Category
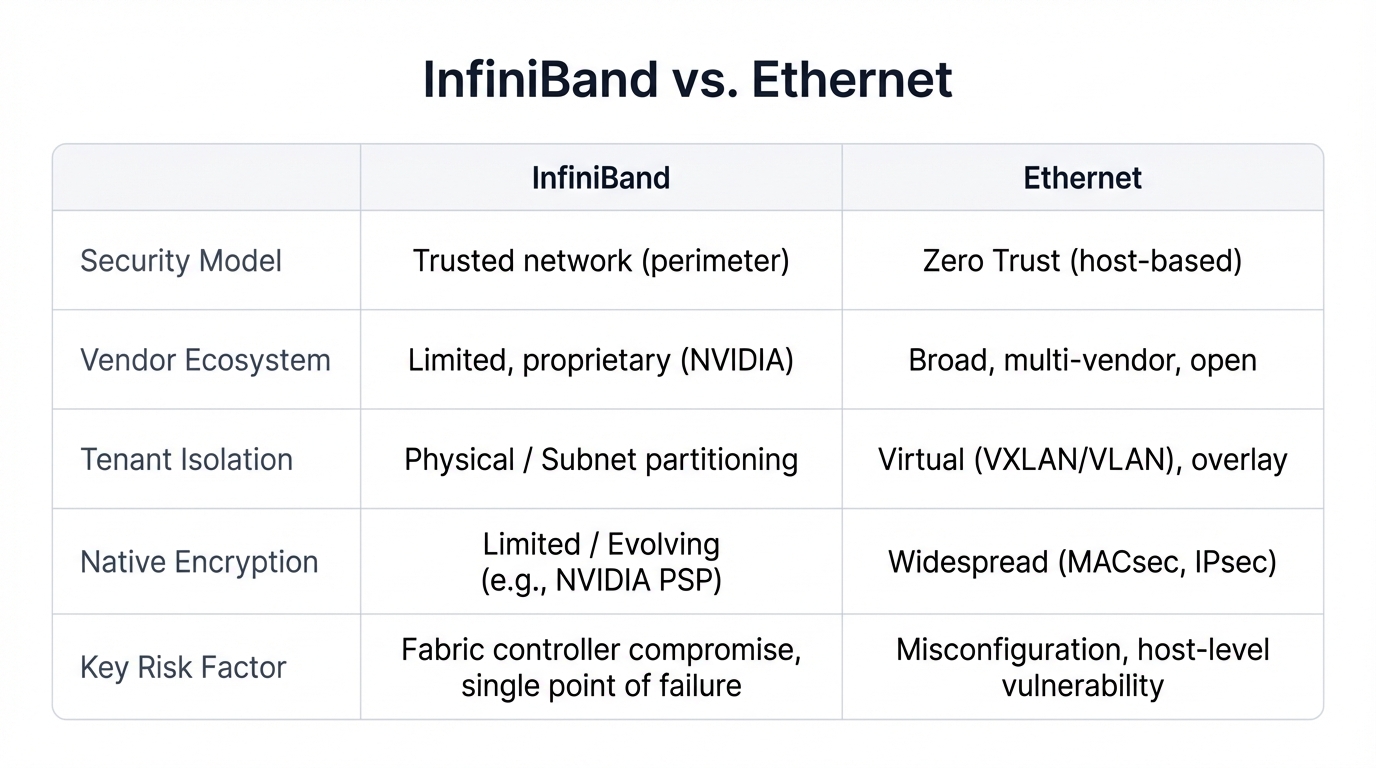
InfiniBand
Ethernet
Security Model
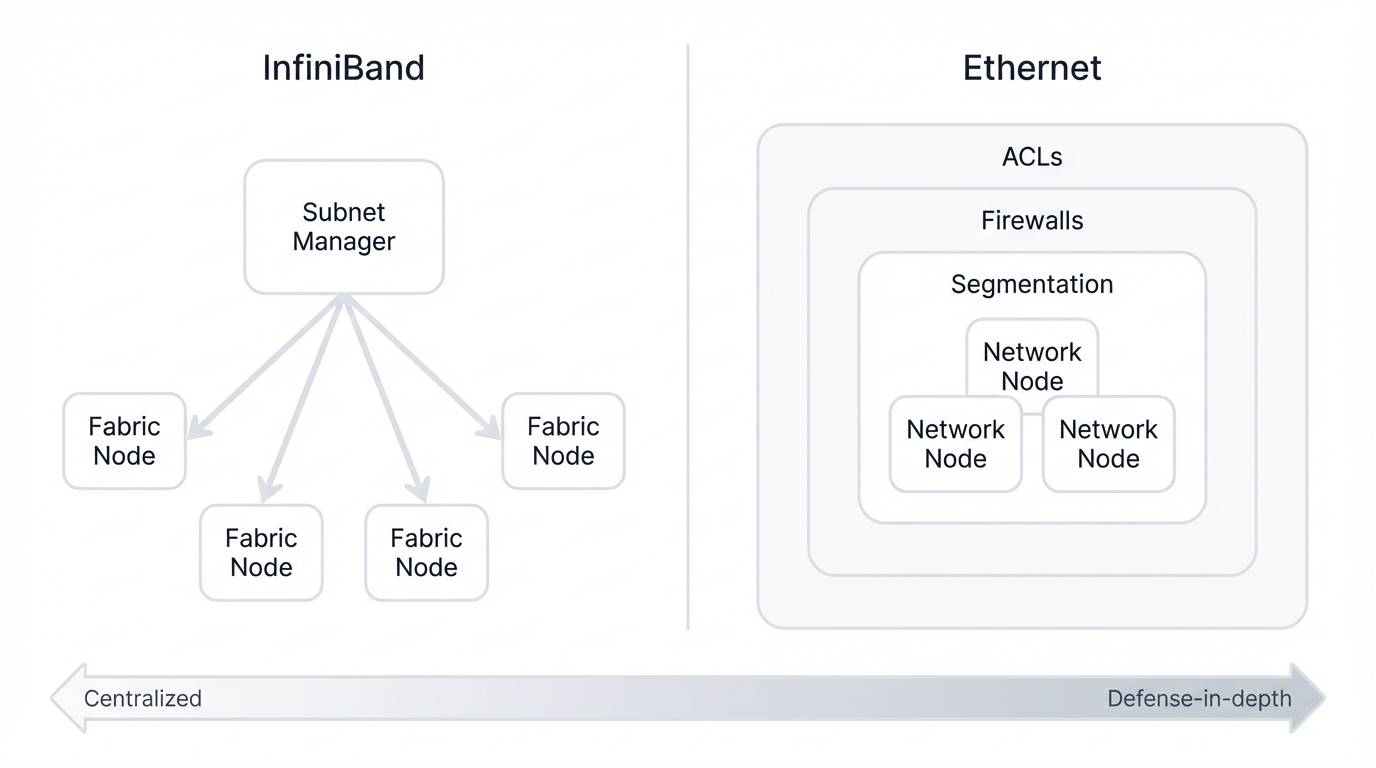
Centralized
Control is centralized in a single subnet manager, creating a single point of administration and potential failure.
Layered / Distributed
Security is managed across multiple layers (ACLs, firewalls, etc.), offering defense-in-depth but increasing complexity.
Vendor Ecosystem
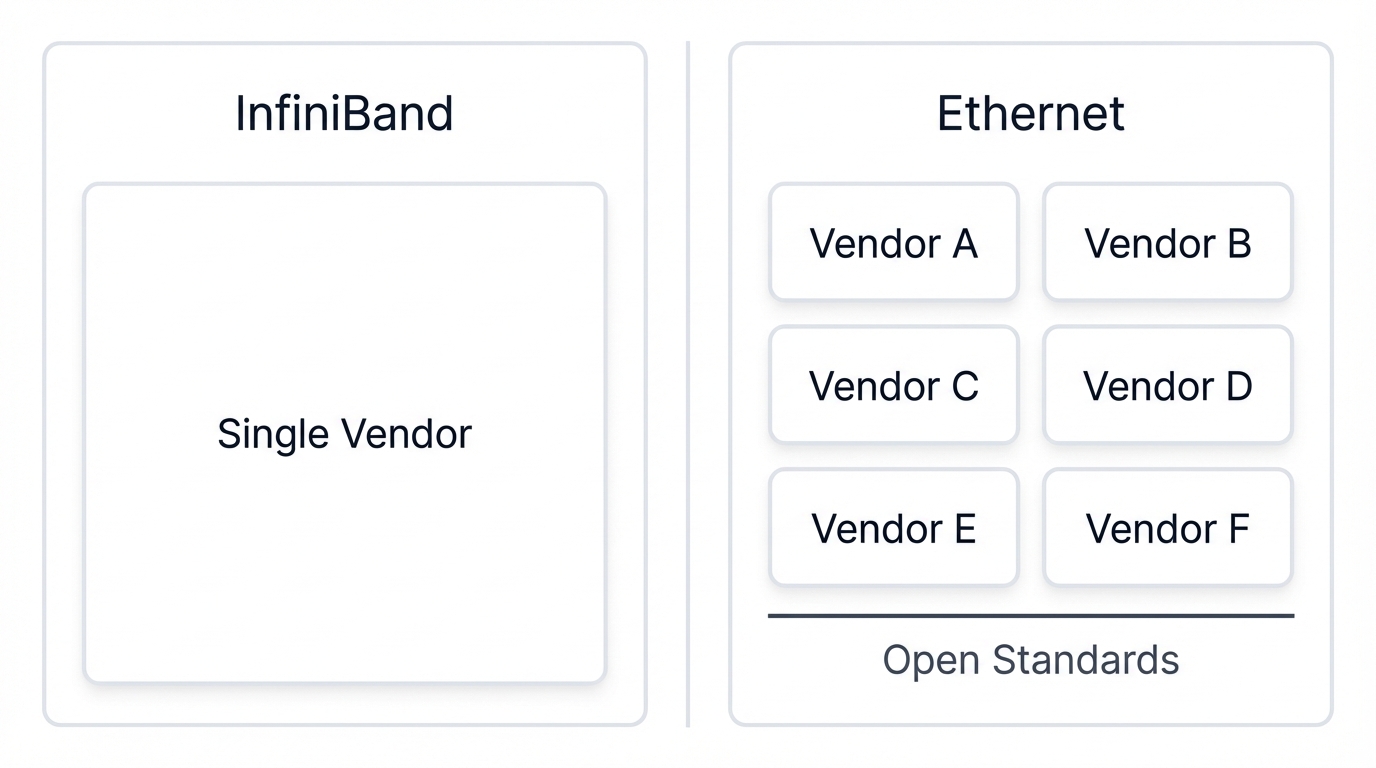
Vertically Integrated
Dominated by a single vendor, leading to tight integration but potential for vendor lock-in and limited choice.
Diverse & Open
A wide range of vendors promotes competition, innovation, and interoperability through open standards.
Tenant Isolation
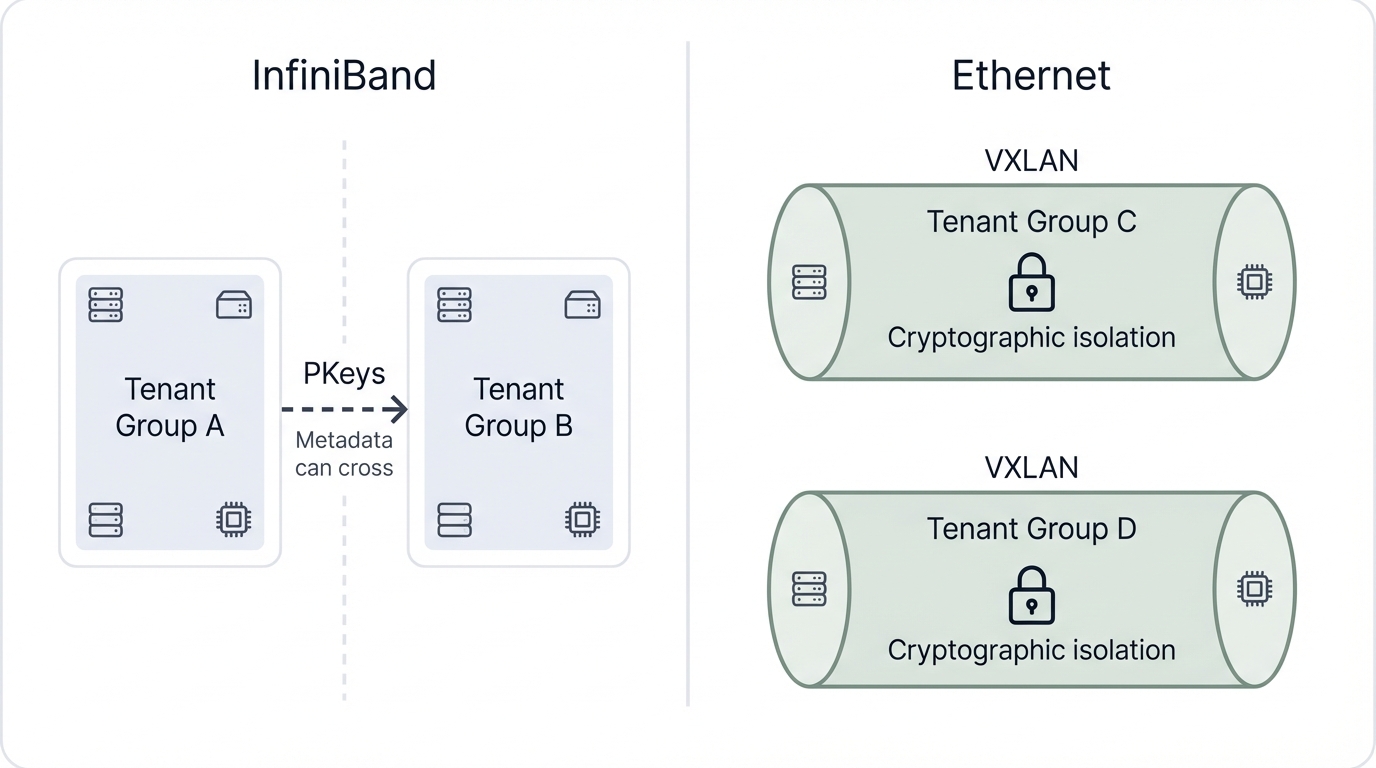
Partition Keys (PKeys)
Uses Partition Keys for isolation, but management traffic (metadata) can sometimes cross tenant boundaries.
VXLAN Tunnels
Encapsulates traffic in VXLAN tunnels, providing strong, cryptographically verifiable isolation between tenants.
Native Encryption
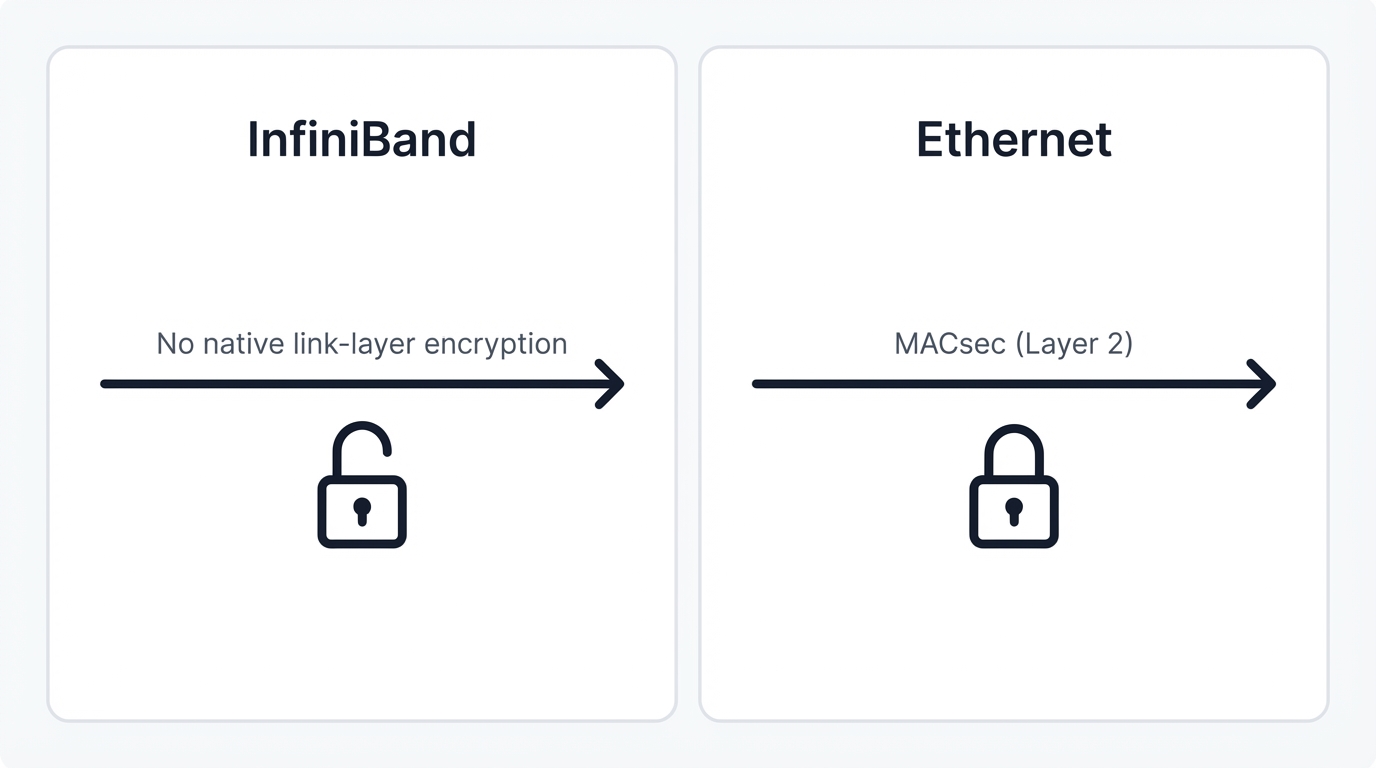
Not Standard
Lacks a native, standardized link-layer encryption protocol, requiring higher-layer solutions.
MACsec (802.1AE)
Includes MACsec as a standard for hop-by-hop encryption, securing data in transit at Layer 2.
Key Risk Factor
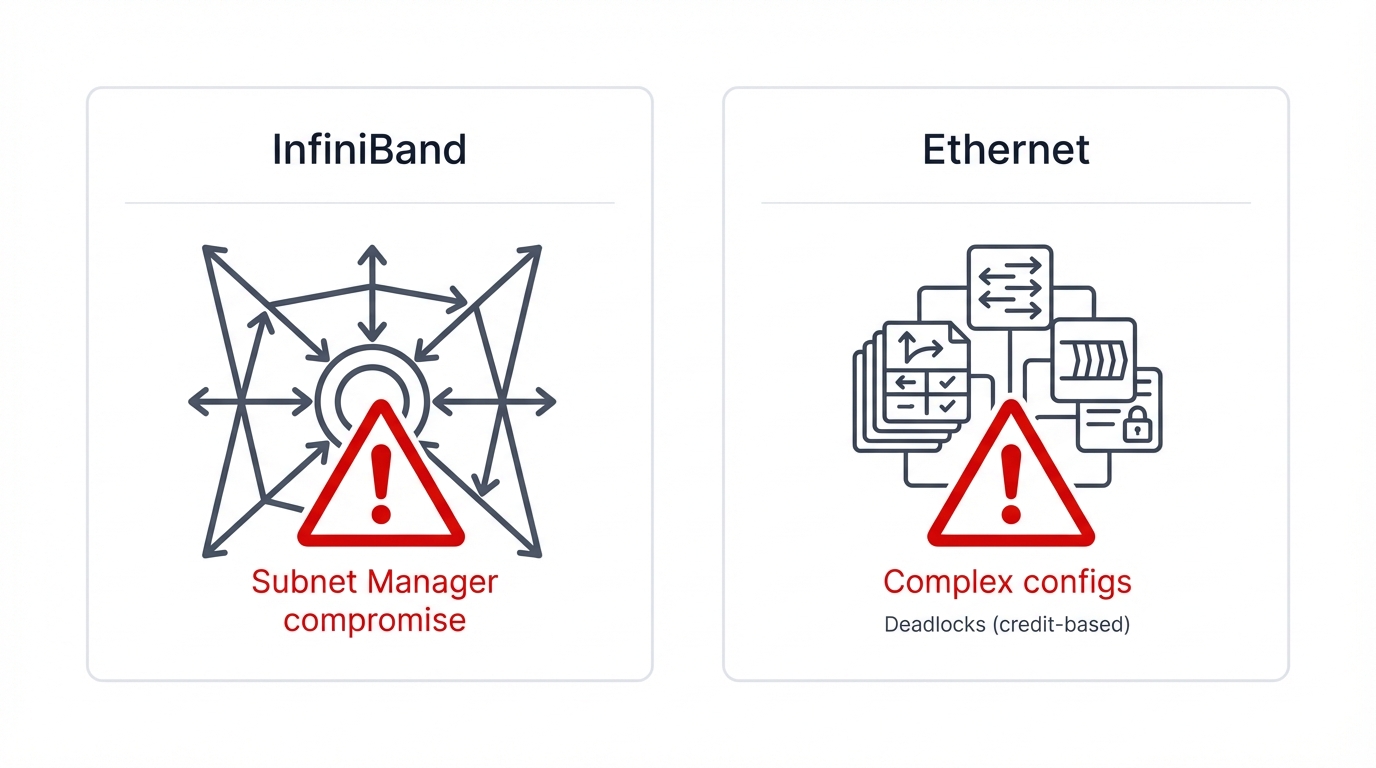
Single Point of Failure
The centralized Subnet Manager can become a critical failure point; if it's compromised, the entire fabric is at risk.
Complexity & Deadlocks
Complex configurations can lead to vulnerabilities. Credit-based flow control can sometimes result in network deadlocks.