🔗 Interactive Visual Comparison
View Security Showdown Infographic →Explore side-by-side security comparisons, architectural differences, and strategic recommendations
A Comparative Security Analysis of InfiniBand and Ethernet Fabrics for Sovereign AI and Regulated Workloads
Executive Summary
This matters. For sovereign AI and regulated workloads, choosing between InfiniBand and high-performance Ethernet transcends technical specifications—it's fundamentally a security choice. Think of InfiniBand as a fortress with a single strong gate. Ethernet distributes checkpoints across the perimeter. Different philosophies. Different risks. Both approaches work, but they embody distinct security paradigms that align with different operational philosophies.
InfiniBand provides centralized, hardware-enforced security through its Subnet Manager architecture, functioning like a single trusted gatekeeper overseeing all traffic flows and access permissions. Ethernet distributes security across multiple independent layers through protocols like 802.1X for port authentication and MACsec for link encryption, creating several checkpoints that verify identity and protect data, aligning naturally with zero-trust principles but demanding significantly more management coordination and expertise.
Key Concept: Understanding this foundational concept is essential for mastering the techniques discussed in this article.
Centralization creates efficiency. It also creates vulnerability. InfiniBand's control flows through the Subnet Manager, making security policy enforcement clean and consistent, but if that SM falls to an attacker, the entire fabric becomes compromised. Ethernet spreads trust across IEEE 802.1X port-based authentication, MACsec link encryption, and VXLAN network segmentation, which introduces operational complexity but offers resilient layered protection where breaching one control doesn't collapse the entire security posture.
The devil lives in the details. When you examine authentication mechanisms, tenant isolation strategies, and quality of service controls, each fabric reveals distinct strengths and exploitable weaknesses. InfiniBand relies on hardware partition keys and delivers robust traffic separation, but it struggles with metadata protection, allowing tenants to potentially discover each other's existence. Ethernet proves vulnerable to resource starvation attacks through Priority Flow Control exploitation and fabric deadlocks from cascading pause frames, yet it excels at metadata security by completely isolating tenant visibility within VXLAN tunnels.
Strategy towers over tactics here. Your choice impacts technological independence in ways that ripple through decades of infrastructure decisions, vendor relationships, and national security postures. InfiniBand locks you into NVIDIA's ecosystem, creating supply chain dependencies and potential geopolitical leverage points that governments must carefully consider. Ethernet's open IEEE and IETF standards foster multi-vendor competition, reducing costs, promoting transparency, and enhancing technological sovereignty through supplier diversity. Performance matters, but sovereignty, resilience, and operational freedom matter more.
No universal winner exists. The optimal choice emerges from your specific security requirements, regulatory environment, threat landscape, and strategic objectives. It's a nuanced balance involving risk tolerance and resilience architecture, vendor dependencies and flexibility needs, operational complexity and team capabilities. Choose wisely. Choose strategically. Choose with eyes wide open to long-term implications.
Section 1: Architectural Foundations and Their Security Implications
Architecture determines destiny. Your network fabric's security capabilities flow directly from its foundational design principles, not from features bolted on later. Both InfiniBand and Ethernet connect high-performance systems powering AI training clusters and supercomputing workloads, but they build from radically different philosophical foundations. InfiniBand embraces centralized management through a single controlling entity. Converged Ethernet distributes control across layered, standardized protocols refined over decades. The crucial difference? InfiniBand centralizes security policies and enforcement points. Ethernet distributes security controls—and their associated vulnerabilities—across multiple independent layers that must coordinate correctly.
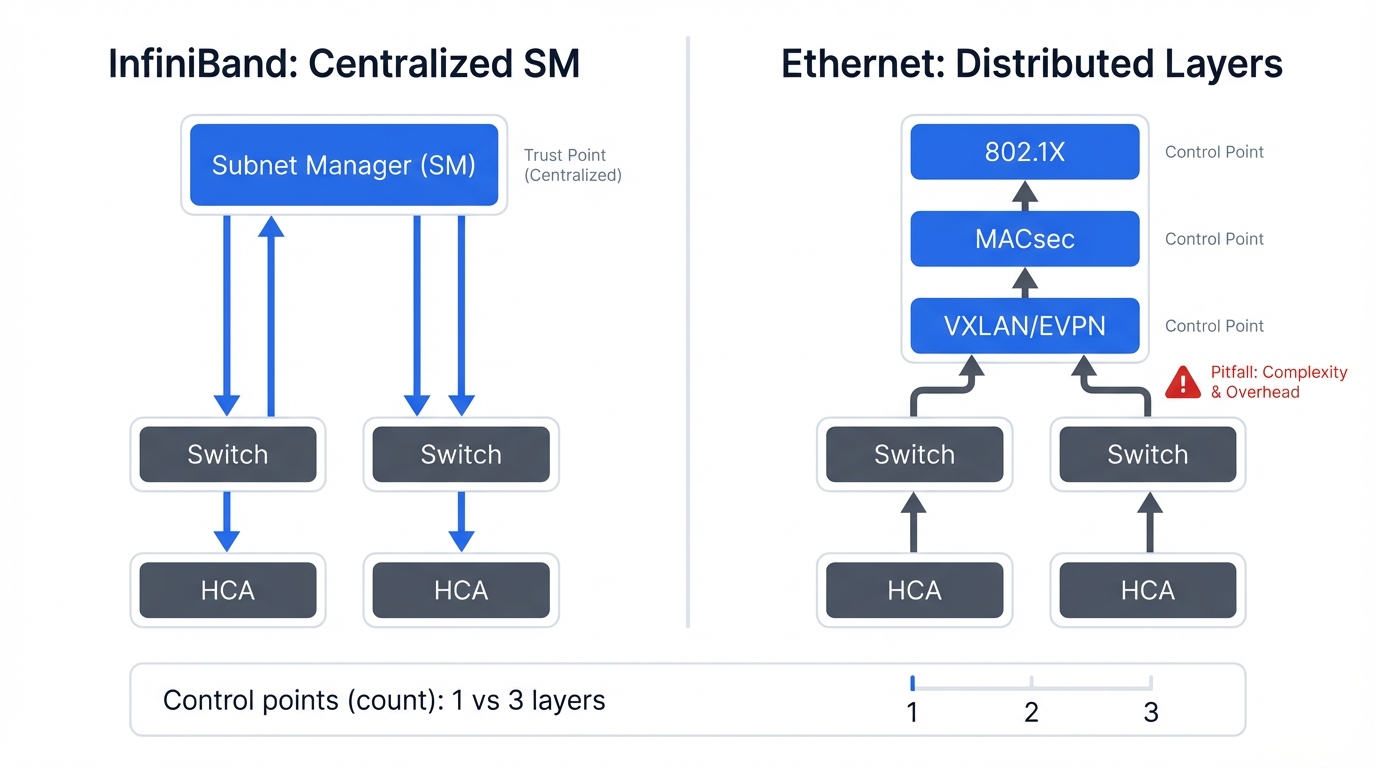
1.1. The InfiniBand Fabric: A Centrally Managed, Software-Defined Architecture
InfiniBand runs fast. It connects devices using a switched fabric topology where specialized network adapters called Host Channel Adapters (HCAs) link to switches through direct point-to-point connections, all orchestrated by a central brain called the Subnet Manager (SM). This SM discovers the physical topology, assigns unique identifiers to each port, configures packet routing through switches, and enforces network-wide policies. It makes InfiniBand fundamentally software-defined, with the SM serving as the single authoritative controller for the entire fabric's behavior and security posture.
The killer feature here is Remote Direct Memory Access (RDMA), which lets computers transfer data directly between their memory spaces without burdening the host CPU or involving the operating system's network stack. This direct path delivers sub-microsecond latency that traditional networking can't match. But speed creates risk. Traditional security tools like firewalls, intrusion detection systems, and network monitors can't see RDMA traffic because it bypasses the kernel entirely, creating an invisible data plane that security teams struggle to observe and protect.
The SM represents both strength and weakness—a critical single point of failure that demands protection through redundancy and hardening. InfiniBand networks typically deploy multiple SMs working in coordinated high-availability configurations where one SM operates as the active master handling all fabric management operations, while standby SMs monitor its health and stand ready to assume control instantly if the master fails. These SMs coordinate through a virtual IP address that always points to the currently active master, enabling transparent failover that maintains fabric operations even when individual SM instances crash or fall to attacks.
1.2. The Converged Ethernet Fabric: A Layered, Standards-Based Architecture for RoCEv2
Ethernet evolved differently. Traditional Ethernet served enterprise networks for decades, but recent enhancements through RDMA over Converged Ethernet version 2 (RoCEv2) made it viable for demanding AI workloads that need microsecond-level latency and massive bandwidth. This technology enables direct memory-to-memory transfers like InfiniBand, but it works by encapsulating InfiniBand transport semantics inside standard UDP/IP packets, allowing RDMA operations to traverse the same IP-routed networks that carry ordinary data center traffic.
The challenge? RDMA demands perfection. Unlike TCP, which recovers gracefully from packet loss through retransmission mechanisms, RDMA operations fail catastrophically when packets disappear, causing applications to stall or crash. This sensitivity requires meticulous network engineering using specialized flow control standards that prevent packet drops:
- Priority Flow Control (PFC): Pauses specific traffic classes when buffers fill, preventing loss but creating attack surfaces
- Explicit Congestion Notification (ECN): Signals early congestion warnings before buffers overflow, enabling proactive rate reduction
Large-scale deployments leverage sophisticated control plane protocols, particularly BGP enhanced with Ethernet VPN (EVPN) extensions that distribute reachability information and build overlay networks, managing the complex interconnections between thousands of endpoints, hundreds of network segments, and dozens of tenants sharing the same physical infrastructure.
1.3. The Security Dichotomy: Kernel Bypass vs. the Network Stack
Understanding data path architecture reveals security implications. InfiniBand achieves extreme performance through complete kernel bypass, transferring data via specialized hardware that never touches the host's network stack, making it inherently immune to kernel-level network exploits but also invisible to host-based security tools like software firewalls, packet capture utilities, and network monitoring agents. Security depends entirely on the fabric's built-in architectural protections, primarily controlled through the SM, which becomes the single critical trust anchor whose compromise exposes the entire data plane.
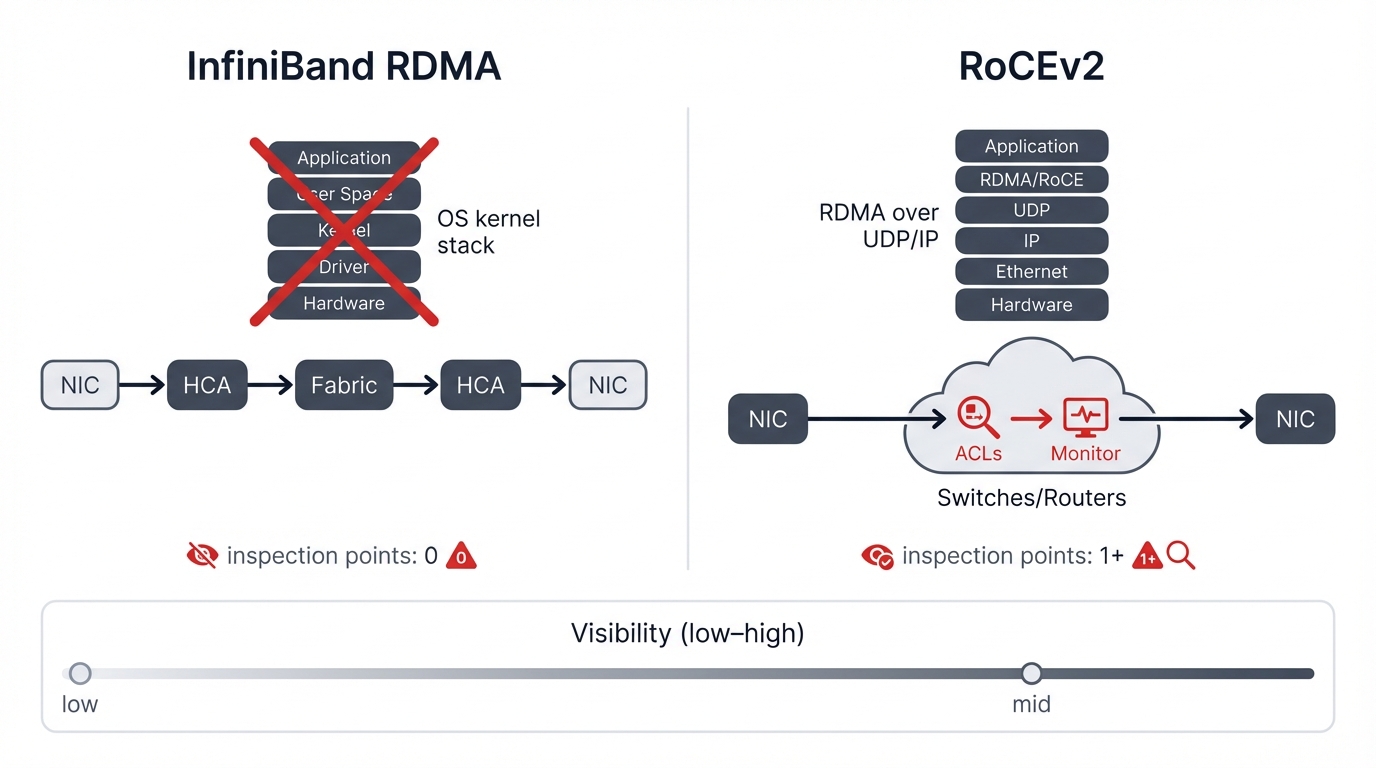
RoCEv2 splits the difference. It bypasses the kernel for RDMA operations, achieving low latency comparable to InfiniBand, but the underlying data still travels as standard IP packets routed through your network infrastructure using normal switching and routing hardware. This means traditional network security controls like Access Control Lists (ACLs) on switches, router-based filtering, and VLAN segmentation remain effective, providing visibility and control points that InfiniBand lacks. You get fast data transfer while maintaining network-layer security enforcement that security teams understand and trust.
These architectural differences reflect fundamentally different security philosophies that organizations must understand before making infrastructure commitments:
- InfiniBand security centralizes trust in the Subnet Manager, creating an efficient, consistent security model where policies flow from a single authoritative source that configures all devices and enforces all rules. But centralization creates fragility—if an attacker compromises the SM through software vulnerabilities, credential theft, or physical access, they gain control over the entire fabric, enabling them to reroute traffic, disable partition isolation, modify QoS policies, or exfiltrate telemetry data that maps tenant workloads and traffic patterns.
- Ethernet security layers independent controls that distribute trust and create defense in depth, using 802.1X to control port access at the physical layer, MACsec to protect link integrity at the data link layer, and VXLAN to enforce segmentation at the overlay network layer. This layered architecture aligns naturally with modern zero-trust security principles where no single control point is trusted absolutely. If attackers breach one layer through credential compromise or configuration errors, other independent layers continue providing protection, making complete fabric compromise substantially harder—though the complexity demands sophisticated security engineering and creates opportunities for misconfiguration that can undermine the entire security posture.
Choose based on your threat model. Organizations facing sophisticated adversaries benefit from Ethernet's defense in depth. Teams prioritizing simplicity may prefer InfiniBand's centralized model, accepting its single point of failure in exchange for operational simplicity. Neither choice is wrong—they're different bets on different risk profiles.
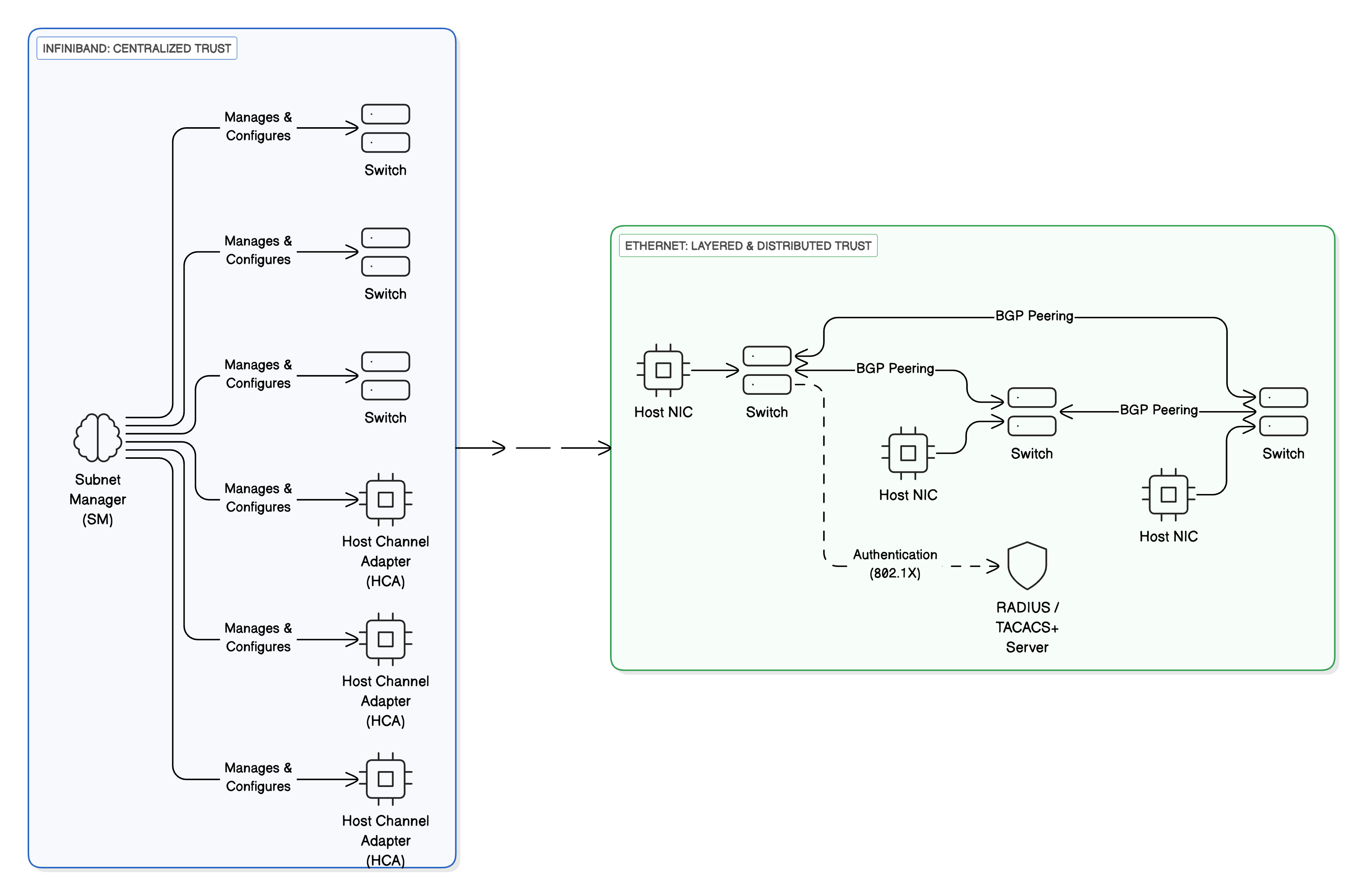
Figure 1: InfiniBand's centralized Subnet Manager approach versus Ethernet's distributed security model with BGP peering and authentication servers
Section 2: Authentication and Authorization: Establishing Trust in the Fabric
Authentication confirms identity. Authorization grants permissions. InfiniBand and Ethernet attack these fundamental security requirements from opposing directions, reflecting their architectural philosophies in ways that create dramatically different operational models and security trade-offs. InfiniBand implements fabric-centric authentication where the SM verifies its right to manage devices and authorizes specific communication paths between endpoints. Ethernet pursues device-centric and link-centric authentication, focusing on validating individual devices as they connect and securing physical links between network elements.
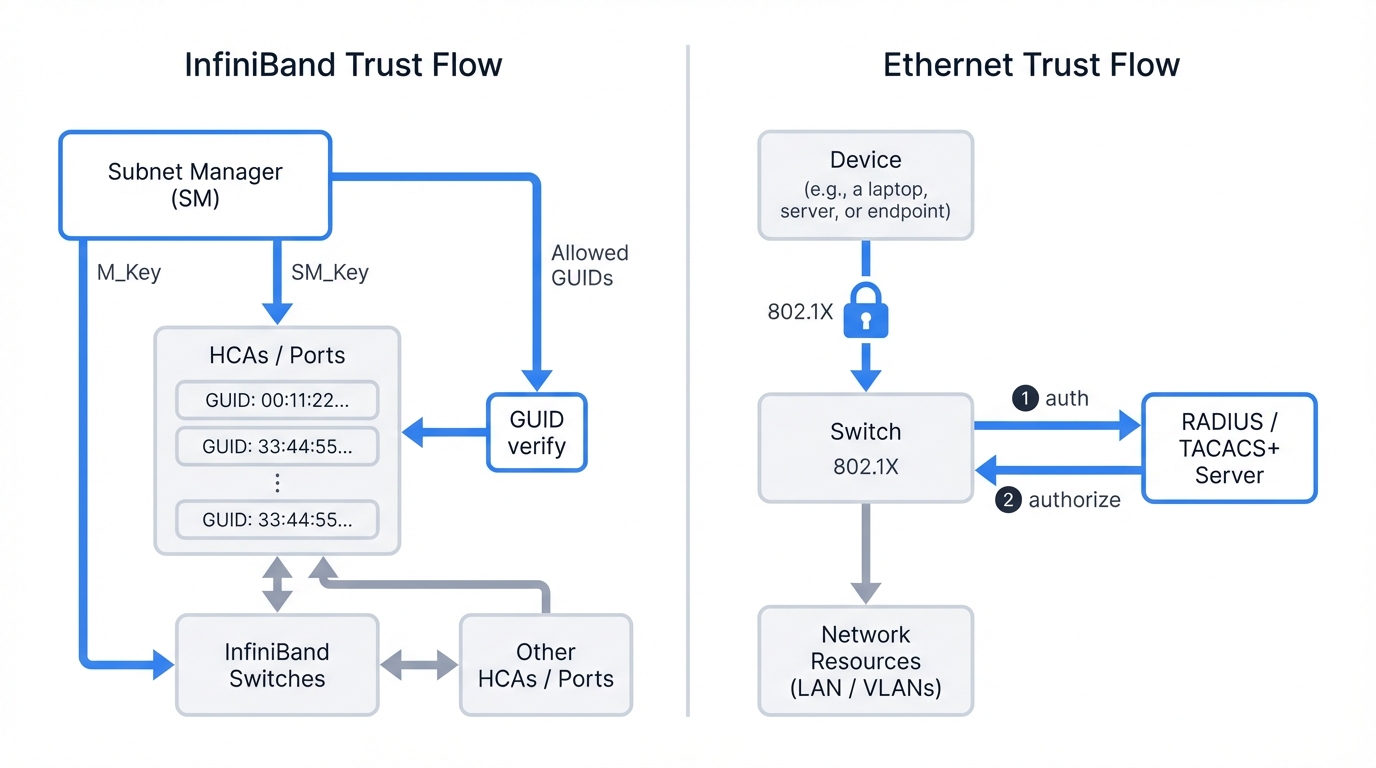
2.1. InfiniBand's Centralized Trust Model: The Subnet Manager and Key-Based Authentication
Keys matter here. InfiniBand security relies on cryptographic keys that function like access tokens, used for authentication and authorization but not for encrypting data in transit—a critical distinction that security teams must understand. The Subnet Manager serves as your central authority that generates, manages, and distributes these keys across the fabric, establishing trust relationships that control device configuration, fabric management, and inter-node communication.
Key Types:
Management Key (M_Key): This protects device configuration integrity. The SM assigns a unique M_Key to each managed port during fabric initialization. Any subsequent management command attempting to modify that port's configuration must include the correct M_Key in the packet header, or the device silently drops the packet and can optionally send a "Bad M_Key" trap notification to the SM alerting it to potential attacks. M_Keys support lease periods that cause them to expire if the SM becomes unreachable, preventing stale keys from persisting indefinitely and creating security gaps.
SM_Key and Allowed GUIDs List: These prevent rogue SM takeover attacks where an attacker deploys a malicious Subnet Manager to gain fabric control. The SM_Key acts as a shared secret that must be presented during the mastership election process, ensuring only authorized SMs can compete for control. You can configure an allowed_sm_guids whitelist containing Global Unique Identifiers of trusted SMs, functioning as an access control list that blocks unknown SMs from participating in elections even if they possess the correct SM_Key.
Hardware GUIDs: Every InfiniBand device and port carries a 64-bit Global Unique Identifier burned into its hardware during manufacturing, creating an immutable identity that attackers can't spoof without physically replacing hardware components. You can configure the SM with a static topology file mapping expected GUIDs to specific physical ports, enabling the SM to verify not just that a device is authorized but that it's connected to the correct location. If a device with an unknown GUID appears, or a known GUID suddenly appears on an unexpected port, the SM refuses to configure it, preventing unauthorized device insertion and detecting cable misconnections.
2.2. Ethernet's Distributed Trust Model: 802.1X, MACsec, and Centralized Authentication Servers
Ethernet scatters trust. Its security model builds on open IEEE standards that create layered, distributed authentication mechanisms, often coordinated through centralized backend authentication servers that provide consistent policy enforcement across distributed control points, combining the benefits of centralized policy management with distributed enforcement that avoids single points of failure.
Key Components:
Port-Based Authentication (IEEE 802.1X): This delivers robust Network Access Control at the physical port level, creating an explicit gatekeeper that challenges every connecting device before granting network access. When a device connects to an 802.1X-enabled switch port, that port enters an "unauthorized" state that blocks all traffic except authentication packets, preventing the device from communicating with the network. The switch acts as an authenticator that relays credentials from the connecting device to a centralized authentication server running RADIUS or TACACS+ protocol. Only after the server validates those credentials and approves the connection does the switch transition the port to an "authorized" state that permits normal traffic flow.
Link-Layer Encryption (MACsec, IEEE 802.1AE): While 802.1X authenticates devices to your network, MACsec protects the actual data traveling across physical links from interception, tampering, and injection attacks. MACsec provides point-to-point encryption on Ethernet links, offering strong AES-GCM encryption, cryptographic integrity checks that detect any bit flips or packet modifications, and anti-replay protection using sequence numbers that prevent attackers from capturing and retransmitting valid packets. This protects against physical threats like fiber tapping, cable interception, and malicious devices inserted into network paths.
Centralized Authentication (RADIUS/TACACS+): These protocols provide the backend Authentication, Authorization, and Accounting infrastructure that supports the distributed edge enforcement points created by 802.1X and MACsec. They enable centralized management of user and device credentials in databases like Active Directory or LDAP, providing consistent policy enforcement across hundreds of switches without manually configuring credentials on each device. TACACS+ often proves preferable in high-security environments because it encrypts the entire AAA packet including usernames, commands, and authorization attributes, whereas RADIUS only encrypts the password field, leaving other potentially sensitive information exposed to network eavesdropping.
The scope of authentication differs profoundly. InfiniBand's key-based mechanisms maintain the integrity of your predefined fabric topology, protecting against internal threats from compromised nodes or rogue administrators who attempt to reconfigure devices or inject unauthorized SMs. Ethernet's approach assumes zero trust—it challenges and verifies every device at the network edge through explicit 802.1X authentication and protects each physical link from breaches using MACsec encryption. For regulated environments requiring strict, auditable proof that only authorized devices accessed the network before receiving sensitive data, 802.1X's explicit gatekeeper role provides more direct, documentable, and legally defensible control than InfiniBand's topology-based trust model.
Practical Example: Verifying MACsec and 802.1X Configuration on Ethernet Switches
# Example Python code to audit MACsec and 802.1X configuration across switches
# Useful for compliance and zero-trust enforcement in AI fabrics
import json
def verify_ethernet_security(config_path):
with open(config_path) as f:
switches = json.load(f)
for sw in switches:
macsec = sw.get('MACsec_enabled', False)
dot1x = sw.get('8021X_enabled', False)
if not macsec or not dot1x:
print(f"WARNING: Switch {sw['name']} missing security config (MACsec: {macsec}, 802.1X: {dot1x})")
else:
print(f"Switch {sw['name']} OK (MACsec: {macsec}, 802.1X: {dot1x})")
This script provides a simple framework for network engineers to programmatically audit switch configurations, ensuring critical security controls like MACsec and 802.1X remain consistently enforced across all fabric components. It integrates easily into larger automation workflows using Ansible, Terraform, or custom orchestration platforms, enabling continuous compliance validation that detects configuration drift before it creates security gaps—a key practice for maintaining zero-trust enforcement in dynamic AI environments where infrastructure changes frequently and manual verification becomes impractical.
Section 3: Tenant Isolation: A Comparative Analysis of Enforcement Mechanisms
Isolation matters critically. In multi-tenant environments like sovereign AI clouds and shared regulated workloads, robust isolation transcends being merely a desirable feature—it represents a fundamental security requirement that protects national secrets, healthcare data, financial transactions, and intellectual property. You must prevent tenants from accessing each other's resources, intercepting each other's traffic, or even detecting each other's existence on shared infrastructure. InfiniBand and Ethernet achieve this essential isolation through fundamentally different technical mechanisms that create different security properties and attack surfaces. InfiniBand depends on hardware-enforced partitions baked into silicon. Modern Ethernet leverages software-defined network virtualization implemented through overlay encapsulation protocols.
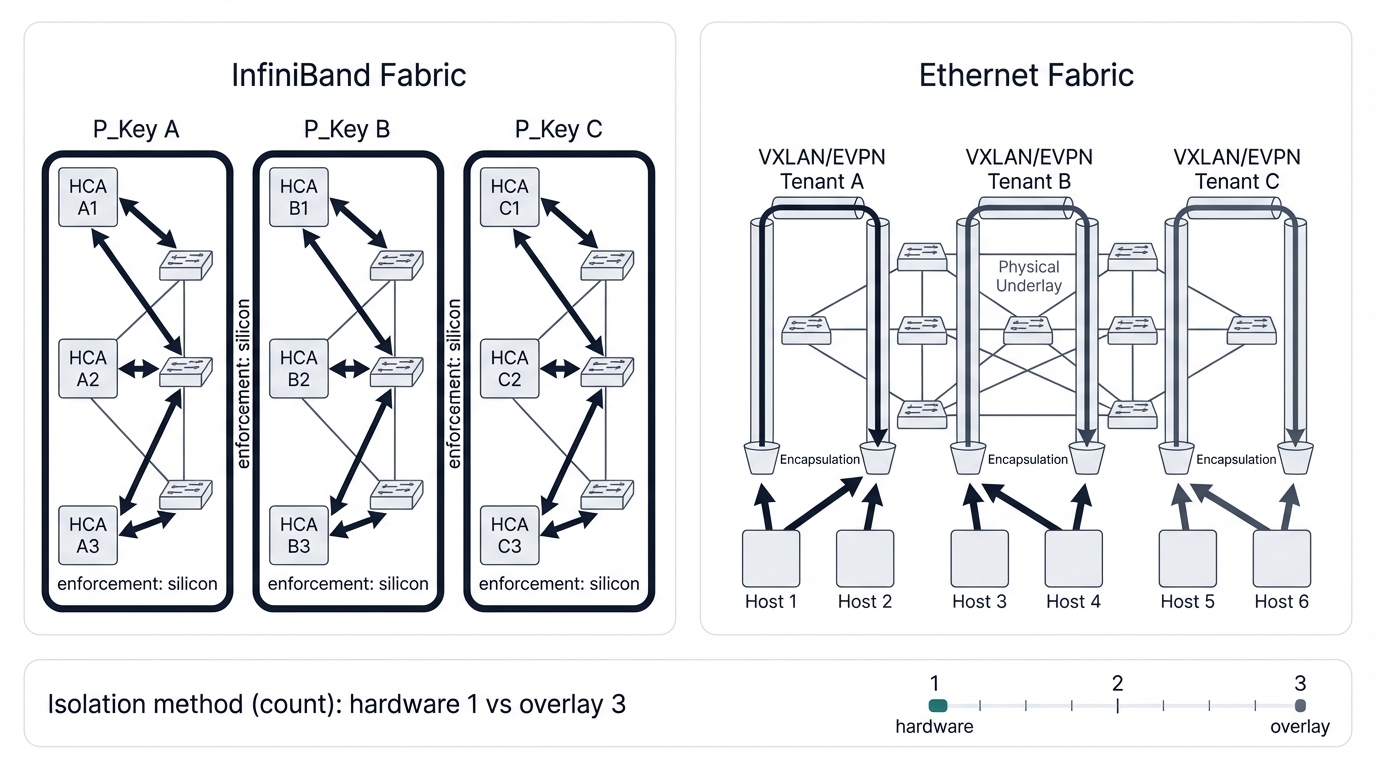
3.1. InfiniBand Partitions (P_Keys): Silicon-Enforced Segmentation
Partitions define boundaries. The Partition Key (P_Key) serves as InfiniBand's primary tenant isolation mechanism, functioning like a VLAN but enforced in hardware at wire speed with zero performance penalty. Think of a partition as a virtual fabric—a defined group of HCA ports authorized to communicate with each other while remaining completely isolated from ports in other partitions. The Subnet Manager creates these partitions during fabric initialization and assigns unique 16-bit P_Keys to ports on different compute nodes, storage systems, and switches based on tenant membership and security policies.
Enforcement happens in silicon. Every data packet transmitted across InfiniBand includes a 16-bit P_Key in its header identifying the partition it belongs to. When switches or HCAs receive packets, their hardware checks this P_Key against the configured list of allowed keys for that specific port, dropping packets with mismatched keys instantly with no forwarding, no logging, and no performance impact. This hardware-level enforcement ensures traffic isolation remains robust even under extreme load, preventing one tenant's traffic surge from creating opportunities to breach another tenant's partition.
InfiniBand adds granularity through "full" and "limited" membership modes that create hierarchical isolation within partitions:
- Full membership: Grants unrestricted bidirectional communication with any other member within the same partition, suitable for trusted infrastructure components
- Limited membership: Restricts communication to full members only, preventing limited members from communicating directly with each other
This creates powerful security patterns where compute nodes receive limited partition membership that allows them to access central storage servers granted full membership, but prevents lateral communication between compute nodes that might belong to different security domains or untrusted users within the same tenant organization.
But metadata leaks. Despite robust data plane isolation, InfiniBand suffers a significant security weakness in the management plane—metadata leakage that violates multi-tenant isolation principles. While data packets respect partition boundaries strictly, management and diagnostic protocols don't necessarily enforce the same isolation. Network diagnostic tools like ibnetdiscover can often reveal detailed information about the entire physical fabric topology, including nodes in other tenants' partitions, exposing device GUIDs, Local Identifiers (LIDs), connection topology, and switch configurations that should remain invisible to tenants. This metadata disclosure gives potential attackers detailed reconnaissance information that maps tenant locations, identifies high-value targets, and reveals infrastructure patterns useful for planning sophisticated attacks.
3.2. Ethernet Virtual Overlays (VXLAN/EVPN): Encapsulation-Based Segmentation
Ethernet virtualizes differently. Modern high-performance Ethernet achieves tenant isolation through network virtualization protocols, most commonly Virtual Extensible LAN (VXLAN), that create logical overlay networks operating independently above the physical network infrastructure, allowing multiple tenants to share the same switches, cables, and routers while maintaining complete traffic and metadata isolation.
VXLAN works through encapsulation. It wraps each tenant's native Layer 2 Ethernet frames inside standard UDP/IP packets that traverse the physical network infrastructure, functioning like tunnels that carry tenant traffic invisibly through shared hardware. Each tenant's isolated network receives a unique 24-bit VXLAN Network Identifier (VNI) embedded in the encapsulation header, supporting up to 16 million distinct tenant networks—vastly exceeding traditional VLAN limits of approximately 4,000 segments. This encapsulation creates a completely private, logical Layer 2 network for each tenant that operates independently of physical topology, allowing tenants to design their own addressing schemes, subnet structures, and Layer 2 domains without coordination or conflict.
Control planes manage scale. Large-scale VXLAN deployments typically leverage BGP-EVPN, a sophisticated control plane protocol that distributes MAC address reachability information and builds efficient forwarding tables across the fabric. Devices called VXLAN Tunnel Endpoints (VTEPs) handle the encapsulation and decapsulation operations, learning tenant device locations through BGP-EVPN rather than inefficient broadcast-based learning that creates scalability and security problems. VTEPs maintain separate forwarding tables for each VNI, ensuring traffic destined for one tenant never leaks into another tenant's network even if MAC addresses or IP addresses accidentally overlap.
Security depends on VTEP integrity. While VXLAN provides strong isolation, it's not perfectly invulnerable to all attacks—security ultimately depends on the trustworthiness of VTEPs and the integrity of the BGP-EVPN control plane. Common Layer 2 attacks like ARP spoofing, MAC flooding, and DHCP starvation can still threaten security within a single tenant's VNI, requiring defense-in-depth controls within tenant networks. However, attacks attempting to breach the encapsulation boundary and cross between different VNIs are fundamentally prevented by the architecture because the VNI is cryptographically bound to the encapsulation header, making cross-tenant attacks require either VTEP compromise or BGP-EVPN control plane manipulation rather than simple packet crafting.
3.3. Synthesis: Robustness, Scalability, and Vulnerabilities in Multi-Tenant Isolation
Trade-offs define choices. InfiniBand's P_Key mechanism delivers rock-solid data plane isolation through hardware enforcement that operates at line rate with zero performance penalty, making it ideal for scenarios demanding absolute certainty that tenant traffic cannot cross partition boundaries regardless of software bugs, configuration errors, or DoS attacks that overwhelm forwarding engines. Ethernet with VXLAN sacrifices that hardware-level guarantee in exchange for dramatically superior scalability that supports up to 16 million isolated network segments and flexibility that allows tenant networks to span any Layer 3 routable infrastructure including geographically distributed data centers connected by WAN links or internet VPNs.
The fundamental difference is what gets protected: traffic versus metadata. InfiniBand excels at isolating actual data packets through partition enforcement, ensuring tenant A's traffic never reaches tenant B's HCAs even if attackers compromise switches or inject malicious packets. But it struggles with preventing tenants from discovering each other's existence, port assignments, topology connections, and device identities through management plane tools that expose fabric-wide metadata—information that violates fundamental multi-tenancy principles requiring tenants remain unaware of each other's presence.
VXLAN flips the equation. Within their VNI, tenants see only their own logical Layer 2 domain with complete visibility into their own devices and traffic patterns, but they remain absolutely blind to other tenants, the underlying physical network topology, shared switch infrastructure, and even the fact they're running on virtualized overlay networks rather than dedicated hardware. This delivers superior metadata protection that aligns with strict multi-tenancy security models. However, traffic isolation security ultimately depends on VTEP implementations correctly enforcing VNI boundaries—if VTEP software contains bugs or attackers compromise VTEP control through software vulnerabilities or credential theft, they could potentially inject traffic into wrong tenant networks or extract traffic from VNIs they shouldn't access.
Context drives decisions. In environments like government AI clouds processing classified workloads or highly regulated industries handling sensitive patient health records, preventing tenants from discovering each other's existence (metadata isolation) often outweighs concerns about sophisticated VTEP compromise scenarios. While VXLAN's security model requires trusting the VTEP implementation and BGP-EVPN control plane, its architectural approach more effectively supports the stringent "tenant invisibility" requirements that define modern multi-tenant security in cloud and shared infrastructure environments.
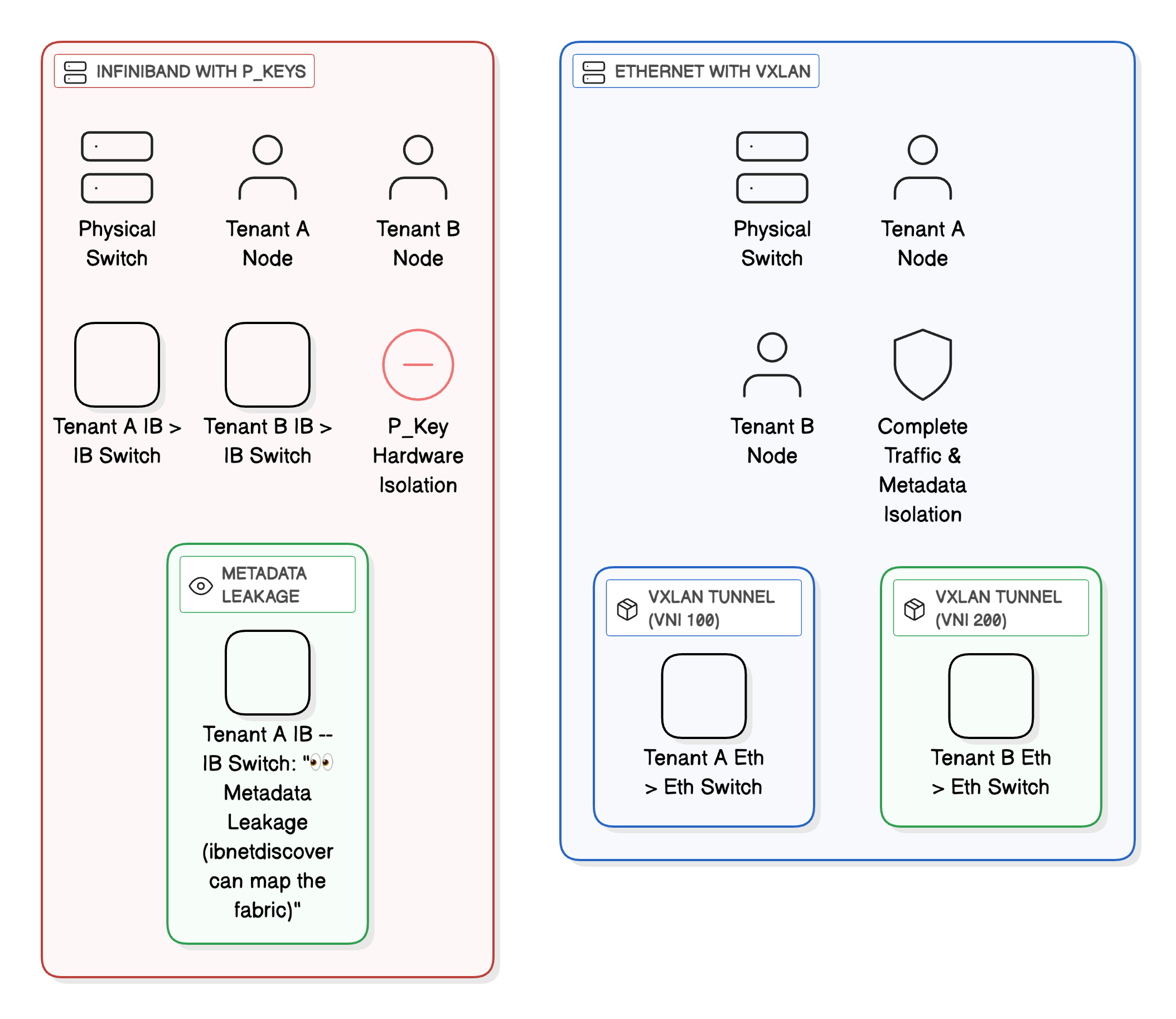
Figure 2: Tenant isolation comparison showing InfiniBand's P_Key hardware isolation with metadata leakage versus Ethernet's complete traffic and metadata isolation via VXLAN tunnels
Section 4: Quality of Service (QoS) as an Attack Vector
QoS becomes weaponized. Quality of Service mechanisms provide essential functionality in high-performance fabrics by managing congestion, prioritizing latency-sensitive traffic, and ensuring fair resource allocation among competing applications and tenants. But these same mechanisms create opportunities for malicious actors or misconfigured systems to launch devastating denial-of-service attacks that starve legitimate users of network resources or destabilize the entire fabric through cascading failures. The attack patterns differ dramatically between InfiniBand and Ethernet due to their fundamentally different approaches to QoS implementation and congestion management protocols.
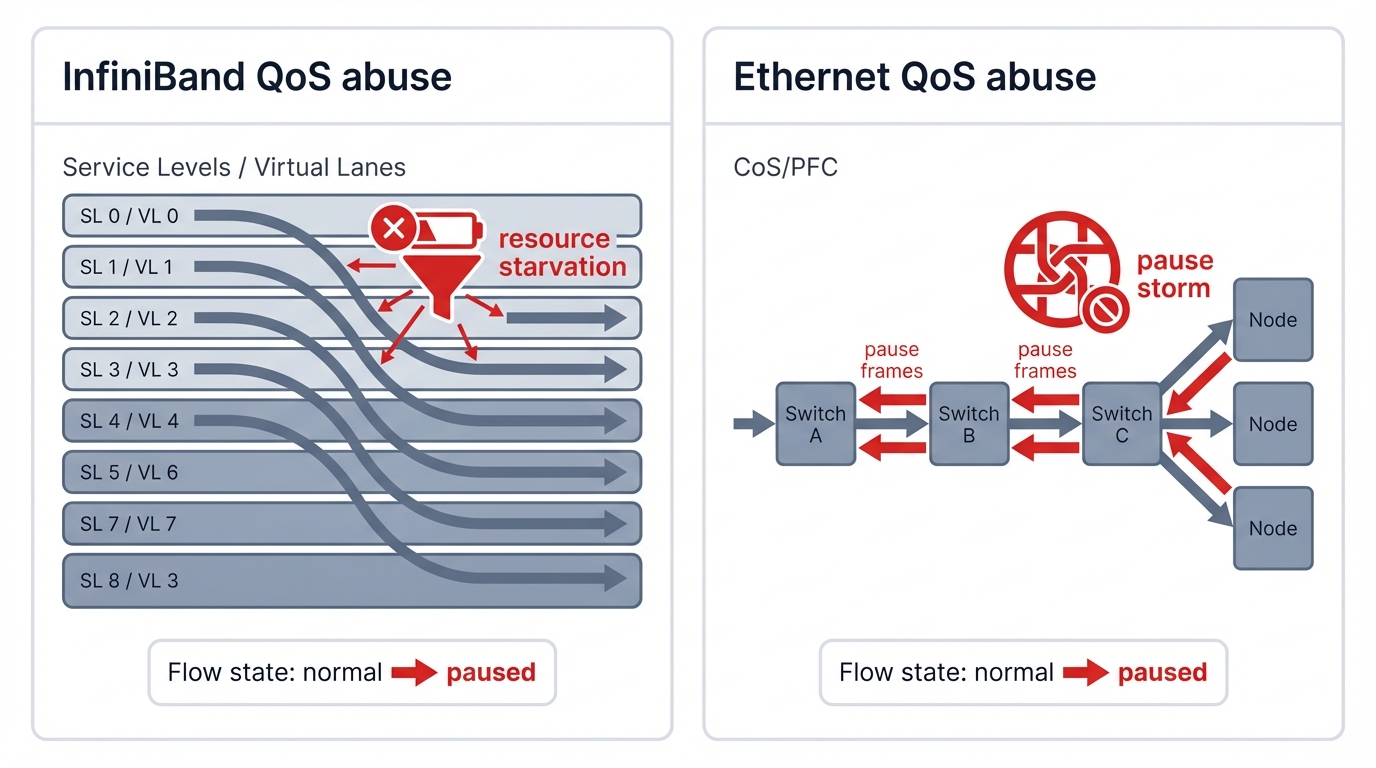
4.1. InfiniBand QoS Abuse: Manipulating Service Levels and Virtual Lanes for Resource Starvation
Service Levels define priority. InfiniBand's QoS architecture revolves around Service Levels (SLs) ranging from 0 to 15 that classify traffic into priority classes, and Virtual Lanes (VLs) that provide separate buffer queues and scheduling resources within switches. The source HCA marks each packet with a 4-bit SL value indicating its priority. As packets traverse switches, the SL combines with input and output port identifiers to determine which VL carries that packet, with separate VLs receiving dedicated buffer space and configurable shares of link bandwidth through weighted arbitration.
Resource starvation threatens here. A compromised tenant or malicious application could mark all its traffic with the highest-priority SL value, attempting to monopolize high-priority VL resources and starve other tenants' traffic. If your fabric's QoS policy lacks sufficient granularity, strictness, or enforcement mechanisms, this high-priority flood could consume VL buffers, dominate scheduling arbiters, and force legitimate high-priority traffic from other tenants into lower-priority VLs where it experiences increased latency, reduced bandwidth, and potential packet drops that violate service level agreements.
Countermeasures require SM vigilance. Defense depends entirely on centralized policy enforcement by the Subnet Manager through robust QoS configurations including strict SL-to-VL mapping tables that control which SLs can use which VLs on each port, carefully tuned arbiter weights that allocate bandwidth shares among VLs based on organizational priorities, and per-partition SL restrictions that prevent tenants from using SL values reserved for infrastructure or higher-priority tenants. The architecture prevents hosts from arbitrarily modifying fabric-level QoS settings because only the SM possesses the management keys needed to configure switches. Additionally, InfiniBand's hardware-based credit-driven link-level flow control makes it inherently resistant to common Layer 2/3 DoS attacks like SYN floods, UDP floods, and ICMP storms that typically get dropped by HCA hardware before involving the host operating system or consuming significant resources.
4.2. Ethernet QoS Abuse: Exploiting CoS/PFC for Denial-of-Service and Congestion Attacks
Ethernet creates bigger problems. Ethernet QoS relies on Class of Service (CoS) markings using 3-bit 802.1p priority values embedded in VLAN tags and Differentiated Services Code Point (DSCP) values using 6-bit fields in IP headers, both of which classify traffic into different queue classes on switches and routers. While general QoS misconfigurations can cause resource starvation similar to InfiniBand's SL abuse, RoCEv2's critical dependence on Priority Flow Control (PFC) creates a uniquely dangerous and potentially catastrophic attack surface that can deadlock entire fabric segments.
PFC enables destruction. Priority Flow Control implements a reactive backpressure mechanism designed to create lossless Ethernet fabrics by preventing buffer overflow. When a switch's ingress buffer for a specific priority class approaches capacity, it sends a PFC "pause" frame to the upstream switch, instructing it to temporarily halt transmission of packets in that priority class. Under normal conditions, this prevents packet loss. Under attack, it enables cascading fabric collapse.
An attacker can generate sustained, massive bursts of traffic classified into a single RoCEv2 priority class, deliberately filling buffers across the fabric. This triggers exponentially spreading pause frames that propagate backward through your network topology like a destructive shockwave:
- Buffer Pressure and Head-of-Line Blocking: Paused flows consume enormous amounts of expensive switch buffer memory in upstream devices, and if buffers aren't strictly partitioned by priority class, the paused traffic can create head-of-line blocking that impacts completely unrelated traffic classes, degrading performance across the entire fabric even for tenants and applications that weren't directly targeted.
- PFC Deadlocks: In complex topologies like Clos fabrics with multiple parallel paths and ECMP load balancing, attackers can deliberately craft traffic patterns that create circular buffer dependencies where Switch A pauses Switch B, which pauses Switch C, which pauses Switch A, forming a deadlock cycle where no switch can drain its buffers because all upstream switches are also paused. This results in a "hard" denial-of-service where absolutely no traffic in the affected priority class can move anywhere in the fabric, effectively freezing critical AI training jobs, distributed storage replication, or real-time inference workloads that depend on that priority class—a catastrophic failure mode that requires manual intervention to resolve.
Countermeasures demand architectural excellence. Defense requires meticulous network design and configuration including careful buffer sizing on every switch that provides enough headroom to absorb transient bursts without triggering PFC, precise tuning of PFC and ECN thresholds that trigger congestion response early enough to avoid buffer exhaustion, strict QoS policies that correctly classify application traffic and police tenant traffic to prevent one tenant from flooding priority classes, and ideally deployment of advanced switch architectures using Virtual Output Queueing (VOQ) that fundamentally prevent head-of-line blocking by maintaining separate queues for each output port, eliminating many of the buffer contention scenarios that enable PFC deadlocks.
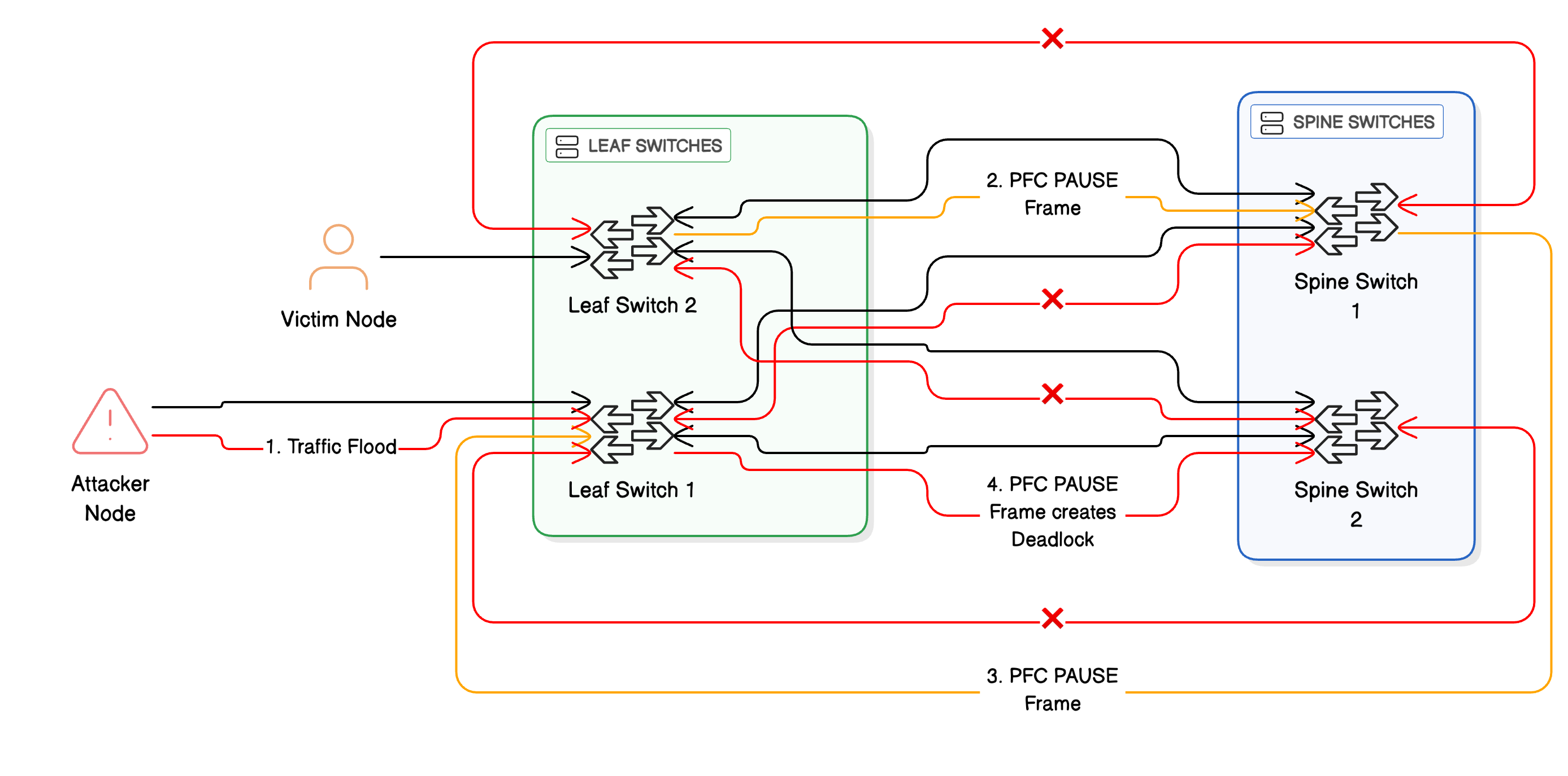
Figure 3: PFC deadlock attack demonstration showing how an attacker can flood traffic to create cascading pause frames that deadlock the entire fabric topology
The failure modes matter strategically. InfiniBand's QoS architecture tends toward "graceful degradation" where attacks lead to unfair resource allocation and priority inversion, reducing performance for some tenants but maintaining fundamental fabric stability and allowing infrastructure teams to identify and mitigate the attack without complete service outage. Ethernet's PFC-dependent architecture, if not perfectly designed, configured, and monitored, becomes susceptible to more brittle "unstable collapse" failure modes where cascading pause frames or circular buffer dependencies create sudden, catastrophic fabric freezes affecting all tenants. For critical systems where predictable behavior under attack matters more than peak performance—think national security AI systems, healthcare inference platforms, or financial trading networks—this fundamental difference in risk profile should heavily influence your fabric selection decision.
Section 5: Telemetry Integrity: Ensuring Trustworthy Fabric Observability
Telemetry reveals truth. The collection of performance counters, event logs, traffic statistics, and diagnostic information provides vital capabilities for managing network health, troubleshooting performance issues, capacity planning, and detecting security anomalies before they escalate into breaches. But telemetry integrity matters enormously—if attackers can tamper with monitoring data, inject false metrics, or spoof event logs, they effectively blind administrators while hiding their malicious activities, misleading incident response teams, and undermining your entire security monitoring framework built on assumptions that telemetry data reflects reality. InfiniBand and Ethernet present fundamentally different challenges and solutions for ensuring telemetry trustworthiness, stemming from their respective integrated ecosystem versus open standards approaches.
5.1. Securing InfiniBand Telemetry: Protecting the SM-Agent Channel and Verifying Hardware Counters
Integration creates coherence. InfiniBand telemetry systems embrace tight coupling and centralized management architectures. Each switch and Host Channel Adapter runs embedded management agents called Subnet Manager Agents (SMAs) that continuously collect detailed statistics including port bandwidth utilization, packet error rates, buffer overflow events, and congestion indicators measured by specialized hardware counters. These agents report data to the central Subnet Manager and often feed into sophisticated management platforms like NVIDIA's Unified Fabric Manager that provide visualization, alerting, and historical analysis.
Traps provide real-time alerts. A powerful feature is the "trap" mechanism where agents send asynchronous alert notifications to the SM whenever unusual or potentially problematic events occur—port state changes, excessive error rates, security violations like M_Key failures, or environmental issues like temperature alarms—providing real-time visibility into fabric health and highlighting potential security incidents as they unfold rather than requiring administrators to poll devices continuously or analyze logs retroactively.
But channel security remains unclear. The significant challenge is securing the communication channel between distributed SMAs and the central SM, which occurs over a dedicated management queue pair called QP0 that carries Subnet Management Packets through the InfiniBand fabric itself. While mechanisms like Management Keys authenticate and authorize configuration changes sent to SMAs, the specifications remain frustratingly ambiguous about whether telemetry reports themselves are cryptographically signed, integrity-protected, or otherwise secured against tampering by compromised hosts. If a host with appropriate privileges falls to attackers, they could potentially inject false trap notifications claiming other nodes are failing, manipulate reported performance counters to hide traffic anomalies, or modify telemetry data to conceal their presence and activities. This risk intensifies due to kernel bypass architecture that renders management traffic invisible to traditional host-based security monitoring tools like endpoint detection agents, system call monitors, or network packet analyzers.
Endpoint security becomes critical. Mitigation focuses on hardening the communication endpoints—particularly the Subnet Manager itself which must run on physically secured, carefully hardened infrastructure with minimal attack surface, restricted administrative access through multi-factor authentication and privilege separation, and network isolation on dedicated management VLANs protected by firewalls and intrusion detection systems. Features like the SMP firewall on modern HCAs can prevent unauthorized hosts from sending management packets at all, blocking compromised compute nodes from injecting false telemetry. Additionally, modern InfiniBand adapters incorporate hardware security features including secure boot that validates firmware integrity, hardware roots of trust using TPM-like technology, and cryptographic attestation that proves the adapter is running authentic, unmodified firmware rather than malicious replacements.
5.2. Securing Ethernet Telemetry: Integrity in a Diverse Ecosystem
Ethernet sprawls. The Ethernet ecosystem offers a rich diversity of standardized telemetry protocols, each optimized for different use cases and deployment scenarios:
- NetFlow and IPFIX: Provide detailed flow records capturing source/destination addresses, ports, protocols, byte counts, and timing information for every conversation traversing the network
- sFlow: Delivers real-time traffic visibility through statistical packet sampling that scales efficiently to high-speed links without overwhelming collectors
- Streaming telemetry: Pushes continuously updated, fine-grained operational data directly from network devices to collectors using efficient encoding
Diversity enables flexibility. This variety allows organizations to select protocols matching their specific monitoring requirements, vendor ecosystems, and operational workflows, fostering innovation and preventing vendor lock-in that constrains architectural evolution. However, security wasn't paramount. Many of these protocols were designed during eras prioritizing interoperability, performance, and simplicity over security, and they typically transmit data unencrypted over UDP by default, making telemetry streams vulnerable to interception by network eavesdroppers, spoofing where attackers inject false data, and tampering where attackers modify legitimate telemetry in transit to hide their activities or frame innocent systems.
Securing telemetry requires layers. Organizations must explicitly add protection through multiple complementary mechanisms including encryption of telemetry streams using IPsec or TLS tunnels between devices and collectors that prevent interception and detect tampering, authentication of telemetry sources using certificates or pre-shared keys that verify data actually came from legitimate network devices rather than attacker-controlled systems, and physical security controls that prevent attackers from connecting rogue devices to wired network segments where they could inject or intercept telemetry traffic—a threat substantially more difficult than attacking wireless networks.
Trust models diverge fundamentally. InfiniBand's telemetry infrastructure rests on a closed, proprietary management ecosystem designed with security considerations but fundamentally opaque to external verification—organizations must trust that NVIDIA and other vendors implemented security correctly because they cannot independently audit firmware source code, cryptographic implementations, or management protocols. Ethernet telemetry relies on open, transparent, publicly documented standards that anyone can verify, audit, and independently implement, but security is never guaranteed by default and depends entirely on organizations properly deploying encryption, authentication, and access controls that the standards enable. For organizations requiring high assurance, strict accountability, and independent auditability—particularly government agencies, critical infrastructure operators, and regulated industries—the explicit, verifiable security measures of well-implemented Ethernet telemetry architectures may provide more trustworthy foundations than InfiniBand's opaque trust-us approach, despite requiring substantially more security engineering effort.
Section 6: Implications for Sovereign AI and Regulated Environments
Stakes transcend performance. Your choice of network fabric for sovereign AI initiatives and regulated industries extends far beyond technical performance specifications, latency benchmarks, or bandwidth capabilities—it directly impacts your nation's technological autonomy, ability to audit critical infrastructure for security and compliance, and capacity to enforce data residency and security mandates without dependence on foreign technology providers. The profoundly different security models embodied by InfiniBand and Ethernet create implications that ripple through national security strategies, regulatory compliance frameworks, and long-term economic competitiveness in these high-stakes contexts.
6.1. Meeting the Demands of Sovereign AI: Data Residency, Control Plane Sovereignty, and Verifiable Isolation
Sovereignty defines independence. Sovereign AI represents your nation's capability to develop, deploy, control, and govern its own artificial intelligence technologies and underlying infrastructure without dependence on foreign entities, ensuring sensitive training data, valuable AI models, and strategic inference workloads remain subject exclusively to your own laws, regulations, and national interests. This concept builds upon foundational principles of data sovereignty (legal authority over data) and data residency (physical location of data), extending them to encompass control over the entire AI technology stack from semiconductors through networks to algorithms.
Control Plane Sovereignty and Vendor Diversity
Vendor concentration creates vulnerability. A critical but often overlooked aspect of technological sovereignty is avoiding dangerous dependency on a single foreign supplier for critical infrastructure components—particularly those that control, monitor, or can potentially manipulate your data flows. The InfiniBand market suffers near-total domination by NVIDIA following its strategic acquisition of Mellanox, creating profound supply chain risk and potential mechanisms for geopolitical leverage where your entire nation's AI research infrastructure, military AI systems, and government analytics platforms could become dependent on one company's hardware roadmaps, software update cadences, security patch responsiveness, and corporate strategic priorities that may not align with your national interests.
Ethernet fosters competition. By contrast, Ethernet thrives as a vibrant multi-vendor ecosystem built on open IEEE and IETF standards that enable genuine interoperability, allowing organizations to purchase switches from Arista, Cisco, Dell, or Huawei; network adapters from Intel, Broadcom, or Marvell; and orchestration software from open-source projects or multiple commercial vendors. This diversity naturally fosters healthy competition that reduces costs, accelerates innovation through differentiation rather than lock-in, and critically provides genuine supplier choice that mitigates single-vendor dependency risks. When geopolitical tensions rise, having alternative suppliers becomes a strategic asset rather than theoretical option.
Data Residency and Verifiable Isolation
Residency demands proof. Enforcing data residency requires not merely storing data within national borders on domestically located servers—it demands ironclad guarantees that tenants sharing infrastructure in multi-tenant sovereign clouds cannot access each other's data, monitor each other's traffic patterns, or even become aware of each other's existence through metadata leakage that reveals which government agencies, military units, or research institutions are utilizing the shared infrastructure.
InfiniBand fails metadata isolation. While P_Key mechanisms provide robust protection against data plane traffic crossing partition boundaries, the critical weakness in metadata isolation creates unacceptable risks for sovereign deployments. The ability for tenants to use diagnostic tools like ibnetdiscover to comprehensively map the entire fabric topology—discovering device identities, connection patterns, and partition structures—constitutes a significant information disclosure vulnerability in multi-tenant sovereign clouds where preventing reconnaissance is fundamental to security. Knowing which other agencies or contractors share your infrastructure leaks strategic information.
VXLAN delivers complete invisibility. Ethernet with VXLAN provides vastly superior metadata isolation by strictly confining each tenant's visibility to their own virtual network overlay, making it impossible for tenant A to discover that tenant B exists, determine what physical switches carry their traffic, map the underlying network topology, or identify connection patterns that reveal organizational relationships. This architectural characteristic better aligns with the stringent separation requirements of multi-tenant sovereign platforms where information about who uses the infrastructure is as sensitive as the data itself.
Auditability and Transparency
Trust requires verification. For infrastructure to be trusted by national governments, intelligence agencies, and regulatory authorities, it must be independently auditable by third parties who can verify security properties without depending on vendor assurances or proprietary implementations. Ethernet's reliance on open, meticulously documented protocols like IP routing, UDP encapsulation, BGP control planes, and standardized authentication makes its control plane and data plane fundamentally transparent to network analysis, allowing your national security agencies, independent auditors, and academic researchers to use standard protocol analyzers, open-source monitoring tools, and publicly available documentation to monitor traffic flows, verify security configurations, validate isolation properties, and detect anomalies without vendor cooperation.
InfiniBand obscures verification. The control plane implemented through proprietary Subnet Management Packets and centralized SM logic presents substantial challenges to independent third-party verification because critical security-relevant operations occur through undocumented protocols, proprietary firmware implementations, and closed-source management software that external auditors cannot fully analyze, verify, or trust without access to source code and detailed protocol specifications that vendors guard as trade secrets. This opacity creates fundamental barriers to achieving high assurance certification that national security applications demand.
6.2. Aligning with Regulated Workloads: A Compliance Mapping for HIPAA and PCI-DSS
Regulations mandate controls. Regulated industries operate under strict compliance frameworks that mandate specific security controls, audit trails, and technical safeguards designed to protect sensitive data from unauthorized access, modification, or disclosure. The Health Insurance Portability and Accountability Act (HIPAA) requires robust technical safeguards for electronic Protected Health Information including access control mechanisms, comprehensive audit trails, and transmission security that protects data in transit. The Payment Card Industry Data Security Standard (PCI-DSS) demands strong network segmentation isolating Cardholder Data Environments, firewall protections at network boundaries, and encryption protecting data during transmission across public or untrusted networks.
The table below maps these high-level regulatory requirements to each fabric's specific capabilities and limitations, revealing how architectural differences create different compliance challenges:
| Regulatory Requirement | Framework | InfiniBand Implementation & Analysis | Ethernet (RoCEv2) Implementation & Analysis |
|---|---|---|---|
| Network Access Control | HIPAA/PCI-DSS | P_Keys for data plane authorization. M_Keys for management plane. SM_Keys for control plane. Centralized policy via SM. Analysis: Strong, hardware-enforced but relies entirely on SM integrity and creates single point of failure. | 802.1X for port-level device authentication. ACLs on Layer 3 switches. Security Groups in VXLAN overlays. Analysis: Layered, distributed control with defense-in-depth. More operationally complex but offers resilience through multiple independent enforcement points. |
| Network Segmentation | PCI-DSS | Partitions (P_Keys) provide hardware-enforced Layer 2 isolation. Analysis: Extremely strong traffic isolation with zero performance penalty but suffers from weak metadata isolation allowing topology discovery. | VLANs (traditional) and VXLAN (modern, scalable) provide Layer 2-over-Layer 3 segmentation. Analysis: Excellent metadata isolation preventing tenant discovery and massive scalability. Enforcement ultimately depends on VTEP integrity. |
| Transmission Security | HIPAA/PCI-DSS | No native, standardized on-the-wire encryption in the protocol. Relies on application-level encryption or specialized proprietary hardware. Analysis: Critical gap for data-in-transit protection at fabric level that complicates compliance. | MACsec provides mature, standardized, line-rate link-layer encryption. IPsec can secure RoCEv2 traffic at network layer, though with performance overhead. Analysis: Multiple standardized encryption options readily available. |
| Audit Trails & Monitoring | HIPAA/PCI-DSS | Centralized logging and telemetry via UFM. Traps for fabric events. Analysis: Comprehensive and operationally simple but proprietary and opaque. Integrity relies on securing SM-agent channel. Invisible to host-based monitoring tools. | Diverse ecosystem: NetFlow/IPFIX, sFlow, Streaming Telemetry. Logs from switches/routers/firewalls. Analysis: Open, flexible, and independently verifiable, but requires explicit security implementation and integration effort across multiple tools. |
| Protect Against Vulnerabilities | PCI-DSS | Hardened transport implemented in hardware silicon reduces software attack surface. Centralized SM enables consistent patching. Analysis: Reduced software vulnerability exposure but completely dependent on single vendor's security response and patch availability. | Relies on OS/firmware security of diverse switches and NICs from multiple vendors. Ecosystem requires diligent patch management across vendors. Analysis: Larger potential attack surface but not dependent on single vendor's security posture or patch responsiveness. |
This detailed mapping reveals that while both fabrics can be configured and hardened to meet compliance objectives, Ethernet's layered security controls often map more directly and explicitly to the prescriptive requirements found in standards like HIPAA and PCI-DSS, potentially simplifying audit processes and compliance verification. The explicit requirement for transmission security finds native solutions in MACsec for Ethernet, whereas InfiniBand lacks comparable standardized, fabric-level encryption mechanisms, forcing organizations to implement application-layer encryption or deploy proprietary vendor-specific solutions that may not satisfy auditors looking for recognized standards compliance.
Section 7: Strategic Recommendations and Conclusion
Best Practice: Following these recommended practices will help you achieve optimal results and avoid common pitfalls.
Decisions echo forward. Your choice and implementation of high-performance network fabric for sovereign AI infrastructure or regulated workloads creates consequences that reverberate through decades of infrastructure evolution, vendor relationships, security postures, and operational capabilities. No universally "best" fabric exists—optimal selection emerges from rigorously analyzing trade-offs between InfiniBand's centralized simplicity and Ethernet's distributed resilience in the context of your specific threat model, regulatory requirements, team capabilities, and strategic objectives. Based on the comprehensive analysis presented earlier, here are strategic recommendations for organizations architecting these mission-critical deployments.
7.1. Hardening InfiniBand Fabrics for High-Assurance Deployments
The SM demands protection. For organizations selecting InfiniBand, security architecture must laser-focus on protecting the Subnet Manager as the fundamental trust anchor for your entire fabric security posture. Isolate and harden the SM by running it exclusively on physically secured devices in locked, access-controlled rooms with comprehensive physical security monitoring. All management access to the SM and switches' out-of-band management ports must be strictly restricted to dedicated, isolated management networks protected by firewalls enforcing deny-by-default policies, intrusion detection systems monitoring for anomalies, and multi-factor authentication for administrative access.
Key Hardening Steps:
Enforce Control Plane Authentication: Never use default SM_Keys in production environments—always configure strong, randomly generated SM_Keys to protect the mastership election process from rogue SM takeover attempts, and maintain a static allowed_sm_guids whitelist containing only the GUIDs of your authorized SM instances, blocking unknown SMs from participating in elections even if they somehow obtain the SM_Key through credential theft or social engineering.
Use Static Topology Files: Where operationally feasible, define your fabric topology in static configuration files that map expected device GUIDs to specific physical ports, switch locations, and rack positions, allowing the SM to verify not just device authorization but correct physical connectivity, preventing GUID spoofing attempts and detecting unauthorized device insertions, cable swaps, or physical tampering that changes fabric topology without authorization.
Mitigate Information Disclosure Aggressively: Deploy the SMP firewall feature on all HCAs to block tenant hosts from sending or receiving subnet management packets, preventing them from running diagnostic tools like ibnetdiscover and ibstat that map fabric topology beyond their authorized partition scope. This is absolutely critical to preventing tenants from conducting reconnaissance that maps other tenants' presence, locations, and network patterns.
Compensate for Lack of Native Encryption: Since InfiniBand fundamentally lacks standardized on-the-wire encryption at the fabric layer, security for data in transit must be explicitly enforced at the application layer using TLS/SSL encryption for application protocols or deploying application-specific encryption that protects data before it reaches the HCA. This requirement must be a primary architectural consideration documented in security architecture reviews, compliance audits, and risk assessments.
7.2. Architecting Secure and Resilient RoCEv2 Ethernet Fabrics
Resilience requires engineering. For organizations selecting Ethernet, the goal is architecting a genuinely lossless, low-latency network while simultaneously implementing comprehensive layered security that achieves defense-in-depth without introducing single points of failure. Design proactively for PFC resilience since the most dangerous threat to RoCEv2 fabric stability is PFC-based denial-of-service attacks that cascade into fabric-wide deadlocks. Your network design must include generous buffer provisioning on all switches that provides headroom to absorb transient microbursts, meticulous tuning of PFC and ECN thresholds that trigger early congestion response before buffers fill completely, strict QoS policies that classify and police tenant traffic preventing priority class flooding, and ideally deployment of modern switch architectures implementing Virtual Output Queueing that fundamentally prevents head-of-line blocking by maintaining separate queues per destination.
Key Architecture Steps:
Implement Comprehensive Layered Security Controls: Adopt a zero-trust architecture as your foundational security model. Mandate IEEE 802.1X for port-based admission control on every switch port, ensuring absolutely no unauthorized devices connect to your fabric without explicit authentication. Deploy MACsec for link-layer encryption on all inter-switch links and, where performance requirements permit, on host-facing ports as well, protecting against physical tapping, cable interception, and man-in-the-middle attacks.
Secure the Control and Overlay Planes Comprehensively: When deploying VXLAN with BGP-EVPN, secure all BGP sessions between network devices using strong authentication mechanisms like TCP MD5 signatures or more robust BGP Security (BGPsec) extensions that cryptographically validate routing updates. Implement rigorous control plane policing to protect switch CPUs from DoS attacks targeting routing protocol processing, preventing attackers from overwhelming switches with malicious BGP updates, VXLAN tunnel establishment requests, or ARP broadcasts.
Never Trust Telemetry by Default: Treat all telemetry streams as potentially compromised until proven otherwise. Every telemetry connection from network devices to collectors must be explicitly secured in transit using IPsec tunnels or TLS encryption that prevents tampering and verifies source authenticity, ensuring your observability infrastructure provides trustworthy data rather than attacker-manipulated fiction that blinds security teams while hiding malicious activity.
7.3. A Risk-Based Framework for Fabric Selection in Sovereign and Regulated Contexts
Context drives decisions. No fabric is universally "more secure" across all deployment scenarios, threat models, and organizational contexts. Your final architectural decision must emerge from rigorous risk assessment that prioritizes your specific deployment's strategic goals, regulatory requirements, threat landscape, and operational capabilities rather than generic performance benchmarks or vendor marketing claims.
For Sovereign AI Infrastructure
Independence demands Ethernet. The strategic imperatives of technological independence, verifiable security, and infrastructure auditability strongly favor Ethernet for national AI infrastructure supporting government agencies, military applications, critical research, and strategic industries. The vibrant multi-vendor ecosystem fundamentally reduces supply chain concentration risks and dangerous reliance on single foreign entities whose interests may diverge from national priorities during geopolitical tensions. Open, transparent, internationally standardized protocols enable independent auditing, verification, and security analysis by national authorities, academic institutions, and third-party auditors without requiring vendor cooperation or access to proprietary implementations. Most critically, the superior metadata isolation provided by VXLAN architectures proves essential for ensuring strict separation preventing different government agencies, military units, or commercial entities sharing a national AI cloud from discovering each other's existence, workload patterns, or infrastructure utilization—information that constitutes strategic intelligence in its own right.
For Regulated Workloads (HIPAA/PCI-DSS)
Compliance creates nuance. Your choice becomes more context-dependent, influenced by your organization's technical maturity, security team capabilities, operational complexity tolerance, and specific risk profile within the regulatory framework. Ethernet provides a security architecture with explicit layered controls that map directly to prescriptive requirements found in frameworks like PCI-DSS, potentially simplifying audit processes, compliance verification workflows, and security control validation that auditors understand. However, managing a genuinely secure, high-performance RoCEv2 fabric demands substantial expertise in network engineering, security architecture, and operational disciplines, and the catastrophic failure risk from PFC deadlocks cannot be dismissed lightly in environments supporting life-critical healthcare systems or financially material transaction processing.
InfiniBand offers operational simplicity through centralized management and a more predictable graceful degradation model under QoS attacks where performance suffers but fabric stability persists, which can prove advantageous for certain critical applications with stringent availability requirements. However, its fundamental security gaps—particularly the absence of native standardized encryption and susceptibility to metadata leakage—must be explicitly acknowledged in risk assessments and comprehensively mitigated through additional compensating controls that auditors and compliance officers must approve and validate during certification processes.
Final Thoughts
Trade-offs define reality. The security debate between InfiniBand and Ethernet ultimately highlights a classic architectural tension between integrated high-performance simplicity offering operational efficiency and layered flexible sovereignty-friendly security providing resilience through diversity. Choosing between them requires looking far beyond narrow performance benchmarks, latency measurements, or bandwidth specifications—it demands strategic decision-making rooted in deep analysis of architectural resilience under attack, security auditability for compliance and assurance, and fundamental alignment with the core goals of sovereignty, regulatory compliance, operational excellence, and long-term strategic flexibility that define organizational success in an increasingly complex threat landscape.
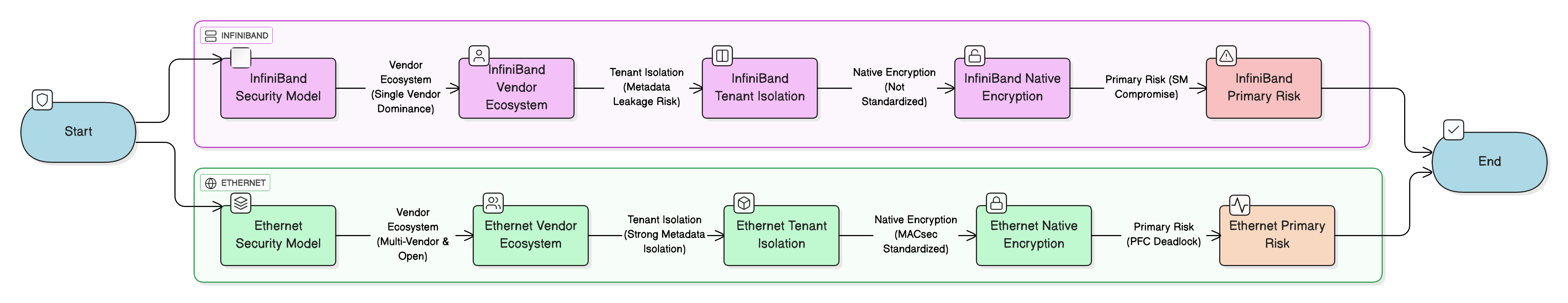
Figure 4: Risk assessment decision framework comparing InfiniBand's single vendor dominance and lack of encryption versus Ethernet's multi-vendor ecosystem and standardized security controls