Introduction: The Shifting Battlefield
Security Paradigm Shift
Traditional perimeter-based security models are obsolete in the cloud-native AI era. Modern security requires a zero-trust approach with identity-centric controls and continuous verification.
Businesses grabbed the cloud. They seized AI. Why? Because these technologies deliver transformative power and blazing agility. But here's the problem: our mental models for security lag miles behind, stuck in an outdated, on-premises mindset where we meticulously design defenses for a world of physical servers and hardened network perimeters. The battlefield has fundamentally changed. Gone are the days of guarding physical assets. The new landscape operates on code, APIs, and identities—a logical and ephemeral world that demands we throw out the old playbook and think differently.
Are we defending castle walls while attackers teleport into the throne room?
This post explores five of the most surprising and counter-intuitive truths about modern cybersecurity, revealing how the very nature of risk has evolved in ways that defy traditional wisdom. Understanding these shifts isn't just helpful—it's the essential first step toward building a resilient defense for the era of cloud and AI, where everything moves faster, threats emerge from unexpected angles, and the old rules no longer apply.
The New Perimeter Isn't a Firewall; It's an Identity
Remember the castle and moat? That traditional security model focused on building a hardened network perimeter to keep attackers out, creating a clear boundary between trusted insiders and dangerous outsiders. In the modern cloud, that perimeter has dissolved completely. Infrastructure is inherently internet-facing. Resources get accessed via public APIs. The line between "inside" and "outside" blurs into irrelevance.
The new perimeter is your Identity and Access Management plane. Every user represents a potential gateway to your infrastructure. Every programmatic role opens a door. Every service account holds keys. This doesn't mean firewalls are useless—they still provide defense-in-depth through network segmentation and DDoS protection within a broader security model. But here's the truth: the primary attack surface is now the complex web of permissions these identities hold, and attackers know it.
Consider the 2019 Capital One breach. A stark example. A brutal lesson. The attacker's initial entry came through a common application vulnerability—nothing sophisticated, just standard exploitation. However, the catastrophic damage only became possible because they stole the temporary credentials for an over-privileged IAM role attached to the server, and that role held the keys to the kingdom, granting the attacker the permissions needed to exfiltrate the personal information of over 100 million individuals in one of the most damaging data breaches in financial services history.
Security Perimeter Evolution: Then vs Now
The shift from network-centric to identity-centric security models
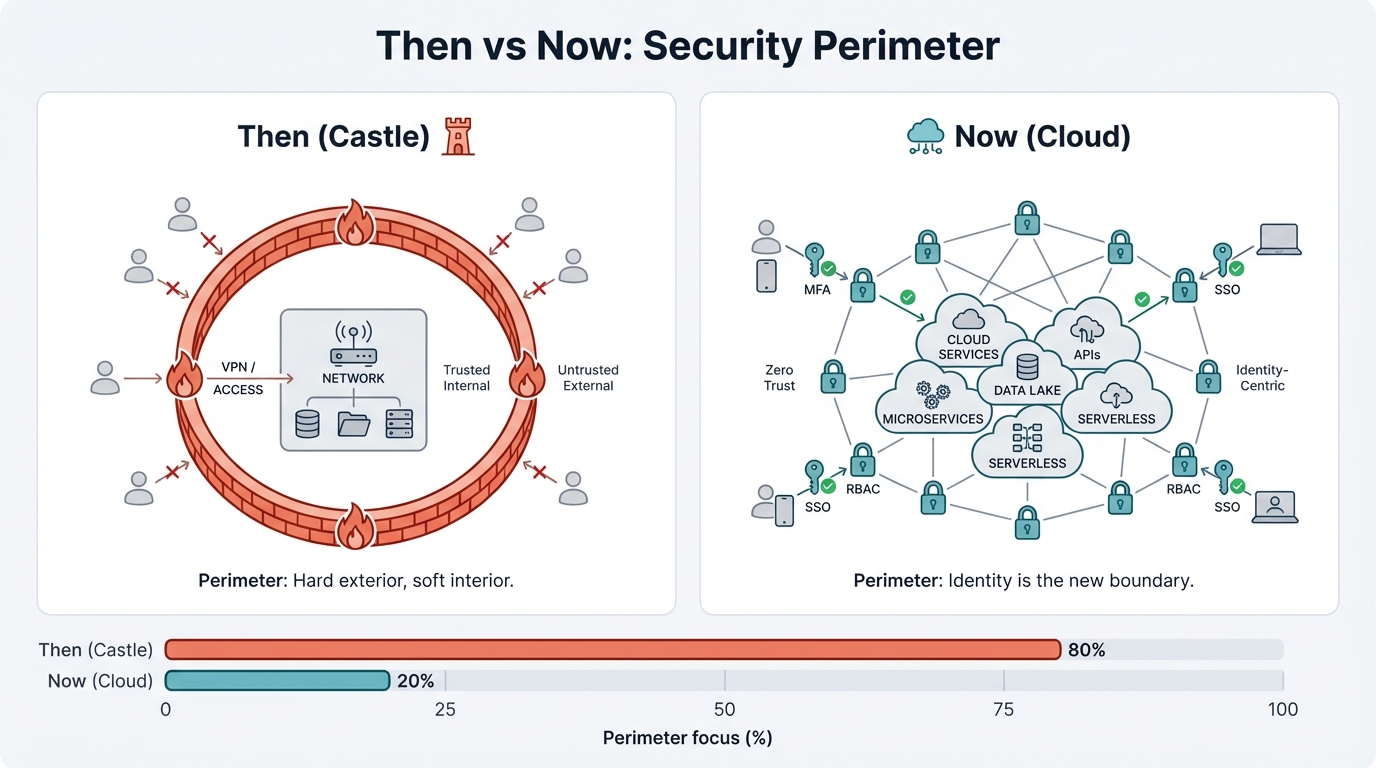
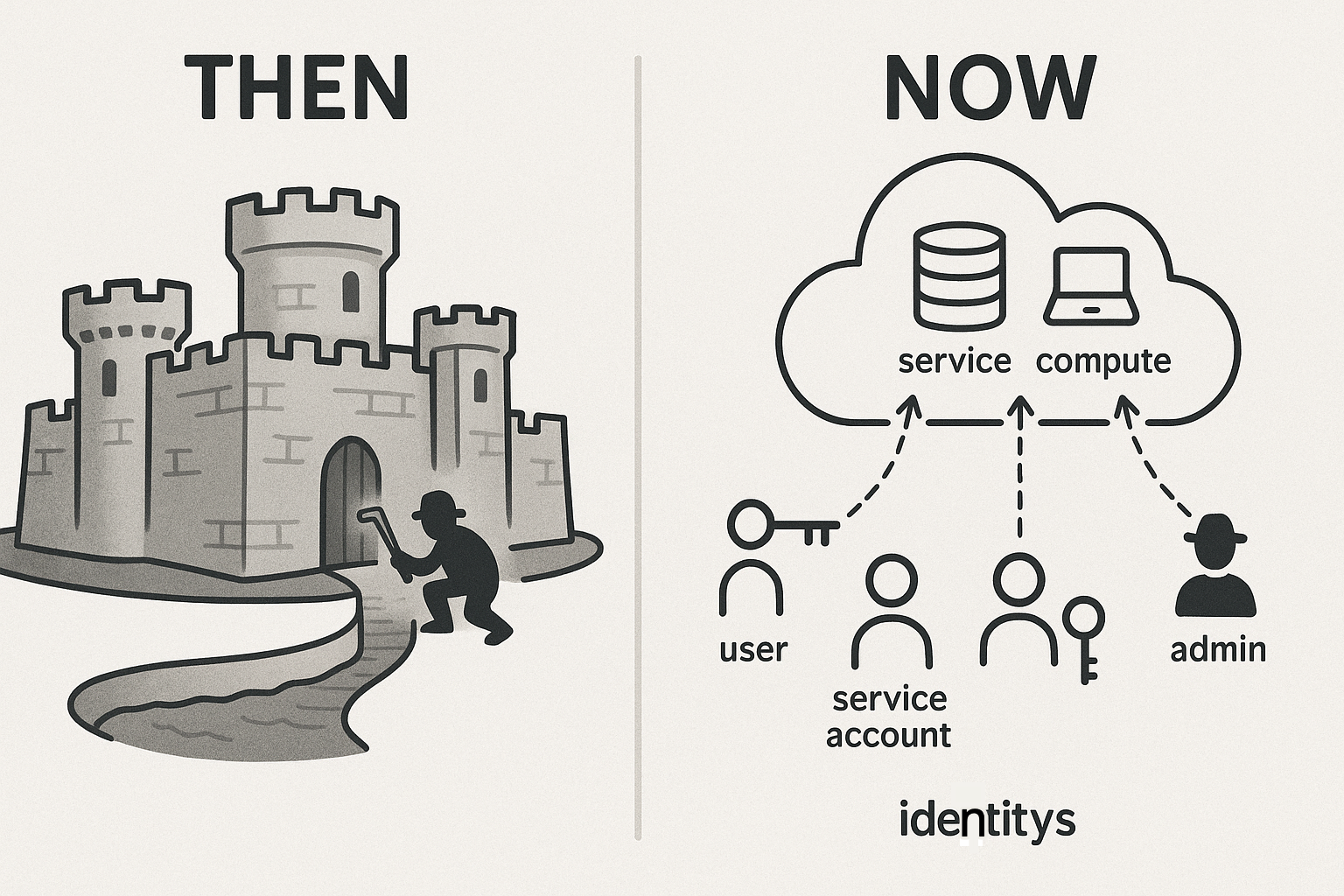
Left (Then - The Castle): Traditional network-centric security with firewalls as the primary perimeter defense.
Right (Now - The Cloud): Modern identity-centric security where IAM credentials are the new perimeter.
Attackers Aren't Using Malware; They're "Living Off the Cloud"
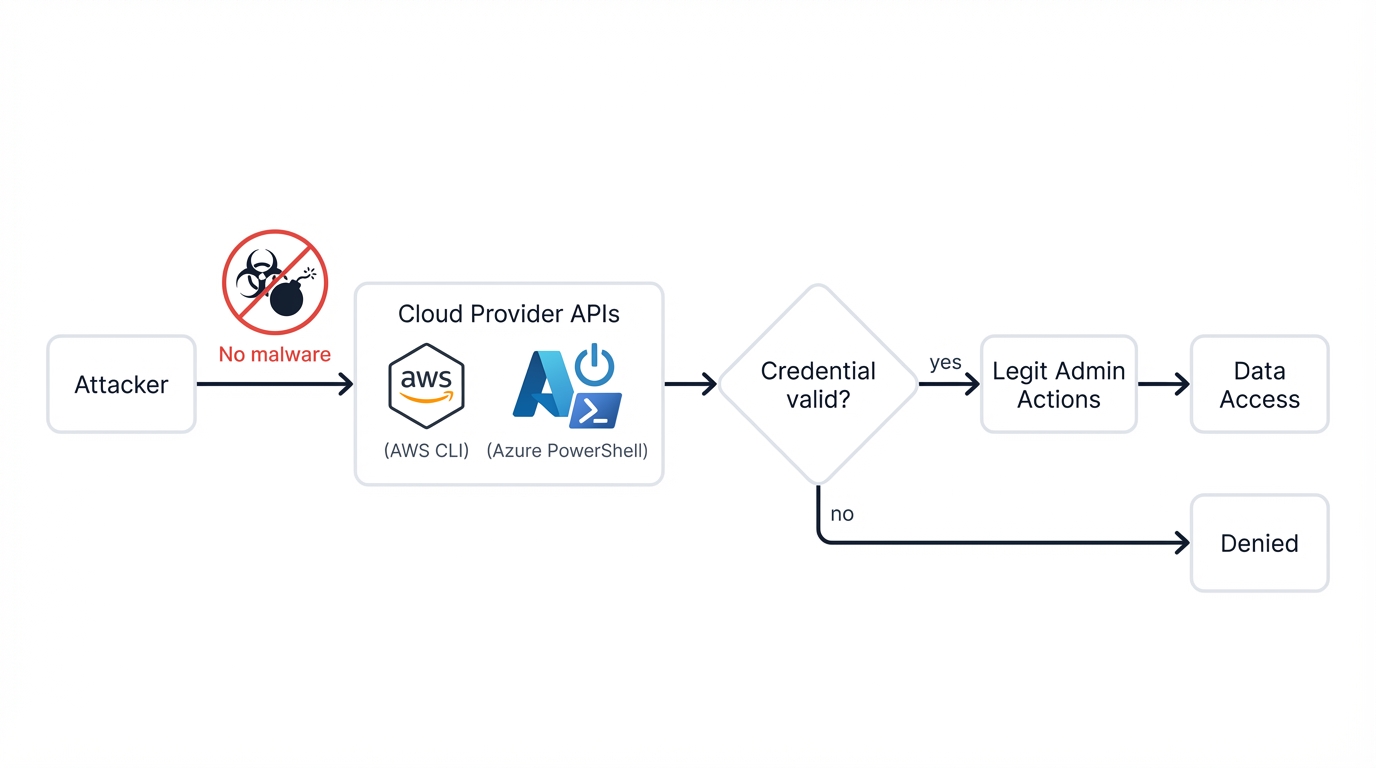
Most effective cloud attacks involve no malware at all. None. Instead of deploying custom malicious binaries that security tools can detect and block, adversaries are increasingly "living off the cloud" by using your own trusted infrastructure against you.
This technique abuses the cloud provider's own powerful, trusted, and well-documented APIs and tools—like the AWS Command Line Interface or Azure PowerShell—to conduct their operations with devastating efficiency. Why write malware when you can use official tools? Organizations inherently trust traffic to their own cloud provider's API endpoints. Traditional signature-based security tools are blind to the malicious intent behind a legitimate API call. Attackers use the same tools as DevOps teams, automating their actions and causing widespread damage with a few simple commands that look exactly like normal administrative activity until it's too late.
One Line of Code Can Instantly Create a Thousand Breaches
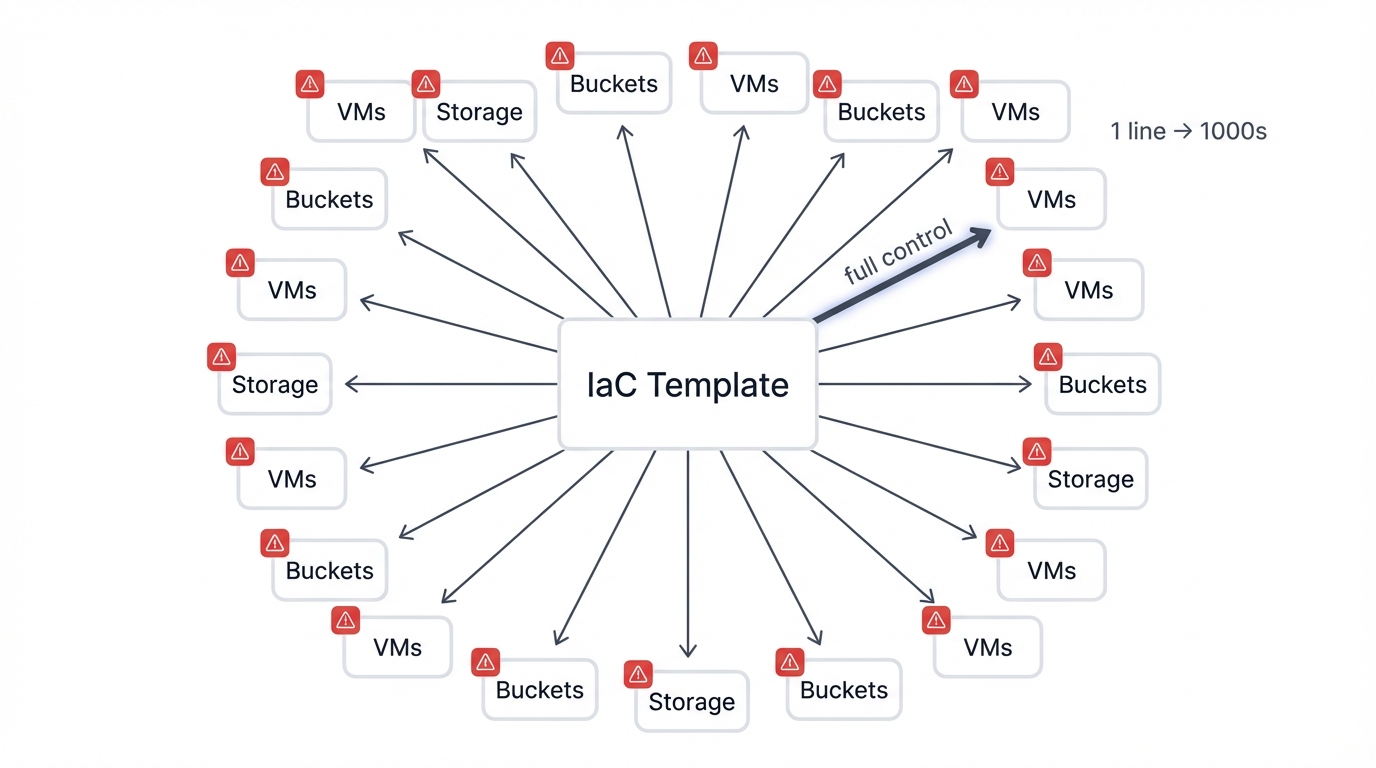
Infrastructure as Code is revolutionary. It's also a powerful amplifier of risk. In the IaC era, a single misconfigured line of code doesn't just create one vulnerability—it instantly creates a systemic, global vulnerability that replicates across your entire infrastructure at machine speed.
The 2023 Microsoft AI researcher data leak proves this brutally. Researchers used an Azure Shared Access Signature token to share AI models, but they misconfigured it with "full control" permissions over an entire storage account containing 38 terabytes of private data—internal secrets, private keys, thousands of Teams messages, all exposed by one wrong parameter. This single error in a shareable token, posted to a public GitHub repository where anyone could find it, exposed massive amounts of sensitive information. The blast radius of a single coded mistake is exponentially larger than a one-off manual error, because code doesn't make mistakes once—it replicates them thousands of times in milliseconds.
For AI, Your Security Tools Are Functionally Illiterate
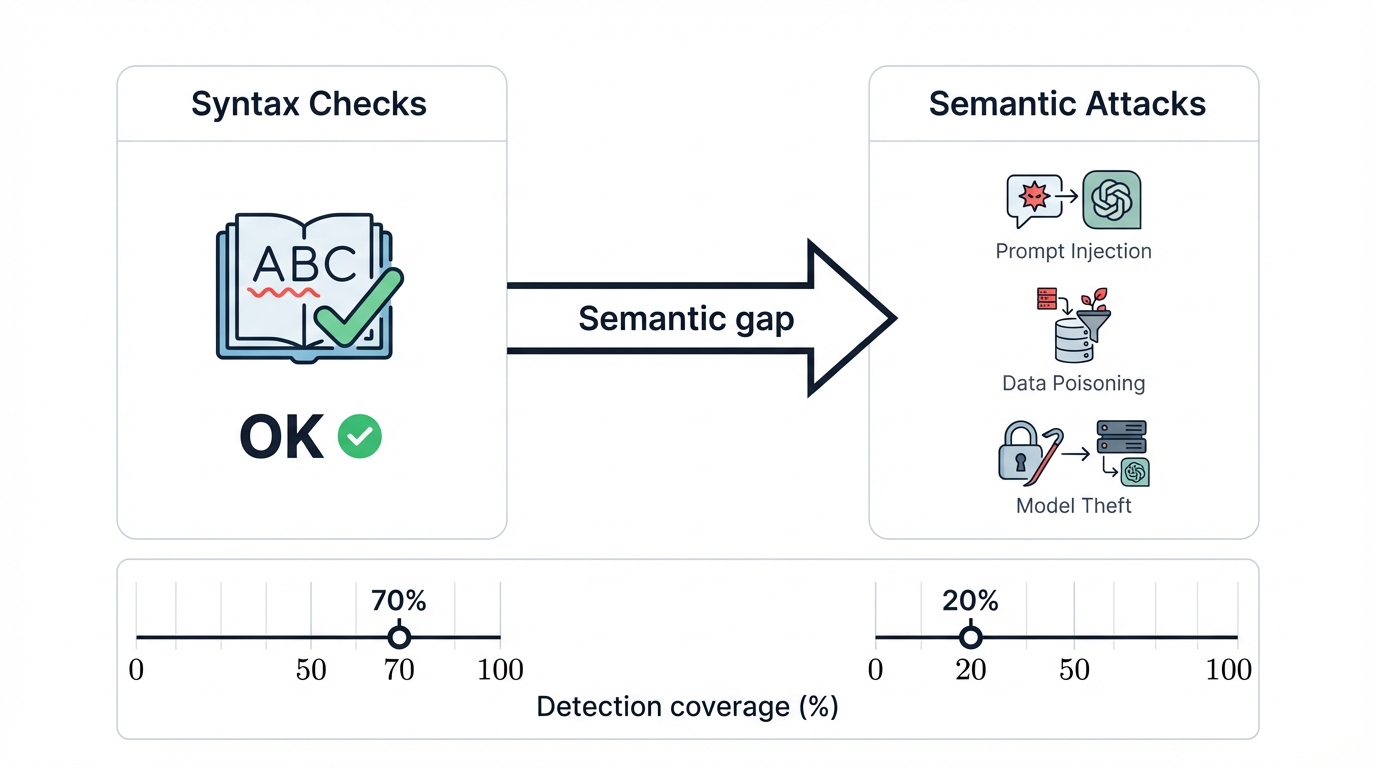
AI security reveals a profound "semantic gap." Your traditional security tools analyze syntax and structure. AI attacks operate on meaning and context. A prompt injection attack uses a perfectly well-formed sentence to manipulate an AI model's logic, causing it to bypass safety controls that look completely intact from a structural perspective.
This creates a fundamental mismatch between threat and defense. Your security tools are like spellcheckers—they can tell you if a sentence is grammatically valid, but they have absolutely no idea if it's telling a lie, manipulating logic, or subverting intended behavior through carefully crafted meaning. This represents just one example of a new class of threats targeting AI systems, which also includes data poisoning attacks that corrupt a model's training data to influence its behavior, and model theft operations that steal the proprietary model itself through careful extraction techniques. Defending against these semantic attacks requires a completely new approach that can understand context and meaning, not just syntax and structure.
In the Cloud, "Persistence" Means Owning an Identity, Not a Machine
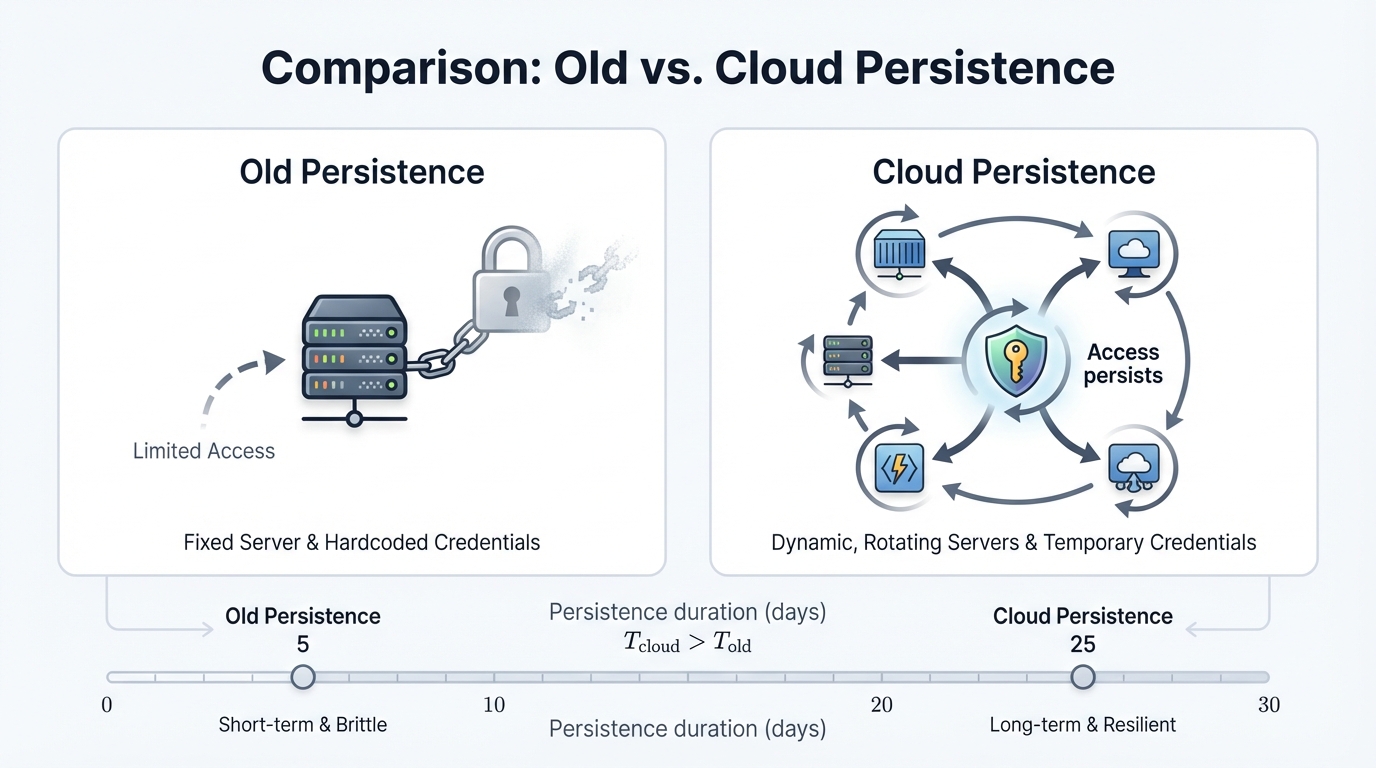
Traditional networks made "persistence" mean maintaining a foothold on a specific host. This model is obsolete in the cloud. Infrastructure is ephemeral. Servers spin up and down in seconds. Host-based persistence is an unreliable strategy that crumbles the moment infrastructure gets replaced.
In the cloud, persistence has evolved to mean maintaining access to the control plane itself, and the ultimate goal is not to own a server but to possess a compromised identity—like an AWS IAM role—that grants ongoing, programmatic access to everything that matters. With a persistent hold on a privileged identity, an attacker can access data across your infrastructure and re-establish a foothold on any new resource that gets deployed, no matter how many times you destroy and rebuild your servers. The persistence lives in the access, not the asset.
A New Mindset, A New Strategy: How to Adapt Your Defenses
Understanding these truths requires more than awareness. It demands action. We've moved from defending physical assets to securing logical, code-defined systems that evolve constantly and operate at machine speed. This new reality demands a fundamentally new strategy focused on identity, automation, and context rather than the network perimeters and signature-based detection that defined security for decades.
Here's how you can begin to adapt:
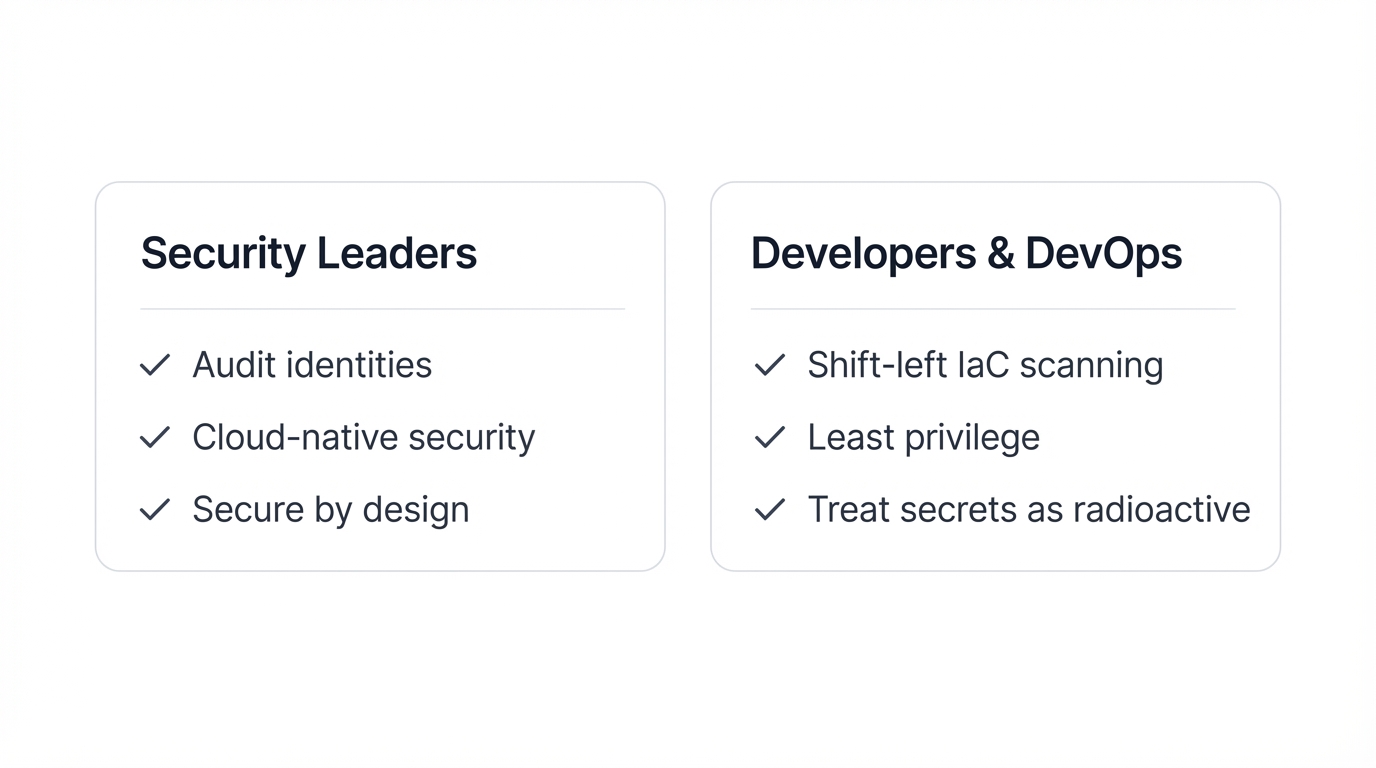
For Security Leaders:
- Audit Identities, Not Just Networks: Shift your team's focus from firewall rule reviews to rigorous, continuous audits of IAM policies. Who has access to what, and is it absolutely necessary?
- Invest in Cloud-Native Security: Prioritize tools built for the cloud, such as Cloud Security Posture Management (CSPM) and Cloud-Native Application Protection Platforms (CNAPP), which can detect misconfigurations and anomalous identity behavior.
- Champion a "Secure by Design" Culture: Security can no longer be a final checkpoint. Embed security expertise directly into development teams to ensure that what they build is secure from the start.
For Developers & DevOps Teams:
- "Shift Left" with IaC Scanning: Integrate automated security scanning directly into your CI/CD pipeline to catch misconfigurations in Terraform or CloudFormation files before they ever reach production.
- Embrace the Principle of Least Privilege (PoLP): When defining roles for applications and services, grant only the bare minimum permissions required for them to function. Never use wildcard permissions in production.
- Treat Secrets as Radioactive: Use dedicated secret management tools like AWS Secrets Manager or HashiCorp Vault. Never hardcode credentials, API keys, or tokens in code or configuration files.
Ready to Modernize Your Security Strategy?
Explore our comprehensive guides on AI security, cloud-native defense strategies, and identity-centric security models.
Example Implementation
# Example: Model training with security considerations
import numpy as np
from sklearn.model_selection import train_test_split
from sklearn.ensemble import RandomForestClassifier
def train_secure_model(X, y, validate_inputs=True):
"""Train model with input validation"""
if validate_inputs:
# Validate input data
assert X.shape[0] == y.shape[0], "Shape mismatch"
assert not np.isnan(X).any(), "NaN values detected"
# Split data securely
X_train, X_test, y_train, y_test = train_test_split(
X, y, test_size=0.2, random_state=42, stratify=y
)
# Train with secure parameters
model = RandomForestClassifier(
n_estimators=100,
max_depth=10, # Limit to prevent overfitting
random_state=42
)
model.fit(X_train, y_train)
score = model.score(X_test, y_test)
return model, score