Section 1: Why Every Security Team Runs on Python
Tool Security
Security tools can become attack vectors if you don't secure them properly. Lock them down with least privilege. Update them regularly. Don't let your defenses become doorways.
Walk into any Security Operations Center. Look at the screens.
You'll see Python everywhere. Penetration testers write in it. Malware analysts dissect threats with it. Incident responders automate with it. This isn't coincidence—it's evolution in action, and you're watching the survival of the fittest language for security work.
Python conquered cybersecurity because it solves the one problem every security professional faces: too many threats, never enough time, and adversaries who automate everything. When attackers launch automated campaigns hitting thousands of targets per hour, defenders need automation that's faster to build, easier to modify when attacks evolve, and powerful enough to process massive datasets looking for subtle indicators of compromise while simultaneously integrating with every security tool in your stack from SIEM platforms to firewalls to threat intelligence feeds.
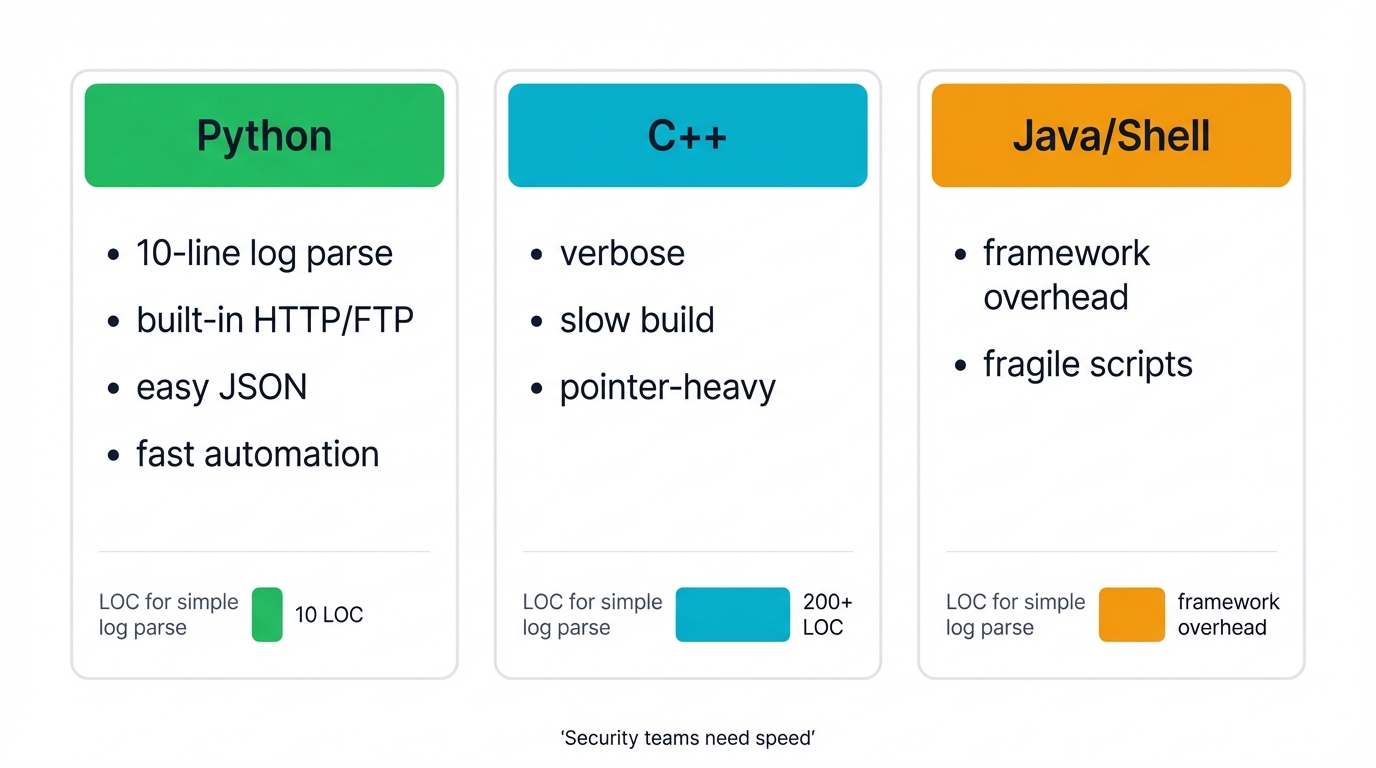
Why did Python win? Try building security tools in other languages and the answer becomes obvious. C++ demands hundreds of lines to parse a simple log file. Python does it in ten. Java requires complex frameworks for basic network operations. Python ships with everything built-in. Shell scripts break under edge cases that Python handles gracefully with proper exception handling and type checking.
The Security Professional's Reality Check: You need to write powerful tools in minutes, not months. You need to automate everything from network scans to malware analysis. You need to connect every security tool in your stack. You need to analyze massive datasets to find hidden threats. You need to build defenses that scale with attack volume.
Python delivers on all these needs. No overhead. No friction. Red teams use it. Blue teams use it. Even attackers use it. The universal language of cybersecurity.
"Batteries Included" - Why Python Ships Ready for Security Work
Security moves fast. Really fast.
New vulnerabilities drop daily. Attack techniques evolve hourly. Zero-days emerge from the shadows. You need tools that match this pace, and you need them yesterday when the incident response phone starts ringing at 3 AM because someone just detected unusual network traffic patterns suggesting data exfiltration and you have approximately ten minutes to determine whether this is a false positive or an active breach requiring immediate containment measures.
Here's reality: when you're responding to an active breach at 3 AM, you don't have time for complex syntax or obscure language features. Python's readable syntax means you solve security problems instead of deciphering your own code six months later. Watch the difference:
// C code to parse HTTP headers
char* header = malloc(1024);
if (strncmp(buffer, "GET", 3) == 0) {
// 50 lines of string manipulation...
}Versus this:
# Python code to parse HTTP headers
if request.startswith("GET"):
headers = dict(line.split(": ") for line in request.split("\n")[1:])Same functionality. One reads like English. One requires a PhD in pointer arithmetic. Guess which one gets the job done when ransomware is spreading through your network and every second counts toward containing the damage before it reaches critical systems?
The "Batteries Included" Philosophy Transforms Security Work: Python ships with everything you need. Parse gigabytes of log files? Built-in file I/O handles it. Test web applications? HTTP and FTP clients ready to use. Integrate with security APIs? JSON parsing works immediately. Hunt for attack patterns? Regular expressions built-in and powerful. Build custom protocols? Low-level networking accessible without complexity. Implement secure communications? Cryptographic functions standardized and reliable.
This foundation means you're not hunting dependencies or wrestling compatibility issues when time is critical and threats are active.
The WannaCry Reality Check: When WannaCry ransomware paralyzed hospitals, government agencies, and corporations worldwide in 2017, security teams faced immediate crisis: they needed custom detection scripts to identify infected systems and prevent further spread. Python teams had working WannaCry detectors running in production within hours. Teams using compiled languages spent days setting up development environments, managing dependencies, and debugging low-level implementation details. Meanwhile, the ransomware continued spreading, encrypting files, demanding ransom payments, and causing operational chaos that ultimately resulted in hundreds of millions of dollars in damages that could have been prevented with faster response capabilities.
The Security Library Goldmine (400,000+ Packages at Your Service)
Python's standard library is just the beginning. Just the opening act.
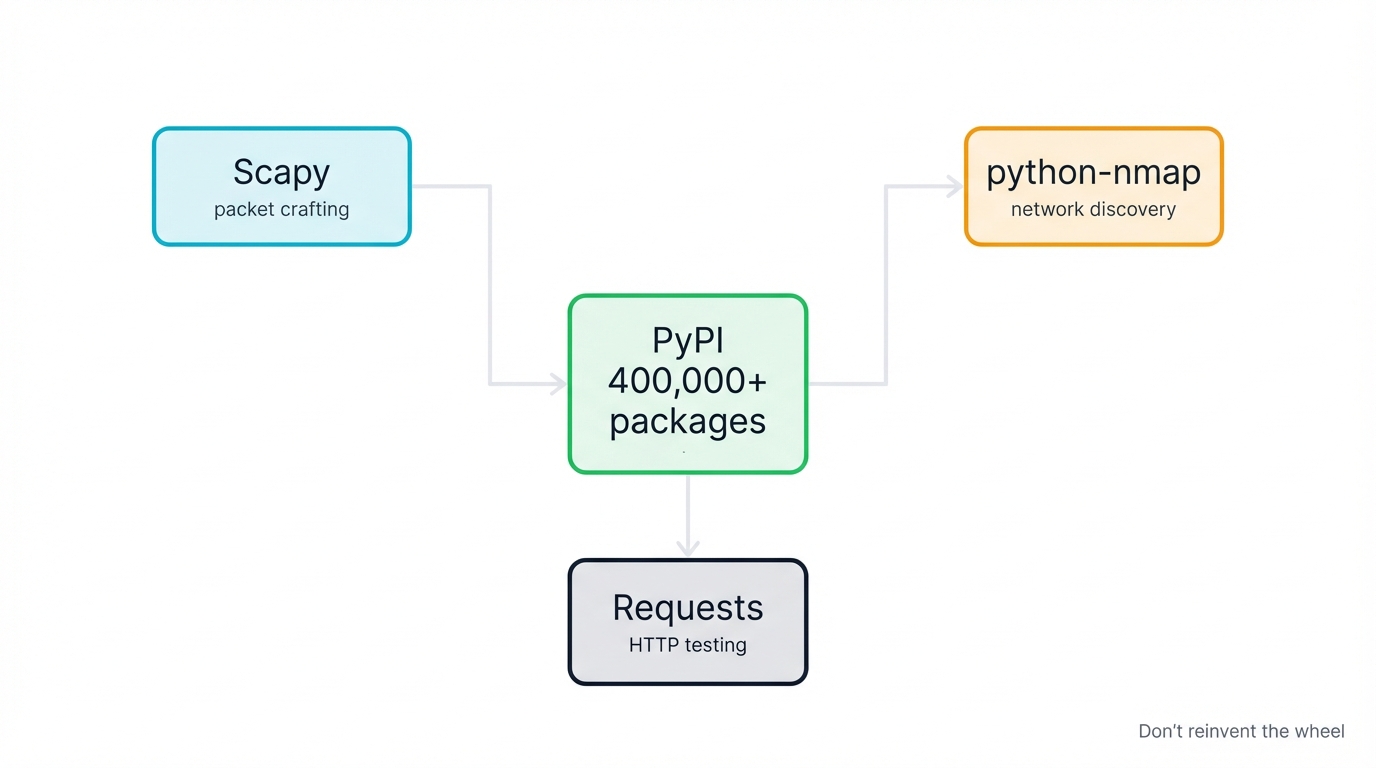
The Python Package Index (PyPI) contains over 400,000 packages, with thousands specifically crafted for security work. This creates a powerful force multiplier that changes how you approach security challenges: whatever problem you're facing right now, someone else encountered it, solved it, tested it in production environments, refined the solution based on real-world feedback, and shared it with the community so you can build on their work instead of starting from scratch.
You're not starting from scratch when building security tools—you're standing on the shoulders of a global community of security professionals who've refined these solutions through years of real-world usage, penetration tests, vulnerability research, incident response scenarios, and security operations center deployments across industries from finance to healthcare to government to technology.
The "Don't Reinvent the Wheel" Principle in Security: Consider the economics here. Every hour you spend rebuilding existing functionality is an hour not spent stopping actual threats. Why spend weeks building a network scanner from scratch when python-nmap provides production-ready scanning? Why risk implementing cryptographic functions when the cryptography library has been battle-tested by security experts and cryptographers worldwide?
The Essential Security Toolkit:
Scapy - The Swiss Army knife of network analysis
What it does: Craft, send, and analyze network packets at the byte level with surgical precision
Real use: "We found weird network attacks in our logs. Let me replicate those exact packets to understand what the attacker did and test our defenses against it." Scapy lets you forge any packet you can imagine. Indispensable for security testing and forensic analysis.
python-nmap - Network discovery on autopilot
What it does: Harness the power of the legendary Nmap network scanner through Python automation
Real use: "Scan our entire network infrastructure every night. Alert me immediately to any new services, unexpected open ports, or suspicious changes." This transforms manual reconnaissance into continuous automated security monitoring.
Requests - HTTP made simple
What it does: Handle HTTP requests and responses with elegant simplicity, making web application testing effortless
Real use: "Test 1000 web applications for common vulnerabilities like SQL injection and XSS without clicking through each one manually." Requests turns web application security testing from tedious manual work into automated precision testing that runs while you sleep.
Python as the Universal Remote Control for Security Tools
Your security stack includes dozens of tools. SIEM platforms collect logs. Vulnerability scanners identify weaknesses. Firewalls block threats. Threat intelligence feeds provide context. Ticketing systems track incidents.
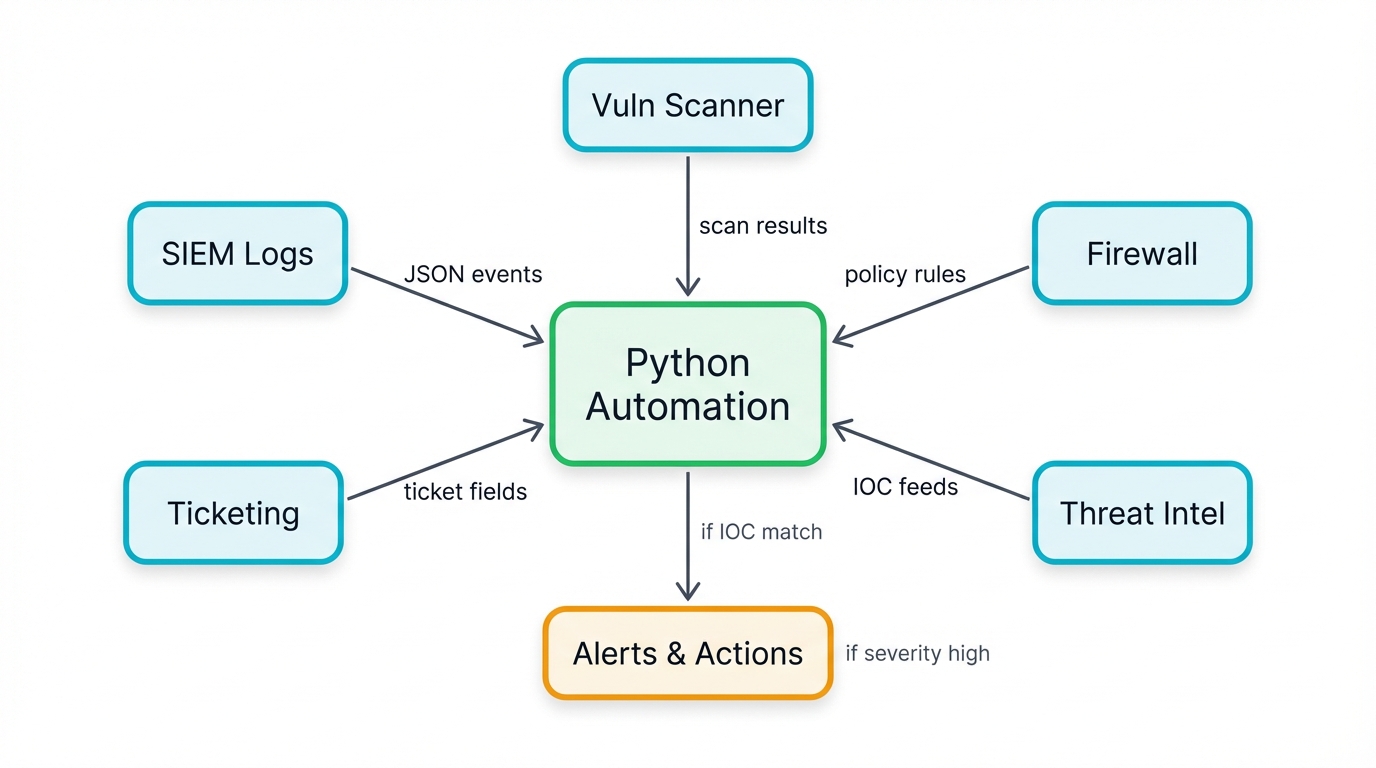
Each speaks a different language, uses different APIs, and expects different data formats. Python becomes the universal translator that makes them work together as a coordinated defense system instead of isolated tools that security analysts manually coordinate by copying data between systems and hoping nothing gets lost in translation.
The Automation Workflow That Actually Works:
# Real security automation pipeline
def incident_response_automation():
# 1. Network reconnaissance
scan_results = nmap.scan_network(suspicious_ip_range)
# 2. Vulnerability assessment
vulns = vulnerability_scanner.scan(scan_results.live_hosts)
# 3. Threat intelligence lookup
threat_data = threat_intel_api.lookup(scan_results.ips)
# 4. SIEM correlation
logs = siem.query_logs(time_window="last_24h", ips=scan_results.ips)
# 5. Automated response
if threat_data.severity == "HIGH":
firewall.block_ips(scan_results.ips)
ticket_system.create_incident(priority="urgent")
# 6. Executive report
report.generate_summary(vulns, threat_data, response_actions)This transformation is profound: what used to require a security analyst to manually coordinate between multiple systems for four hours now executes automatically in four minutes. The analyst shifts from being a data coordinator to a strategic threat hunter who focuses on understanding adversary tactics, techniques, and procedures instead of copying IP addresses between systems.
Your Python Security Cheat Sheet
Bookmark this table. These libraries solve 90% of security engineering problems:
| Library | What It Does | When You Use It |
|---|---|---|
| Scapy | Craft and analyze network packets | "I need to replicate this exact attack traffic" / "What's in these suspicious packets?" |
| python-nmap | Automate network scanning | "Scan our entire infrastructure for new vulnerabilities" |
| Requests | Interact with web APIs and services | "Test 1000 web apps for SQL injection" / "Pull threat intel from 12 different feeds" |
| Pwntools | Build binary exploits | "Prove this buffer overflow is exploitable" |
| pefile | Analyze Windows executables | "Is this .exe file malware?" |
| yara-python | Pattern-based malware detection | "Scan files for known malware signatures" |
| Volatility | Memory forensics | "What was running when the system got compromised?" |
| Pandas | Crunch massive datasets | "Find attack patterns in 10GB of logs" |
| Scikit-learn | Machine learning for security | "Build AI that detects never-before-seen attacks" |
| Cryptography | Secure encryption and hashing | "Encrypt data without creating vulnerabilities" |
Section 2: Red Team Tools - Python for Ethical Hacking
ETHICAL USE ONLY DISCLAIMER: This section covers tools and techniques for authorized security testing. Use only on systems you own or have explicit written permission to test. Unauthorized use is illegal and unethical. Don't be that person. Don't cross that line. The legal consequences include criminal charges, civil liability, and permanent damage to your professional reputation.
Python dominates penetration testing for one fundamental reason: it transforms complex attack techniques from PhD-level research projects into accessible, modifiable tools. The gap between understanding a vulnerability conceptually and proving it's exploitable in your specific environment? Python bridges it.
Automated Network Discovery - Finding What Defenders Missed
Before testing defenses, you need to understand what you're defending. Network reconnaissance reveals the critical gap between what IT documentation claims runs on the network and what's actually accessible to attackers.
This discrepancy often represents the most vulnerable aspects of an organization's security posture—forgotten development servers, misconfigured cloud instances, unauthorized shadow IT deployments, legacy systems that never got decommissioned, and services that someone installed for "temporary testing" three years ago and then forgot about completely.
Real-World Example: Automated Infrastructure Discovery
import nmap
import sys
def nmap_scan(target_host, port_range):
"""
Performs an Nmap scan on the specified host and port range.
"""
try:
nm = nmap.PortScanner()
except nmap.PortScannerError:
print('Nmap not found', sys.exc_info())
sys.exit(1)
except:
print("Unexpected error:", sys.exc_info())
sys.exit(1)
print(f'[*] Scanning {target_host} for ports {port_range}...')
nm.scan(target_host, port_range)
for host in nm.all_hosts():
print('----------------------------------------------------')
print(f'Host : {host} ({nm[host].hostname()})')
print(f'State : {nm[host].state()}')
for proto in nm[host].all_protocols():
print('----------')
print(f'Protocol : {proto}')
lport = list(nm[host][proto].keys())
lport.sort()
for port in lport:
port_info = nm[host][proto][port]
print(f"port : {port}\tstate : {port_info['state']}\tname : {port_info['name']}")
if __name__ == '__main__':
target = '127.0.0.1' # Target can be an IP or hostname
ports = '22-100' # Port range to scan
nmap_scan(target, ports)Packet Crafting and Network Manipulation with Scapy
For tasks requiring granular control over network traffic, Scapy represents a paradigm shift. From using tools. To crafting solutions.
Unlike Nmap, which provides comprehensive but standardized scanning capabilities, Scapy is a packet manipulation library that puts you in direct control of network communications at the byte level. You're not limited to what someone else designed—you can craft any packet structure imaginable, test any protocol behavior, and simulate any network condition from routine traffic to sophisticated attacks that combine multiple protocols in ways that defensive systems might not expect or properly handle.
Code Example: LAN Host Discovery with Scapy ARP Scan
from scapy.all import ARP, Ether, srp
def arp_scan(target_ip):
"""
Performs a network scan using ARP requests to discover live hosts.
target_ip: an IP address or a subnet (e.g., '192.168.1.1/24')
"""
print(f"[*] Scanning {target_ip} with ARP requests...")
# Create an ARP request packet
arp_request = ARP(pdst=target_ip)
# Create an Ethernet broadcast packet
broadcast = Ether(dst="ff:ff:ff:ff:ff:ff")
# Combine the Ethernet and ARP frames
arp_request_broadcast = broadcast / arp_request
# Send the packet and receive responses
answered_list = srp(arp_request_broadcast, timeout=2, verbose=False)[0]
clients_list = []
for element in answered_list:
client_dict = {"ip": element[1].psrc, "mac": element[1].hwsrc}
clients_list.append(client_dict)
return clients_list
if __name__ == '__main__':
# Replace with your network's IP range
network_to_scan = "192.168.1.1/24"
scan_result = arp_scan(network_to_scan)
print("Available devices in the network:")
print("IP" + " "*18+"MAC")
for client in scan_result:
print(f"{client['ip']:<20}{client['mac']}")Automating Credential Attacks: Password Cracking
Python's combination of intuitive file handling and robust hashing libraries creates an ideal platform for developing password attack tools that operate at scale. These automated attacks typically fall into two fundamental categories that attackers have used for decades but that Python makes dramatically more accessible and efficient.
Dictionary Attacks: This approach leverages human psychology and password patterns. People are predictable. They use common words, personal information, simple patterns. Dictionary attacks systematically test pre-compiled lists of likely passwords against targets, exploiting the reality that most users choose convenience over security and reuse passwords across multiple systems.
Brute-Force Attacks: This approach abandons assumptions about password content. It systematically generates every possible character combination up to a specified length, testing each one methodically until finding the correct password or exhausting the search space, which for long passwords with high entropy can take longer than the heat death of the universe but for short passwords with limited character sets can succeed within hours or days depending on available computational resources.
Code Example: Dictionary Attack on a Password-Protected ZIP File
import zipfile
import time
def crack_zip_password(zip_filepath, wordlist_filepath):
"""
Attempts to crack a password-protected ZIP file using a dictionary attack.
"""
try:
zip_file = zipfile.ZipFile(zip_filepath)
except zipfile.BadZipFile:
print(f"[!] Error: Could not open {zip_filepath}. Is it a valid ZIP file?")
return
try:
with open(wordlist_filepath, 'r', errors='ignore') as wordlist:
start_time = time.time()
password_count = 0
for line in wordlist:
password = line.strip()
password_count += 1
try:
# extractall requires the password to be in bytes
zip_file.extractall(pwd=password.encode('utf-8'))
end_time = time.time()
print(f"\n[+] Password found: {password}")
print(f"[*] Time taken: {end_time - start_time:.2f} seconds")
print(f"[*] Passwords tried: {password_count}")
return password
except (RuntimeError, zipfile.BadZipFile):
# This exception is raised for an incorrect password
continue
print(f"\n[-] Password not found in {wordlist_filepath}.")
print(f"[*] Total passwords tried: {password_count}")
except FileNotFoundError:
print(f"[!] Error: Wordlist file not found at {wordlist_filepath}")
if __name__ == '__main__':
# Replace with the path to your protected zip and wordlist
zip_path = 'protected.zip'
wordlist_path = 'wordlist.txt'
crack_zip_password(zip_path, wordlist_path)Section 3: Defensive Security, Forensics, and Threat Hunting
While Python demonstrates formidable capabilities in offensive security, its impact on defensive operations represents an even more fundamental transformation. Think about it.
The language's exceptional proficiency in processing massive datasets, automating complex analytical workflows, and integrating disparate security systems has made it indispensable for modern incident response, digital forensics, and proactive threat hunting that seeks adversaries before they achieve their objectives rather than responding reactively after damage has occurred.
Automated Log Analysis and Threat Detection
Modern enterprises face a data deluge. Millions of log entries daily.
Security devices generate millions of log entries daily documenting every network connection, authentication attempt, and policy decision. Servers record every transaction and error. Applications document every user interaction and system event. This volume creates what security professionals call "the haystack problem"—finding the needle of malicious activity buried in mountains of legitimate data where normal operations generate far more log entries than malicious activity and attackers deliberately hide their actions among routine traffic hoping defenders won't notice the subtle anomalies that indicate compromise.
Real-World Example: Parsing Apache Logs for Suspicious Activity
import re
from collections import Counter
def analyze_apache_logs(log_file_path):
"""
Parses an Apache log file to detect suspicious patterns.
"""
# Regex to capture IP, status code, and requested path from a common log format
log_pattern = re.compile(r'(\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}) - - .*? ".*?" (\d{3}).*')
ip_counter = Counter()
suspicious_ips = {}
print(f"[*] Analyzing log file: {log_file_path}")
try:
with open(log_file_path, 'r') as f:
for line in f:
match = log_pattern.match(line)
if match:
ip_address = match.group(1)
status_code = int(match.group(2))
# Track status codes per IP
if ip_address not in suspicious_ips:
suspicious_ips[ip_address] = {'401': 0, '404': 0}
if status_code == 401:
suspicious_ips[ip_address]['401'] += 1
elif status_code == 404:
suspicious_ips[ip_address]['404'] += 1
except FileNotFoundError:
print(f"[!] Error: Log file not found at {log_file_path}")
return
# Define thresholds for alerts
failed_login_threshold = 10
not_found_threshold = 20
print("\n--- Analysis Report ---")
for ip, counts in suspicious_ips.items():
if counts['401'] > failed_login_threshold:
print(f"⚠️ Potential brute-force from {ip}: {counts['401']} failed login attempts (401).")
if counts['404'] > not_found_threshold:
print(f"⚠️ Potential content discovery scan from {ip}: {counts['404']} not found errors (404).")
if __name__ == '__main__':
# Path to a sample Apache access log
log_path = 'access.log'
analyze_apache_logs(log_path)Malware Analysis Methodologies
Python has evolved into the backbone of modern malware analysis. It fundamentally changed how security teams approach understanding malicious code.
The language's versatility enables automation and enhancement of both static analysis (examining malware without execution to understand its design and capabilities before allowing it to run) and dynamic analysis (observing malware behavior during execution in controlled environments like sandboxes where it can't cause real damage but reveals its true intentions through observable actions like network connections, file modifications, registry changes, and process creation).
Static Analysis (Analysis without Execution)
Static analysis represents the first line of defense in malware analysis: understanding what malicious code is designed to do before allowing it to execute and potentially cause harm. This is detective work at the binary level.
Code Example: Basic Static Malware Triage
import pefile
import yara
import sys
def static_analysis(file_path, yara_rule_path):
"""
Performs basic static analysis on a PE file.
"""
print(f"--- Static Analysis for: {file_path} ---")
# --- PE File Analysis with pefile ---
try:
pe = pefile.PE(file_path)
print("\n[+] Imported DLLs:")
for entry in pe.DIRECTORY_ENTRY_IMPORT:
print(f" - {entry.dll.decode('utf-8')}")
except pefile.PEFormatError:
print("[!] Not a valid PE file. Skipping PE analysis.")
except Exception as e:
print(f"[!] An error occurred during PE analysis: {e}")
# --- YARA Scan with yara-python ---
try:
rules = yara.compile(filepath=yara_rule_path)
matches = rules.match(filepath=file_path)
print("\n[+] YARA Scan Results:")
if matches:
for match in matches:
print(f" - Rule Match: {match.rule}")
else:
print(" - No YARA rules matched.")
except yara.Error as e:
print(f"[!] YARA error: {e}")
except FileNotFoundError:
print(f"[!] YARA rule file not found: {yara_rule_path}")
if __name__ == '__main__':
if len(sys.argv) != 3:
print(f"Usage: python {sys.argv[0]} ")
sys.exit(1)
target_file = sys.argv[1]
yara_rules = sys.argv[2]
static_analysis(target_file, yara_rules) Section 4: Best Practices for Secure Python Development (The OWASP Framework)
Python is powerful for building security solutions. But it's also a language used to build applications that can themselves be vulnerable.
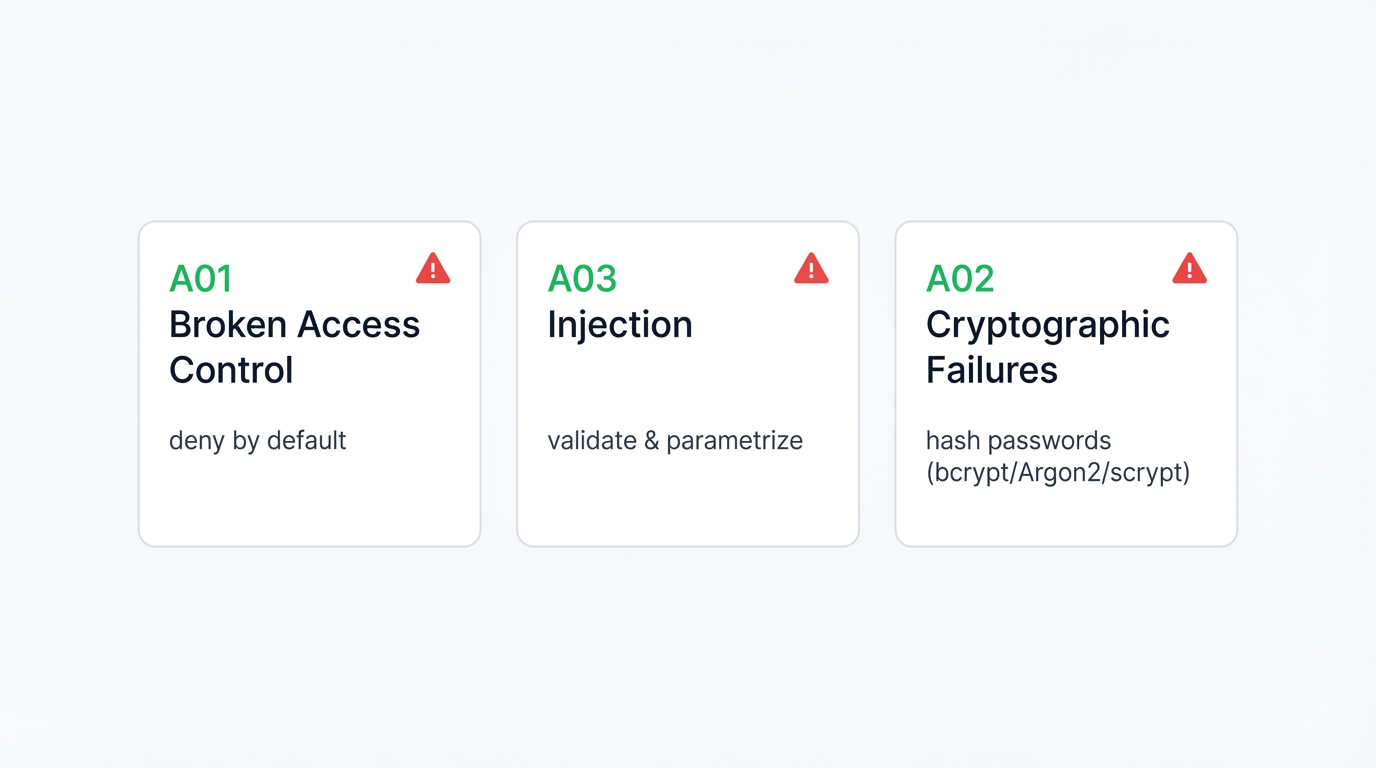
Writing secure code is paramount to prevent introducing new weaknesses into the systems you're trying to protect—imagine the irony of building security tools that themselves contain exploitable vulnerabilities that attackers can use to compromise the very defenses you're constructing. The Open Web Application Security Project (OWASP) Top 10 provides an industry-standard framework for understanding and mitigating the most critical web application security risks that affect millions of applications worldwide across every industry and technology stack.
A01:2021 - Broken Access Control
Broken access control refers to failures in enforcing policies that restrict users to their intended permissions. The result? Unauthorized data disclosure or modification.
The core principle for prevention is simple: deny by default and explicitly grant access based on a user's role and ownership of a resource. Never assume users will only access what they're supposed to access—enforce it at every layer of your application from the user interface to the API endpoints to the database queries themselves.
A03:2021 - Injection
Injection flaws occur when untrusted user input is sent to an interpreter as part of a command or query, leading to unintended execution. This is one of the most prevalent and dangerous vulnerability classes that has topped security lists for decades because it remains remarkably common despite being well-understood and easily preventable with proper coding practices.
The universal defense is simple: never trust user input and always validate, sanitize, and separate data from commands. Treat every piece of user input as potentially malicious until proven otherwise through rigorous validation that checks both format and content.
SQL Injection Prevention:
Insecure (f-string):
username = request.form['username']
# VULNERABLE: User input is directly inserted into the query string.
cursor.execute(f"SELECT * FROM users WHERE username = '{username}'")Secure (Parameterized Query):
username = request.form['username']
# SECURE: The database driver safely handles the user input.
cursor.execute("SELECT * FROM users WHERE username = %s", (username,))A02:2021 - Cryptographic Failures
This category addresses failures related to protecting data in transit and at rest. Most notably? The improper handling of passwords and sensitive information.
Passwords should never be stored in plaintext where anyone with database access can read them or where a breach immediately exposes every user credential. They must be hashed using a strong, slow, and salted hashing algorithm designed specifically for password storage like Argon2, bcrypt, or scrypt rather than fast cryptographic hash functions like SHA-256 that were designed for different purposes and can be brute-forced too quickly with modern hardware including GPUs and specialized ASIC chips that can test billions of password candidates per second against fast hash functions.
import argon2
# Hashing a new password
hashed_password = argon2.hash_password(b'my-super-secret-password')
# Verifying a password at login
if argon2.verify_password(hashed_password, b'my-super-secret-password'):
print("Password is valid.")
else:
print("Invalid password.")OWASP Vulnerability Mitigation in Python
| Vulnerability | Insecure Python Code Example | Secure Python Code Example |
|---|---|---|
| SQL Injection | cursor.execute(f"SELECT * FROM items WHERE owner = '{user_input}'") |
cursor.execute("SELECT * FROM items WHERE owner = %s", (user_input,)) |
| OS Command Injection | subprocess.run(f"ls {user_input}", shell=True) |
import shlex; subprocess.run(["ls", shlex.quote(user_input)]) |
| Cross-Site Scripting (XSS) | return f"<h1>Comment: {user_comment}</h1>" |
return render_template_string("<h1>Comment: {{ user_comment }}</h1>", user_comment=user_comment) |
| Insecure Deserialization | import pickle; user_object = pickle.loads(user_supplied_data) |
import json; user_data = json.loads(user_supplied_data) |
| Insecure Password Storage | import hashlib; hashed = hashlib.sha1(password.encode()).hexdigest() |
import bcrypt; hashed = bcrypt.hashpw(password.encode(), bcrypt.gensalt()) |
Section 5: Conclusion
Python's role in security engineering? Both profound and multifaceted.
Its inherent characteristics—simplicity, a vast standard library, and an unparalleled ecosystem of specialized third-party tools—have made it the dominant language for rapid prototyping and automation across the entire cybersecurity spectrum from offensive operations that identify vulnerabilities to defensive measures that detect and respond to threats to the secure development practices that prevent vulnerabilities from being introduced in the first place.
In offensive security, Python acts as a powerful abstraction layer that democratizes advanced techniques like low-level packet manipulation and binary exploit development. Libraries like Scapy and Pwntools lower the barrier to entry, enabling a wider range of professionals to build sophisticated assessment tools and simulate complex attacks without requiring years of specialized training in assembly language, network protocols, or operating system internals.
In defensive operations, Python has become the engine driving the modernization of the Security Operations Center where it serves as the critical "glue" that enables the orchestration of disparate security tools and the automation of time-consuming tasks like log analysis and malware triage that would otherwise consume all available analyst time leaving no capacity for proactive threat hunting or strategic security improvements. The convergence of Python's security ecosystem with its world-class data science libraries, such as Pandas and Scikit-learn, is fueling a paradigm shift towards data-driven security where machine learning models detect anomalies that human analysts might miss and predictive analytics identify attack patterns before they fully manifest.
The success of major Python-based frameworks like Volatility, Cuckoo Sandbox, and SQLMap highlights the power of its open-source, community-driven development model where thousands of security professionals worldwide contribute improvements, share techniques, and collaboratively advance the state of the art. Their extensible, plugin-based architectures have allowed them to evolve and remain at the forefront of their respective fields, profoundly impacting the practices of digital forensics, malware analysis, and penetration testing across organizations from small startups to Fortune 500 enterprises to government agencies responsible for national security.
Ultimately, as Python's integration into critical security workflows deepens and more organizations build their defensive capabilities around Python-based automation and analysis, the responsibility to write secure code becomes paramount—not just important, but existentially critical to the security ecosystem. The principles outlined by frameworks like the OWASP Top 10 are not abstract guidelines that you can safely ignore or defer to later phases of development but essential practices for any developer working in this domain where the tools you build to defend systems must not become the source of their compromise through ironic vulnerabilities that attackers exploit to turn your defenses against you. A mastery of Python for security engineering is therefore not just about leveraging its power for automation and analysis, but also about wielding that power responsibly, ensuring that the tools built to defend systems do not become the source of their compromise, and maintaining the trust that organizations place in security professionals who build the defenses protecting their most valuable assets from increasingly sophisticated adversaries who continuously evolve their tactics and techniques.
