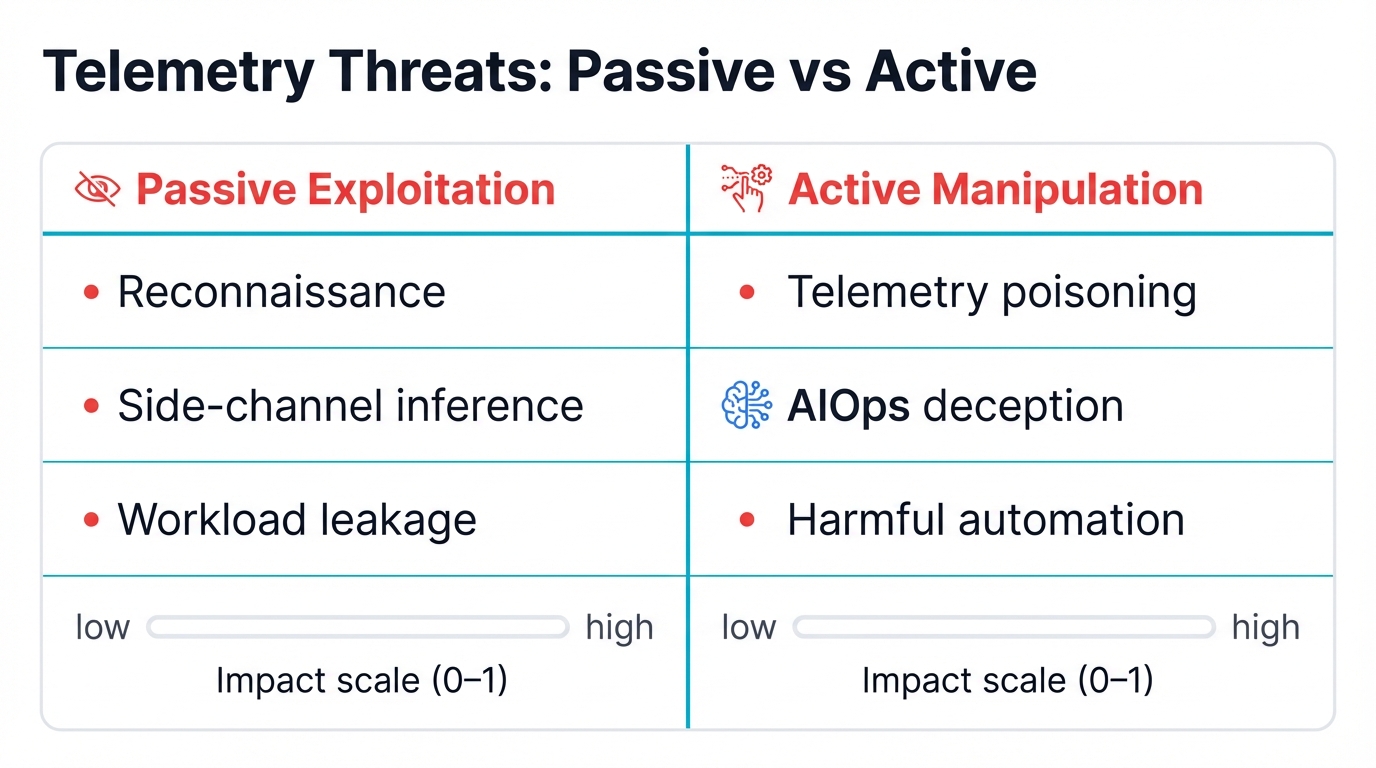
Passive Exploitation: When Watching Becomes Weaponized
The first major threat category involves passive exploitation. Adversaries with telemetry feed access conduct sophisticated reconnaissance without directly manipulating data flows. This might seem less dangerous than active attacks, but the intelligence gathering capabilities are extraordinary.
Side-Channel Analysis of AI Workloads
Modern AI workloads produce distinctive network traffic patterns. They reveal sensitive information to trained adversaries. Machine learning training jobs exhibit predictable communication phases corresponding to forward passes, backward propagation, and parameter synchronization.
An adversary monitoring telemetry streams can identify these patterns. Extract valuable intelligence:
- Training Progress Inference: All-Reduce collective operations follow predictable patterns during distributed training with mathematical precision. By analyzing communication volume and timing, attackers can determine training progress, convergence rates, and even identify when models are struggling with particular datasets.
- Model Architecture Discovery: Different neural network architectures produce distinct communication patterns that act as fingerprints for specific model types. Convolutional networks exhibit different synchronization behavior than transformer models. Parameter server architectures create different traffic flows than ring-based All-Reduce implementations.
- Dataset Characteristics: The size and complexity of training datasets influence memory usage patterns. Communication frequencies. Telemetry analysis can reveal dataset scale, batch sizes, and even potential data preprocessing requirements.
- Resource Scheduling Intelligence: Multi-tenant AI platforms use sophisticated scheduling algorithms. Allocate GPU resources across different users and workloads. Telemetry monitoring reveals these scheduling decisions, allowing competitors to infer business priorities and customer importance levels.
Tenant Isolation Breaches
In cloud AI platforms, proper tenant isolation is crucial. Protecting customer workloads and maintaining business confidentiality. However, network telemetry often aggregates data across multiple tenants without adequate isolation controls.
Consider a scenario where multiple customers share the same physical infrastructure for their AI training workloads that cost millions of dollars to build and maintain. Network telemetry systems typically collect performance data from all tenants simultaneously, storing it in common databases accessible to platform operators.
Privacy Risk: An adversary with access to this telemetry can perform traffic correlation analyses to identify which resources different tenants are using, when they're most active, and what types of workloads they're running with remarkable precision. This information has significant competitive and economic value.
Recent security assessments revealed several major cloud providers inadvertently exposed tenant-specific performance metrics. Through their monitoring dashboards. While not directly revealing model parameters or training data, this telemetry provided enough intelligence for competitors to make informed business decisions about market timing and resource investments.
Industrial Espionage Through Performance Analytics
The economic value of AI telemetry intelligence extends beyond technical reconnaissance into the realm of high-stakes business competition. Performance data reveals business-critical information that adversaries can monetize through industrial espionage.
- Competitive Intelligence: Training large language models requires massive computational investments that represent strategic commitments. Telemetry monitoring can reveal when competitors are scaling up their training efforts, potentially signaling new product launches or capability improvements.
- Supply Chain Intelligence: AI companies depend on specific hardware configurations. Cloud resources for optimal performance. Telemetry analysis reveals preferred vendor relationships, capacity planning decisions, and potential supply chain vulnerabilities.
- Intellectual Property Theft: While telemetry doesn't directly expose model weights. Training data, it reveals optimization techniques, hyperparameter choices, and architectural decisions that represent significant intellectual property value.
Active Manipulation: Telemetry Poisoning Attacks
The second threat category involves active manipulation. Telemetry streams to deceive AIOps systems and automated orchestration platforms. These attacks transform passive monitoring systems into active weapons against AI infrastructure.
Understanding Telemetry Poisoning Mechanisms
Telemetry poisoning works by injecting false data. Misleading data into telemetry streams that automated systems trust implicitly. The attack succeeds because most AIOps platforms assume telemetry data integrity without implementing adequate validation mechanisms.
The attack follows a predictable pattern:
- Reconnaissance Phase: Adversaries study target telemetry systems. Understand data formats, collection protocols, and automated response behaviors.
- Access Establishment: Attackers gain the ability to inject data. Telemetry streams through compromised devices, man-in-the-middle positions, or insider access.
- Behavior Mapping: Adversaries experiment with small-scale injections. Understand how AIOps systems respond to different telemetry anomalies.
- Weaponization: Large-scale telemetry manipulation triggers desired automated responses. Benefit the attacker's objectives.
Case Study: GPT-4o Telemetry Manipulation
Recent research achieved a 97% success rate. Poisoning telemetry feeds against GPT-4o systems deployed in production environments. The attack exploited the model's reliance on real-time performance metrics for dynamic resource allocation.
Attack Vector Analysis: The attack worked by injecting false congestion notifications into network telemetry streams with surgical precision. GPT-4o's automated scaling systems interpreted these signals as genuine performance degradation and began migrating inference workloads to alternative resources.
By carefully timing these injections, adversaries could force the system to move computations. Compromised infrastructure under their control. Once workloads migrated to attacker-controlled resources, they gained access to model queries, responses, and potentially cached model parameters.
The attack's high success rate resulted from GPT-4o's aggressive optimization algorithms. Prioritized performance over security. The system assumed telemetry integrity and made automated decisions based on potentially manipulated data.
AIOps System Subversion Techniques
Modern AIOps platforms implement sophisticated decision-making algorithms. Respond automatically to telemetry anomalies. These systems become attack vectors when adversaries understand their behavioral patterns and decision logic.
- Resource Misallocation Attacks: By injecting false resource utilization metrics, attackers can deceive AIOps systems into making suboptimal resource allocation decisions that waste money and degrade performance. This could involve forcing expensive computations onto slower hardware or creating artificial resource scarcity.
- Denial of Service Through Automation: Telemetry poisoning can trigger automated responses. Create cascade failures across AI infrastructure. False failure indicators could cause AIOps systems to unnecessarily restart services, migrate workloads, or trigger emergency procedures.
- Backdoor Installation Through Trust: AIOps systems often have elevated privileges. Making infrastructure changes. Telemetry manipulation could deceive these systems into installing attacker-controlled software components or modifying security configurations.
- Performance Degradation Campaigns: Sustained telemetry manipulation can create chronic performance issues. Degrade AI system efficiency over time. These attacks are particularly insidious because they mimic legitimate infrastructure aging and capacity constraints.
Supply Chain Attacks via Telemetry
Telemetry systems often integrate with third-party monitoring tools. Cloud services, and vendor management platforms. This integration creates supply chain attack vectors where compromised external systems can inject malicious telemetry data.
The SolarWinds incident demonstrated how supply chain compromises. Could affect monitoring and management systems across thousands of organizations. Similar attacks targeting AI telemetry platforms could have even more severe consequences given the automated decision-making capabilities of modern AIOps systems.
Real-World Evidence: Recent security assessments identified over 200 unprotected Chroma vector database servers exposed to the internet with default configurations, many containing telemetry data from AI systems. While these exposures represented configuration errors rather than active attacks, they demonstrated the potential scale of telemetry-based supply chain vulnerabilities.
Comparative Security Analysis: Ethernet vs. InfiniBand Architectures
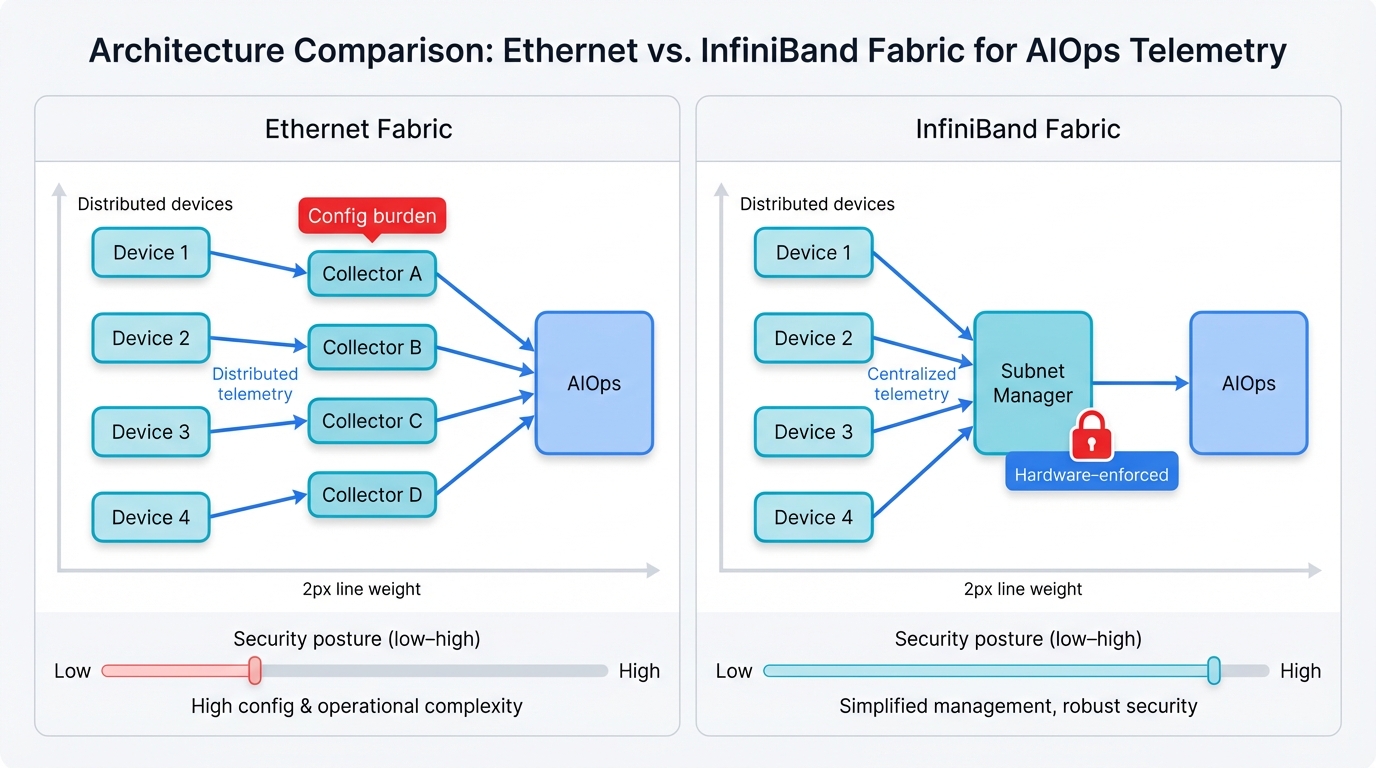
Security Architecture Fundamentals
The fundamental architectural differences between Ethernet and InfiniBand create vastly different security postures. Telemetry collection and management. Understanding these differences is crucial for making informed infrastructure decisions and implementing appropriate security controls.
Ethernet's success stems from its open, distributed architecture. Enables vendor competition and rapid innovation. However, this same openness creates security complexity that operators must manage through layered defenses and careful configuration management.
InfiniBand's centralized management model prioritizes performance. Reliability through hardware-enforced policies and comprehensive fabric oversight. This approach provides inherent security advantages but requires specialized expertise and limits vendor flexibility.
Ethernet Fabric Security Challenges
Distributed Trust Model Vulnerabilities
Ethernet fabrics rely on distributed protocols. Individual switches make local decisions based on limited information. This model creates numerous trust boundaries that adversaries can exploit for telemetry manipulation.
Consider how spanning tree protocol operates. Large Ethernet fabrics. Individual switches exchange bridge protocol data units (BPDUs) to elect root bridges and determine optimal forwarding paths. An adversary with access to switch management or packet injection capabilities could manipulate this process to influence traffic patterns and telemetry collection points.
Vulnerability Pattern: The same vulnerability extends to telemetry collection protocols with alarming consistency. sFlow implementations typically allow any authorized device to send telemetry samples to collectors. Without proper authentication and integrity checking, attackers can inject false data that appears to originate from legitimate network devices.
Protocol Stack Complexity
Modern Ethernet AI fabrics implement complex protocol stacks. Layer multiple technologies: base Ethernet for connectivity, priority flow control for lossless operation, explicit congestion notification for feedback, and RDMA protocols for high-performance communication.
Each protocol layer introduces potential security vulnerabilities:
- Layer 2 Vulnerabilities: VLAN hopping, ARP poisoning, and spanning tree manipulation can affect telemetry collection. Redirecting traffic flows or creating false network topology information.
- Priority Flow Control Exploits: PFC pause frame injection can create artificial congestion conditions. Mislead telemetry systems about actual network performance.
- RDMA Security Gaps: RoCE implementations often lack proper authentication mechanisms. Allowing unauthorized devices to participate in high-performance communication flows and access sensitive telemetry data.
- Congestion Control Manipulation: ECN marking injection can deceive congestion control algorithms. Causing suboptimal traffic engineering decisions based on false telemetry inputs.
InfiniBand Security Advantages
Centralized Security Management
InfiniBand's Subnet Manager provides comprehensive fabric oversight. Simplifies security management and reduces attack surfaces. All fabric configuration, topology management, and performance monitoring flows through authenticated centralized channels.
The Subnet Manager maintains complete topology awareness. Can implement fabric-wide security policies consistently across all devices. This eliminates the configuration drift and policy inconsistencies that plague large Ethernet deployments.
Security Benefits: For telemetry security, centralized management means unified access control where all telemetry access requests go through the Subnet Manager with cryptographic verification, topology validation to detect unauthorized devices, and consistent policy enforcement across the entire fabric.
Hardware-Enforced Security Features
InfiniBand implements security controls directly in silicon. Making them resistant to software-based attacks that commonly affect Ethernet implementations.
- Partition Key (P_Key) Security: Hardware enforces partition boundaries. Prevent unauthorized access to telemetry streams. Unlike software-based VLANs that can be bypassed through configuration errors, P_Key enforcement happens in the switch ASICs.
- Service Level Enforcement: Quality of service and security policies are enforced at the hardware level with silicon-based guarantees. Preventing software attacks from bypassing traffic controls or accessing unauthorized telemetry data.
- Queue Pair Security: Application-level security extends to telemetry collection. Through hardware-enforced queue pair permissions that control which processes can access specific performance data streams.
Proven Security Track Record
InfiniBand's security model has been battle-tested. High-security environments including financial trading systems, government research facilities, and classified computing environments. This track record provides confidence in its ability to protect sensitive AI telemetry data.
Recent security evaluations during 2024-2025 confirmed InfiniBand's resistance. Many attack techniques that successfully compromised Ethernet-based AI fabrics. Hardware-enforced security policies maintained telemetry integrity even under sophisticated attack scenarios.
Comprehensive Risk Assessment Framework
Risk Categorization and Impact Analysis
To effectively address telemetry security risks. AI fabrics, organizations need a structured framework for assessing threats and prioritizing mitigation efforts. Our analysis identifies three primary risk categories with varying impact levels and likelihood factors.
High-Impact, High-Likelihood Risks
These represent the most critical threats. Organizations should address immediately:
Passive Reconnaissance Through Telemetry Access: Adversaries with legitimate or compromised access to telemetry systems can extract valuable intelligence about AI workloads, competitive activities, and business operations with remarkable precision. This risk is particularly high because telemetry access is often granted broadly for operational reasons.
- Impact Assessment: Industrial espionage, competitive disadvantage, intellectual property theft
- Likelihood: High due to broad telemetry access requirements and limited access controls
- Mitigation Priority: Critical - implement immediately
AIOps System Manipulation: Telemetry poisoning attacks against automated orchestration systems can cause significant operational disruption. Resource misallocation. The 97% success rate against GPT-4o systems demonstrates the maturity of these attack techniques.
- Impact Assessment: Service disruption, financial losses from resource waste, potential data exposure
- Likelihood: High in environments with automated response systems
- Mitigation Priority: Critical - requires immediate attention
Threat Actor Profiling
Understanding who might target AI telemetry systems. Helps organizations focus defensive efforts appropriately.
Nation-State Actors
Advanced persistent threat groups have strong motivations. Targeting AI infrastructure telemetry:
- Intelligence Collection: AI capabilities represent strategic national advantages. Making AI telemetry valuable for understanding competitor capabilities and progress.
- Economic Espionage: State-sponsored actors may target commercial AI developments. Economic benefit or to support domestic companies.
- Infrastructure Disruption: Telemetry poisoning could enable sophisticated attacks. Against critical AI infrastructure supporting national security or economic functions.
- Capabilities Assessment: Nation-state actors possess the resources and expertise. Required for sophisticated telemetry manipulation attacks.
Commercial Competitors
Business competitors have strong economic incentives. Access AI telemetry intelligence:
- Market Intelligence: Understanding competitor AI capabilities, resource utilization, and development timelines provides significant business advantages in rapidly evolving markets.
- Customer Acquisition: Telemetry data revealing service quality issues. Capacity constraints could support competitive sales efforts.
- Technology Intelligence: Performance characteristics and optimization techniques visible through telemetry represent valuable intellectual property worth millions.
Business Impact Quantification
Annual Loss Expectancy (ALE) = Single Loss Expectancy (SLE) × Annual Rate of Occurrence (ARO)
Example calculation for a large AI training operation:
- SLE for telemetry poisoning attack: $500,000 (combining operational disruption, investigation costs, and competitive impact)
- ARO for sophisticated adversaries: 0.3 (30% chance annually given current threat landscape)
- ALE: $150,000 annually
This calculation helps justify security investments. Prioritize mitigation efforts based on quantified risk levels.
Detailed Mitigation Strategies and Implementation Guidelines
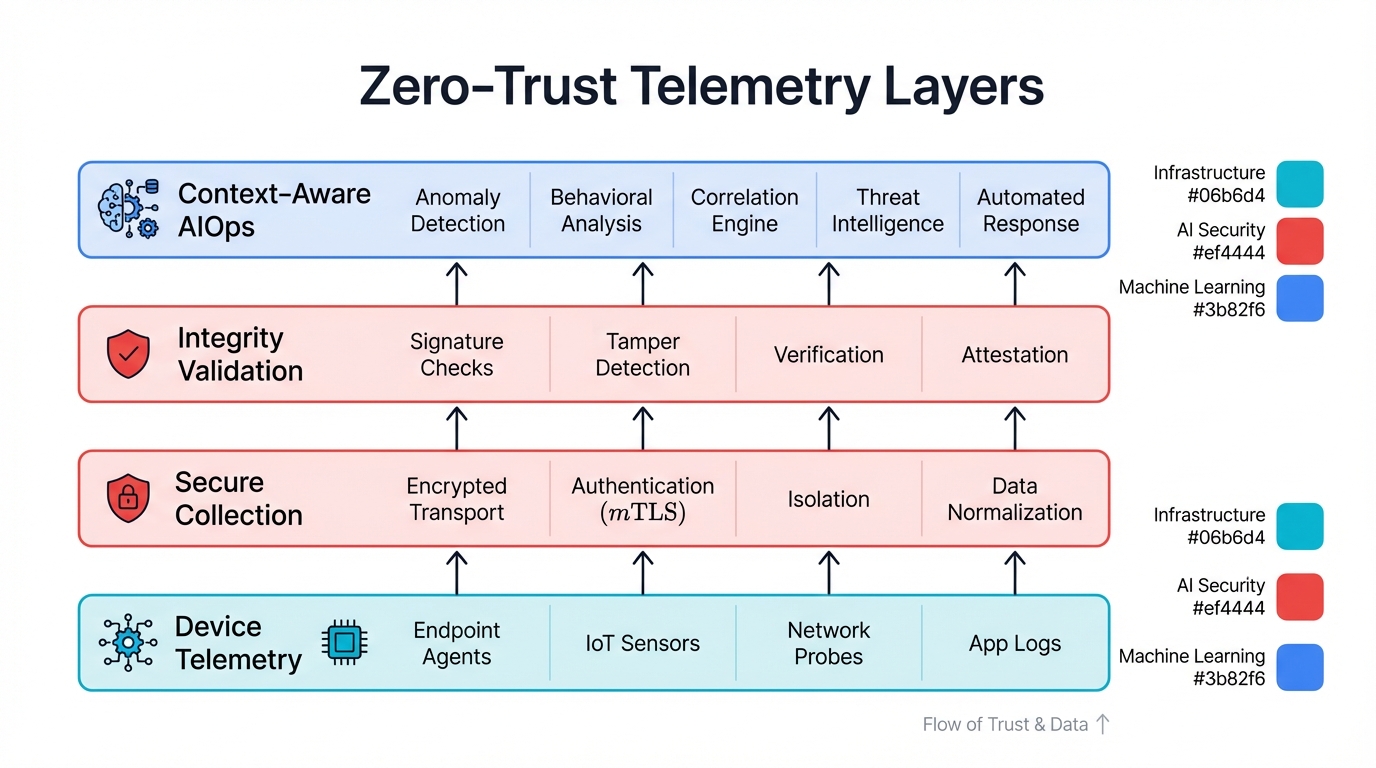
Zero-Trust Telemetry Architecture
The fundamental principle of Zero-Trust security applies directly to telemetry systems. Never trust, always verify. Every telemetry data source, transmission channel, and consuming system must be authenticated and authorized before accessing sensitive performance data.
Identity and Access Management for Telemetry
Traditional telemetry systems often rely on network-based trust models. Any device on the management network can send telemetry data to collectors. Zero-Trust architecture replaces this implicit trust with explicit identity verification for every telemetry interaction.
Implementation Requirements:
- PKI infrastructure for device certificate management
- Automated certificate provisioning and renewal systems
- Certificate revocation mechanisms for compromised devices
- Hardware security modules (HSMs) for protecting device private keys
Service Account Management: Applications and AIOps systems consuming telemetry need dedicated service accounts. Precisely defined permissions. Avoid shared accounts or overprivileged access that creates unnecessary attack surfaces.
Dynamic Access Controls: Implement just-in-time access granting. Provides telemetry access only when needed for specific operational tasks. This minimizes the window for insider threats and reduces the impact of credential compromise.
Microsegmentation for Telemetry Networks
Network microsegmentation isolates telemetry traffic. Production workloads and limits lateral movement opportunities for adversaries who gain initial access.
- Dedicated Telemetry Networks: Separate physical or logical networks. Telemetry collection provide security boundaries and performance isolation.
- Software-Defined Perimeters: Create encrypted tunnels. All telemetry communication that provide authentication and authorization at the network level.
- Application-Level Segmentation: Within telemetry networks, further segment access. Based on data sensitivity and business requirements.
Data Integrity and Validation Controls
Protecting telemetry data integrity prevents poisoning attacks. Ensures AIOps systems make decisions based on trustworthy information.
Cryptographic Data Protection
- End-to-End Encryption: Encrypt all telemetry data. From generation through consumption to prevent interception and manipulation during transmission. Use modern encryption algorithms (AES-256-GCM) with proper key management.
- Digital Signatures: Sign telemetry data at the source. Enable integrity verification throughout the processing pipeline.
- Hash Chains: Implement cryptographic hash chains. Link sequential telemetry samples, making it impossible to insert false data without detection.
Statistical Validation Techniques
Advanced Validation Methods:
- Anomaly Detection: Implement statistical models. Understand normal telemetry patterns and can detect injected false data.
- Cross-Validation: Compare telemetry data. Multiple sources to identify inconsistencies that might indicate manipulation.
- Temporal Consistency Checking: Verify that telemetry data follows physically possible patterns. Over time.
Context-Aware AIOps Security
AIOps systems must be designed with security awareness. Rather than assuming all telemetry inputs are trustworthy.
Defensive AIOps Design Principles
- Input Sanitization: Treat all telemetry inputs as potentially malicious. Implement comprehensive sanitization before using data for automated decisions.
- Decision Confidence Scoring: Implement confidence scoring. All automated decisions based on input data quality and consistency.
- Graceful Degradation: Design AIOps systems to function safely. When telemetry data quality is compromised.
Human-in-the-Loop Controls
Critical Decision Gates: Require human approval for high-impact automated decisions, especially those involving resource allocation changes, security policy modifications, or service migrations that could affect millions of dollars in infrastructure investments. Implement anomaly review processes and clear override mechanisms for human operators.
Fabric-Specific Security Implementation
Different fabric architectures require tailored security approaches. Account for their unique characteristics and capabilities.
Ethernet Fabric Hardening
Switch Security Configuration: Implement comprehensive security configurations. Across all Ethernet switches including access control lists, port security, DHCP snooping, and storm control.
Protocol Security Enhancement: Enable security features available. Telemetry protocols including sFlow authentication, NetFlow encryption, and SNMP v3 protection.
Management Network Security: Secure the management networks. Used for telemetry collection through dedicated VLANs, encrypted protocols, and network access control.
InfiniBand Security Optimization
Subnet Manager Hardening: Secure the centralized Subnet Manager. Through strong authentication, encrypted communication, and regular security updates.
Partition Key Management: Implement comprehensive P_Key management. Including regular rotation, principle of least privilege, and hardware security module protection.
Service Level Security: Configure service levels. Provide security isolation and prevent denial of service attacks.
Strategic Implementation Roadmap
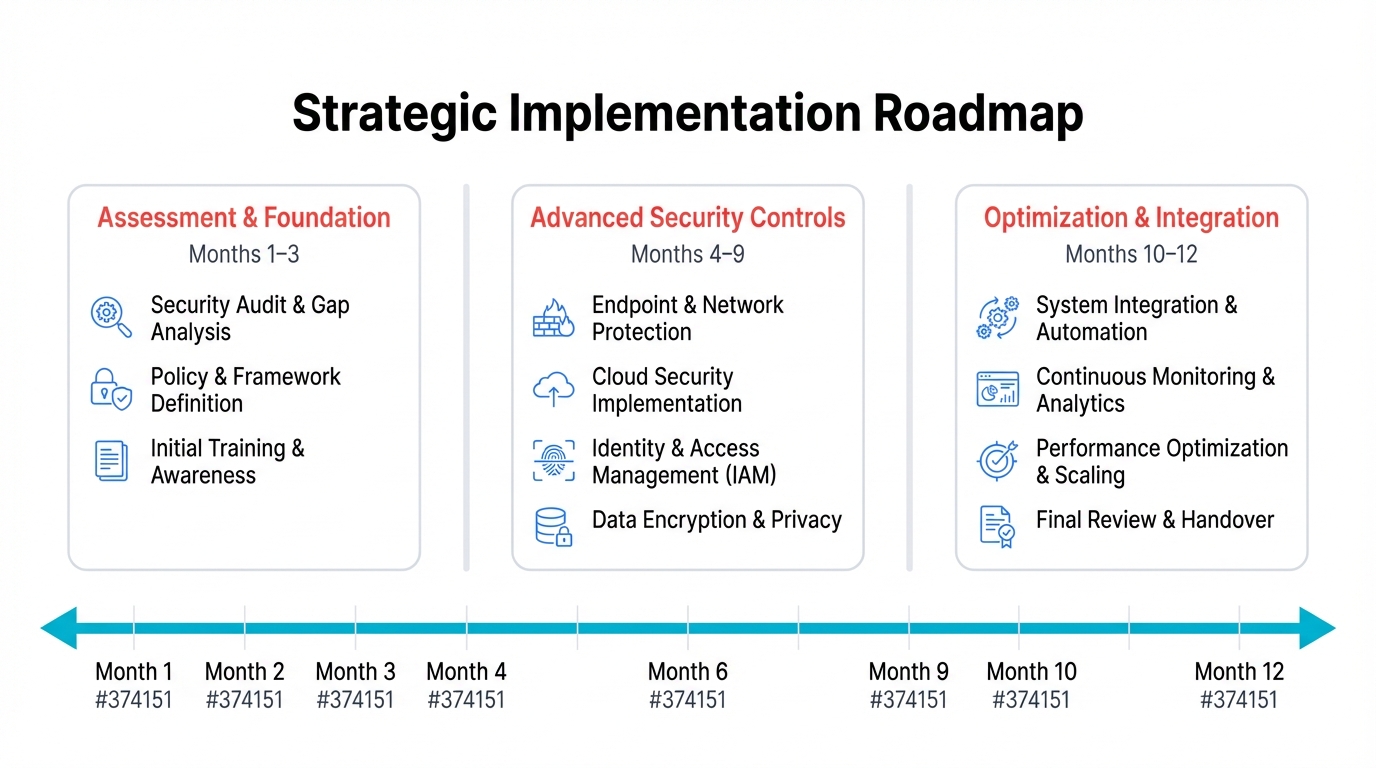
Phase 1: Assessment and Foundation (Months 1-3)
The first phase focuses on understanding. Current telemetry security posture and establishing foundational security controls that provide immediate risk reduction.
Current State Security Assessment
Telemetry Architecture Audit: Document all existing telemetry collection systems. Data flows, and consuming applications. Many organizations lack comprehensive visibility into their telemetry infrastructure, making security assessment impossible.
Documentation Requirements:
- All telemetry data sources (switches, servers, applications)
- Collection protocols and encryption status
- Data transmission paths and network segments
- Storage systems and retention policies
- Consuming applications and access permissions
Threat Modeling Workshops: Conduct structured threat modeling sessions. Stakeholders from network operations, security, and AI development teams. Use frameworks like STRIDE or PASTA to systematically identify potential attack vectors and impact scenarios.
Gap Analysis: Compare current security controls. Against the mitigation strategies outlined in this report. Prioritize gaps based on risk assessment and implementation complexity.
Quick-Win Security Improvements
Access Control Hardening: Implement immediate improvements. Telemetry system access controls:
- Remove unnecessary accounts and overprivileged access
- Enable multi-factor authentication for telemetry system access
- Implement network access controls restricting telemetry protocol access
- Deploy monitoring for telemetry system login attempts and access patterns
Encryption Deployment: Enable encryption. Telemetry data transmission where supported:
- Configure TLS encryption for HTTPS-based telemetry APIs
- Enable SNMP v3 with authentication and privacy protection
- Implement IPsec or WireGuard VPNs for telemetry network isolation
- Deploy encrypted tunnels for cross-site telemetry data transmission
Phase 2: Advanced Security Controls (Months 4-9)
The second phase implements sophisticated security controls. Provide comprehensive protection against advanced threats.
Zero-Trust Architecture Implementation
Microsegmentation Deployment: Implement comprehensive network microsegmentation. Through software-defined networking, application-level policies, and encrypted communication channels.
Continuous Verification Systems: Deploy systems providing ongoing security validation. Including user and entity behavior analytics, continuous compliance monitoring, and automated threat response.
Data Integrity Protection
Cryptographic Protection Implementation:
- End-to-end encryption for all telemetry data flows
- Digital signature systems for telemetry data authentication
- Hardware security modules for key management and protection
- Regular key rotation and compromise recovery procedures
Advanced Validation Systems: Implement sophisticated telemetry data validation. Including machine learning-based anomaly detection, cross-correlation systems, and automated integrity alerting.
Phase 3: Optimization and Integration (Months 10-12)
The final phase optimizes security controls. Operational efficiency and integrates telemetry security with broader organizational security programs.
Performance Optimization
Security Control Tuning: Optimize security controls. Minimize performance impact through algorithm selection, compression optimization, and load balancing.
Operational Efficiency Enhancement: Streamline security operations. Through automated policy deployment, self-service capabilities, and integrated dashboards.
Organizational Integration
Policy and Procedure Development: Develop comprehensive policies. Governing telemetry security including data classification, incident response procedures, and third-party risk management.
Training and Awareness Programs: Implement training programs. Ensuring organizational understanding of telemetry security through awareness training, technical training, and incident response exercises.
Continuous Improvement Framework
Metrics and Measurement: Establish metrics tracking telemetry security program effectiveness. Including security incident measurements, compliance assessments, user satisfaction, and cost-benefit analysis.
Threat Intelligence Integration: Integrate telemetry security. Broader threat intelligence programs through industry participation, commercial feeds, and internal research.
Security Research and Development: Invest in ongoing security research. Capability development through academic collaboration, red team exercises, and emerging technology evaluation.
Future Research Directions and Industry Implications
Emerging Threat Vectors in AI Telemetry
As AI fabrics continue evolving, new attack vectors will emerge. Require proactive research and defense development. Understanding these emerging threats helps organizations prepare for future security challenges.
Quantum-Safe Telemetry Security
The emergence of quantum computing threatens current cryptographic protection mechanisms. Used in telemetry systems. Organizations must begin planning for post-quantum cryptography migration to maintain long-term telemetry security.
Quantum Threat Timeline: Current estimates suggest cryptographically relevant quantum computers may emerge within 10-15 years with devastating impact on existing security infrastructure. However, telemetry data collected today might remain sensitive longer than this timeline, requiring immediate attention to quantum-safe cryptography.
Migration Planning: Organizations need structured plans. Migrating telemetry systems to quantum-safe cryptography including inventory of current implementations, performance impact assessments, hybrid transition approaches, and certificate management system upgrades.
AI-Powered Attack Evolution
As AI capabilities improve, adversaries will leverage machine learning. Enhance telemetry attacks with unprecedented sophistication and automation.
- Automated Reconnaissance: AI systems could analyze vast amounts of telemetry data. Automatically identify attack opportunities and extract intelligence about target organizations.
- Sophisticated Poisoning Attacks: Machine learning could enable telemetry poisoning attacks. Adapt dynamically to defensive measures through reinforcement learning and generative adversarial networks.
- Defense Automation Requirements: Organizations must prepare for AI-powered attacks. Developing equally sophisticated defenses including machine learning detection models and automated threat hunting systems.
Edge AI Telemetry Challenges
The proliferation of edge AI deployments creates new telemetry security challenges. Differ significantly from centralized data center environments.
- Distributed Trust Management: Edge deployments often lack centralized security infrastructure. Requiring new approaches including decentralized identity management and blockchain-based trust systems.
- Resource-Constrained Security: Edge devices have limited computational resources. Constrain security control implementation through lightweight cryptography and efficient algorithms.
- Supply Chain Complexity: Edge AI deployments involve complex supply chains. Creating additional security challenges including hardware validation and software integrity verification.
Regulatory and Compliance Evolution
Regulatory frameworks governing AI security are rapidly evolving. With implications for telemetry security requirements and compliance obligations.
International Regulatory Trends
European Union AI Act: The EU's comprehensive AI regulation includes security requirements. May extend to telemetry systems supporting AI applications through risk assessment requirements, documentation standards, and incident reporting obligations.
US Executive Orders and NIST Frameworks: US government AI security initiatives are establishing standards. May influence industry practices including NIST AI Risk Management Framework guidance and federal agency requirements.
Sector-Specific Regulations: Different industries face unique regulatory requirements. Affecting telemetry security including financial services, healthcare, automotive, and telecommunications regulations.
Compliance Framework Development
Industry Standards Evolution: Technical standards organizations are developing new frameworks. Specifically addressing AI security including ISO/IEC standards, IEEE standards, industry consortium standards, and certification programs.
Audit and Assessment Requirements: New compliance frameworks require sophisticated audit capabilities. Including automated compliance monitoring, third-party assessments, and continuous compliance reporting.
Industry Collaboration and Standards Development
Addressing telemetry security challenges requires coordinated industry collaboration. Standards development efforts.
Open Source Security Solutions
Community-Driven Development: Open source projects provide opportunities. Industry collaboration including open source telemetry platforms, community-developed security tools, and shared threat intelligence platforms.
Vendor-Neutral Standards: Industry collaboration on vendor-neutral security standards. Reduces fragmentation including common telemetry data formats, standard APIs, and interoperable identity management systems.
Research and Development Collaboration
Academic Partnerships: Collaboration between industry and academia. Accelerates telemetry security research through university research programs, industry-sponsored research, and joint development projects.
Government Collaboration: Public-private partnerships support telemetry security research. Including government funding, information sharing programs, and collaborative vulnerability disclosure.
International Cooperation: Global collaboration addresses telemetry security challenges. Including international working groups, cross-border threat intelligence sharing, and harmonized regulatory approaches.
Conclusion: Building Resilient AI Infrastructure Through Secure Telemetry
The evidence is clear. Telemetry systems have evolved from simple monitoring tools. Into critical infrastructure components that can either strengthen or compromise AI security posture. Organizations that recognize this evolution and act decisively will maintain competitive advantages and operational resilience. Those that continue treating telemetry as an afterthought face significant risks in an increasingly hostile threat landscape.
The Strategic Imperative for Action
Your AI infrastructure investments depend fundamentally on telemetry system integrity. Whether millions spent on GPU clusters. Years invested in model development. The 97% success rate achieved in recent GPT-4o telemetry poisoning attacks demonstrates that these aren't theoretical vulnerabilities waiting to be discovered but active attack vectors being exploited today against real systems in production environments around the world.
Urgent Reality Check: The current threat landscape demands immediate action without delay or hesitation. With 93% of security leaders anticipating daily AI attacks within the next year, organizations cannot afford to delay telemetry security improvements. The average $4.1 million cost of AI-related security incidents, offset by $1.8 million in savings from proper AI security frameworks, provides clear financial justification for comprehensive telemetry protection programs.
Consider the implications of inaction for a moment. Passive exploitation allows competitors to gain intelligence. About your AI capabilities, training progress, and business priorities through telemetry reconnaissance. Active manipulation enables adversaries to disrupt operations, waste resources, and potentially compromise sensitive data through AIOps system subversion. These aren't distant possibilities—they're current realities affecting organizations across industries.
The Path Forward: Implementation Priorities
Organizations must move beyond reactive security approaches. Toward proactive telemetry protection strategies. The three-phase implementation roadmap outlined in this report provides a structured path forward, but success requires commitment at all organizational levels.
Immediate Actions (Next 30 Days):
- Conduct comprehensive telemetry security assessments to understand current vulnerabilities
- Implement basic access controls and encryption for telemetry data transmission
- Deploy security monitoring specifically focused on telemetry infrastructure
- Begin threat modeling workshops to identify organization-specific attack vectors
Medium-Term Objectives (6-12 Months): Deploy Zero-Trust architecture principles. Across telemetry infrastructure, implement comprehensive data integrity protection with cryptographic validation, enhance AIOps systems with security-aware decision-making capabilities, and develop incident response procedures specifically addressing telemetry attacks.
Long-Term Strategic Goals (12+ Months): Achieve full integration. Between telemetry security and organizational security programs, establish continuous improvement frameworks for evolving threat landscapes, contribute to industry standards development and threat intelligence sharing, and develop internal expertise for emerging telemetry security challenges.
Fabric Architecture Considerations for Future Deployments
The choice between Ethernet and InfiniBand architectures has profound implications. Long-term telemetry security posture. Organizations planning new AI fabric deployments should carefully evaluate security capabilities alongside performance and cost considerations.
InfiniBand's centralized security model provides inherent advantages. Telemetry protection through hardware-enforced policies and comprehensive fabric management. The proven track record in high-security environments and resistance to sophisticated attacks demonstrated during recent security evaluations make InfiniBand attractive for security-conscious organizations.
Ethernet's flexibility and ecosystem maturity remain compelling. Many deployments, but organizations must invest significantly more effort in security configuration and management. The distributed trust model requires careful attention to protocol security, access controls, and configuration consistency across potentially thousands of devices.
Architecture Decision Framework: Hybrid approaches combining both architectures require special attention. Security boundaries and trust transitions. Organizations must avoid creating weak links where telemetry data crosses between different fabric types with varying security models.
The Broader Implications for AI Security
Telemetry security represents a microcosm. Broader AI security challenges: the tension between operational requirements and security concerns, the complexity of securing rapidly evolving technologies, and the need for proactive rather than reactive security approaches.
The lessons learned from telemetry security apply broadly. Across AI infrastructure:
- Assume Compromise: Traditional network security models based on perimeter defense prove inadequate. AI infrastructure. Zero-Trust principles must extend throughout AI systems, including traditionally trusted components like monitoring and observability platforms.
- Automate Defensively: As AI systems become increasingly autonomous, security controls must evolve to match with equal sophistication. Automated decision-making systems require security-aware design that considers potential manipulation and validates inputs comprehensively.
- Collaborate Proactively: The complexity and novelty of AI security challenges exceed what any single organization can address independently with limited resources. Industry collaboration, standards development, and threat intelligence sharing are essential for effective defense.
- Invest in Expertise: AI security requires specialized knowledge. Combines traditional cybersecurity expertise with deep understanding of AI systems and infrastructure. Organizations must invest in developing internal capabilities or partnering with specialized providers.
Final Recommendations: Building Organizational Resilience
Success in telemetry security requires more than technology deployment. It demands organizational transformation that prioritizes security throughout AI infrastructure lifecycle management.
Executive Leadership: Senior executives must understand that telemetry security directly impacts business objectives. Competitive positioning. Regular security briefings should include telemetry-specific threats and mitigation progress.
Cross-Functional Collaboration: Telemetry security touches every aspect of AI operations. Requiring collaboration between security, network operations, AI development, and business stakeholders. Break down organizational silos that prevent effective security coordination.
Continuous Learning: The threat landscape evolves rapidly. Requiring ongoing education and capability development. Invest in training programs, conference attendance, and industry participation that keep security teams current with emerging threats and defenses.
The Future of Secure AI Infrastructure
The organizations that emerge as AI leaders will be those that recognize security as a competitive advantage rather than a cost center that drains resources. Secure telemetry systems enable the automation, optimization, and innovation that drive AI success while protecting against the sophisticated threats targeting modern AI infrastructure.
Competitive Advantage Through Security: The investment in telemetry security pays dividends beyond risk reduction with measurable returns on investment. Organizations with robust telemetry security can deploy more aggressive automation, share data more freely with partners, and operate with confidence in high-stakes environments. These capabilities become competitive advantages in industries where AI performance determines business success.
The techniques and technologies discussed in this report represent current best practices. But the field continues evolving rapidly. Organizations must balance immediate security improvements with preparation for future challenges like quantum computing threats, AI-powered attacks, and evolving regulatory requirements.
The choice is clear. Organizations can either lead in telemetry security. Reap the benefits of secure, automated AI infrastructure, or fall behind competitors who recognize the strategic importance of protecting the data that drives AI success. The time for action is now, while the opportunity for competitive advantage still exists.
The future belongs to organizations that master both AI technology and the security foundations that make trustworthy AI possible, creating systems that deliver breakthrough performance while maintaining unwavering protection against sophisticated adversaries. Telemetry security represents a critical component of that foundation—one that forward-thinking organizations are already beginning to build with determination and foresight.
What's Next?
Continue your AI security learning journey. These related articles:
Example Implementation
# Example: Model training with security considerations
import numpy as np
from sklearn.model_selection import train_test_split
from sklearn.ensemble import RandomForestClassifier
def train_secure_model(X, y, validate_inputs=True):
"""Train model with input validation"""
if validate_inputs:
# Validate input data
assert X.shape[0] == y.shape[0], "Shape mismatch"
assert not np.isnan(X).any(), "NaN values detected"
# Split data securely
X_train, X_test, y_train, y_test = train_test_split(
X, y, test_size=0.2, random_state=42, stratify=y
)
# Train with secure parameters
model = RandomForestClassifier(
n_estimators=100,
max_depth=10, # Limit to prevent overfitting
random_state=42
)
model.fit(X_train, y_train)
score = model.score(X_test, y_test)
return model, score